If it's set up correctly then all you need to do is make pass rules in the firewall, which you have. So I don't know why it's not working. Did you check that each network has its interface address as the default gateway and not the address of just the lan interface?
Have you checked that this isn't a problem with the firewalls running on the computers you're trying to access?
Yes and Yes... for a few seconds I saw my brothers PC and he couldn't see me. Then after a reboot of both our PCs and the pfSense box the reverse was true and now nothing again... Internet still works fine! I am kind of losing my marbles over this stuff.
With ping?
Be aware that nothing that relies on broadcast traffic will work over a routed network, which includes network discovery on Windows.
Yes, I meant ping at the time.
So, with great fiddling comes some results. First off, as a test, we were able to play Borderlands the Pre-Sequel now and it worked. I am able to view my camera system now but only if I input the IP and port manually. I have uPNP enabled and the uPNP port mapping works but the camera system is supposed to use uPNP for network discovery, by what the manual says, and that isn't working. For some reason, my brother was able to see my PC in windows and it DID work, able to download files and everything but I can't see him. This is intriguing to me because you say that network discovery on Windows should be completely borked. I tested accessing the printer and yes, that also works perfectly and after cycling it to get a new IP address from the DHCP server.
This whole time, I was using a ping test to see if traffic was going through so at least I wasn't expecting network discovery on Windows to just pop up. Though, for convenience sake, is there a way to make that work that you can think of? If not, that's ok, I may just play around with some cable routing and such to get our shit directly connected via one of the switches and keep the devices we want not to have access outside of that connection but that will be a little bit of a pain. I guess finishing up and fully implementing the file server might be the way to fully fix that. I haven't ever done that actually but I think I need to run a WINS server and then add that info to pfSense in the DHCP area? I think that is what I read somewhere. See, the research is slow going for me but I think I will get the hang of it soon enough.
In the end, I have a bridge with DHCP on the bridge, DHCP turned off on the normal networks and a CRAP load of random firewall rules my brother put in there that I would be surprised if even one of them were actually part of getting this to work. Still, I tried it this way yesterday and I have no idea why it is working out NOW whereas it did not work before. Unfortunately, they do all have the same IP range and such but I guess I could learn how to use a vLAN now. 
Either way, thank you so SO very much for sitting there and trying to help. I can't tell you how awesome it is to see there are still people out there who are willing to help out, especially someone who is as apparently clueless as I am. 
Well, for the moment, I think I am done with this chapter of the story. You may very well be seeing some posts from me later on as I start getting into some of the more advanced features. At this point, I think the first thing I need to do is learn how the traffic shaper works so I can get those roommates reigned in on their sheer idiotic amounts of internet bandwidth usage. I have a 1TB cap and now that Cox is going to start charging overage fees in my area, I can't keep letting a 3.5TB to 4TB a month usage keep on happening.
Thanks again my friend!
If you're using a bridge then you're better off just hooking everything to the same switch and having simply a WAN and LAN interface on pfsense. You shouldn't have to bridge it for it to work. If you create a bunch of interfaces and have allow any to any rules then all traffic should be able to route between interfaces, so I don't know why you're having such a hard time with it, it doesn't make sense.
upnp (by default) only makes WAN rules, so it won't help with inter network traffic unless you mess around with the upnp settings in pfsense, but it's unnecessary as you have allow rules anyway. If you want to avoid using an IP to connect to things then you need to make an entry in the DNS server for it.
There is no way to get broadcast traffic to work on a routed network, that's how it works and part of the point of subnetting. Just because network discovery won't work doesn't mean you can't access windows shares however, you just need to know the hostname or IP of the share you want to access.
If you haven't done anything weird to the pfsense configuration then I'd say a lot of the issues are on the devices themselves, because it's the sort of things which 'just works' as far as pfsense is concerned.
Yeah, I really didn't want to use a bridge but it was sort of a last-ditch effort to get something, anything to work. Honestly, the whole setup is less than ideal and so I will have to do some more deep thinking on how I wish to proceed. Likely, the best way is to just hook up my network to my brother's switch so that we can have proper Windows sharing a bit easier, at least till we get the file server finished.
