Hi, this is my first post and first topic on L1Techs forum (been watching Wendell since Tek Syndicate days).
So, I just recently made a pfSense router using an AsRock J3455M motherboard, 8 GB of RAM, 1x Quad Port HP NC365T (intel chipset) PCI-E x4 and 1x 1 Port Intel WGI210AT PCI-E x1. With the integrated Realtek port, I got a total of 6x 1Gb/s ports. I’m currently running it as host, but I’m thinking of virtualizing pfSense under Arch Linux and passthrough the Quad Port card to pfSense (I have experience with Arch, but not with KVM + QEMU, so noob on virtualization on Linux as well, except for VirtualBox).
I’m looking for things to learn for pfSense, so what should I first do? After I am initiated to it, I want to make an OpenVPN to force all traffic form other devices through my home network, but I also want to learn to setup a RADIUS auth (where I work, my Network Admin colleagues have setup RADIUS and OpenVPN, so I want to learn how to do that myself), not just use the integrated auth from OpenVPN. That’s where the Arch host would come in handy. I know it’s overkill for only 3 or 4 people (with 1 or 2 devices each at most) I would force through my home network, but I want to learn. Also, some documentations about VLANs would also be very welcome. By the way, I get free DynDNS from my ISP, because I pay for the best home contract they offer.
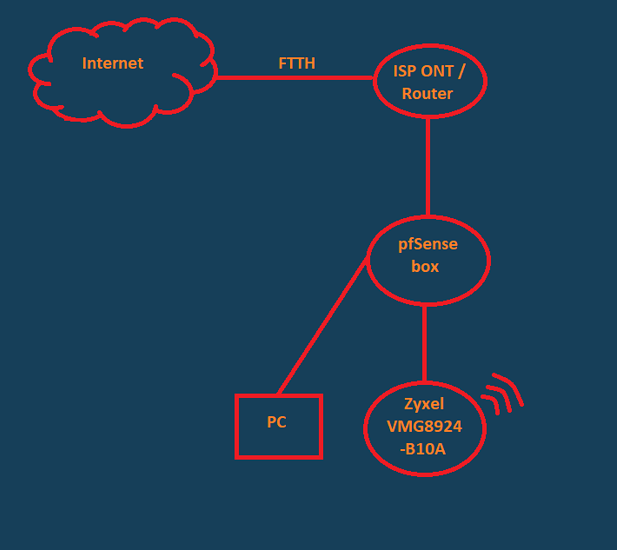
Lastly, I have some problems setting a Zyxel VMG8924-B10A into AP mode. I updated its firmware to latest version, I configured its WiFi, deactivated DHCP, set WAN into 5th LAN Port (and ended up still using one of the LAN ports instead, had some problems with the WAN port in bridge mode). If I connect my PC in any LAN port, I get internet connection and IP from the pfSense box, but if I connect any WiFi devices (my android phone), it connects, waits a few seconds, says “No internet access” and disconnects automatically, so I can’t use this router just as an AP, it has to be set into routing mode, not bridge mode. Also, I can’t access its web interface when it’s in bridge mode. Any tips on these ones?
Thanks for your patience with me. And if you are curious, here’s my home network map (sorry for my paint skills).