What are the chances of an OpenWRT quick run-through video is made?
You should be able to block access by MAC address by specifying MAC Deny in the MAC address control advanced options under your DHCP service.
@wendell mentioned the OSI model. The reason you cant filter by MAC on the firewall is because the firewall works and filters on IP addresses at Layer 3 and above, where as MAC are at layer 2.
Using the MAC Deny option will prevent the machine from getting an IP address all together. So you have two options.
MAC Deny if you don't want the device to get an IP from your network at all.
Or DHCP static map and filter the IP on the firewall, give your internet network access but the device cant access the internet.
The second option (wendells) make more sense as if its plugged into your network you probably want it to have an IP address.
In both cases, it doesnt stop the machine from accessing the internet with a static IP that it assigned its self (but this usually required manual input).
I am trying to set up firewall rules for CS:GO. (On my VPN I actually have a better ping but crazy lagspikes (btw. why is that?).)
So I rerouted all outgoing ports 27000-27050 traffic over WAN gateway. This is my only firewall rule, rest is free to flow.
Game does not work anymore 
Steam does not connect(startup online) anymore.
How does one usually troubleshoot?
I recognized 443 traffic in the firewall log, so the game seems to contact the matchmaking servers.
...but I dont want to have all 443 on WAN... what do I do?
Thank you very much for the once again great video.
Thank you for addressing the Microsoft telemetry.
In that case you could create a separate interface for these devices and block certain access on that interface in general.
You could yes. Put them on another network, interface, or vlan and only allow them access to the internal networks.
Is there any way to dynamically update the MS telemetry list so that it remains current without user interaction?
EDIT: To some degree, I may have found my answer. There is a whole thread on this topic already so I'll suffice it to say that the below linked response shed some light on the easy way to do it in pFsense. However, the answer gets much more complicated when you read the entire thread. Seems that you'll likely be fighting a losing battle for now.
Didn't talk much about blacklisting vs whitelisting or how to approach putting together a firewall policy.
I know it would be confusing if you installed a new firewall and everything stopped working but in a lot of ways that is what I expect from a firewall. Everything closed except those ports that I have explicitly opened.
Is there an easy way to configure Pfsense to blacklist all ports and then add in the ones that are desired explicitly?
Post Removed: Forgive me, I'm still learning.
Firewall->Rules->LAN: Delete the "Default allow LAN to any" rule
Firewall->Rules->WAN: Add a "Block any to WAN rule"
@Whizdumb Floating rules are not above the LAN.Anti-Lockout Rule?
I do not understand how I again managed to lock myself out by enabling pfBlockerNG dnsbl.
That is how pfsense works by default, if you delete the default allow any to any rule then everything will be blocked. If you want to set up your firewall this way then make allow rules for the ports you want, and when you are absolutely sure it's set up properly delete the default allow any to any rule and the anti lockout rule, but if you mess you you're going to have to do a factory reset to get back in.
The rules are processed from top to bottom on first match, that means that as soon as traffic matches a rule no other rules take effect, so keep that in mind when setting up your firewall. Also remember that the firewall rules are for traffic entering an interface, so the source address is always something connected to that interface and the destination address is always something on a different interface or the interface address itself. So on the LAN for example there is no difference between setting the source to LAN network or any, they will both do the same thing, and the destination has to be something on the internet or on a different network, or the LAN interface address on pfsense, but it can't be another LAN address.
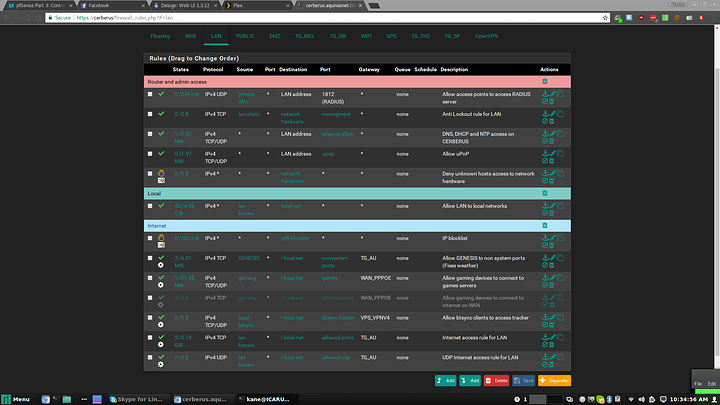
These are my LAN rules as an example of a firewall which is set up to block everything and only allow specific ports, although devices on my lan are less restricted than devices on the other networks.
This isn't needed as it's already the default action. You only need to make block (or deny) rules if there is an allow rule bellow it which would match the traffic. If there's no rule that matches then the default action of the firewall is to block.
Floating rules are complicated, but I'm pretty sure they are processed first, so they would be matched before the LAN anti-lockout rule. I tried a while ago using more floating rules rather than having similar rules on multiple interfaces and they appear to be matched from bottom to top in some cases and top to bottom in others and sometimes before or after the regular interface rules. So I gave up. Now I only use floating rules for match only rules because it's much easier to understand what's going on with regular rules.
Forgive the newb clarfication question, but now I'm totally confused. Are you saying that even after traffic matches a rule in the list, that the firewall continues to filter that rule down through the rest of the list to see if it matches?
For example: Say I create a rule that states: Block Any IP Outbound on port 80
Then I create a rule below that that states: Allow 192.168.1.1 Outbound on port 80
It will still allow the traffic through on 192.168.1.1 because it matches the second rule in the stack?
No, it's the opposite, the rule that matches first takes effect and all other rules are ignored. So order is very important. In your example you'd want to have the allow rule on top of the block rule so that it would allow 192.168.1.1 and block everything else. With the block rule on top then everything will be blocked including 192.168.1.1.
Do these 2 statements contradict themselves? What am I missing?
You only need to make block (or deny) rules if there is an allow rule bellow it which would match the traffic.
The rule that matches first takes effect and all other rules are ignored.
The rule that matches first takes effect, and the rules are read top to bottom. But there is an invisible block all rule at the bottom, which is the default action. So you don't need to make a block rule bellow an allow rule because there's already one there but you do need a block rule above an allow rule if you wanted to block some part of what the allow rule is allowing.
Ok so I think I get it now. That was a bit to wrap my head around but I definitely feel like I learned something about the fundamental workings of firewall rules and networking there. Thanks for the clarification.
No worries, it took me ages to get my head around it
Technically there is also UDP ping 
(regarding the statement that ping is ICMP in the video)
I'm having the same issue...