Thanks for the tip on DNS, I knew this was the way to do it but since I only just got it working at all, I haven't even thought about using that yet. I will still keep the cameras and the printer plugged right into the pfSense box since it's not that hard to just set a static map for those devices so they always have the same IP. I mean, it's almost quicker and easier to just use the IP to configure them anyways, especially the printer since it is an old girl where auto detection itself in the driver can be flakey under the best circumstances. At least I can do what I need to do for the moment and will figure the rest out later.
Man, what an adventure this has been... 
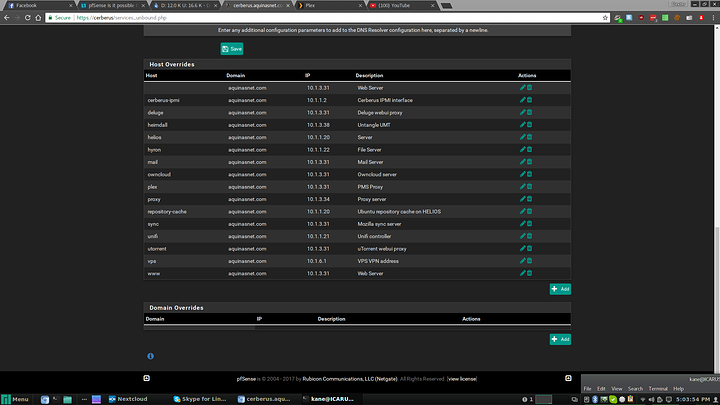
Assuming you have pfsense set as your DNS server then configuring static entries is easy. Go to the DNS resolver (or forwarder if you're using that but the resolver is the better choice) and go to the bottom of the page, then just add the entries.
COOL! Thanks for that. I will play around with this tomorrow. It's like 2AM here now and I am just fried. Looks like a good way to handle it, though.
It doesn't matter what your domain is, as you only need the first part. so you can set 'server.domain.local' to an IP then just connect to 'server' and it will resolve to that IP. Devices which get a DHCP lease should automatically have their host names added to the DNS server, so that should work by default so long as everything is working properly.
That's just beautiful! Thanks!
As a little bit of an update, I tried disabling all those crazy firewall rules my brother put in and local traffic stopped working. I did find a way to use a single rule to perform the same function, however. I made one floating firewall rule with a source and destination pointing to the bridge and BAM, it all just started working again. So the firewall rules I had in the first place that were supposed to be sufficient, simply are not. I wonder if a recent update changed things a little? Maybe I found a bug? Because this is my first pfSense install ever and you aren't the only person to say what I had should have worked. I will likely be doing that cable routing a bit and get this set up more sensically going forward.
I am probably going to get one of these for my brother's house, this is where the pfSense box and the internet itself are physically located. Plus, it also supports LACP so I can maybe instead, use all 4 ports as LAGG ports to increase bandwidth while keeping all of the other devices able to talk to one another broadcast style. I can then just put all of the roommates on a VLAN so they are isolated instead of a separate port on the pfSense box like it is right now. Since you are now my expert, do you think this is a good idea?
No, it won't work, what you are describing is kind of sort of a router on a stick configuration, except you're not doing any routing because it bridges, essentially the firewall won't do anything. You need to get rid of the bridge. It should work with separate interfaces each with its own network and you use pfsense to route between them and control access.
If for whatever reason you can't get that to work then just use a switch and have pfsense as the router between the switch and the internet. It will perform much better.
Yeah, I know, I will do it that way. I was just thinking of using the 4 ports together in a LAGG configuration since I have a new switch on the way that is managed and it has support for that in it' list of features, totally unrelated to the issues I had before. I was just wanting your take on configuring the network this way. It doesn't really matter much but curiosity gets the best of me sometimes. 
My original dilema will be sorted shortly anyways, soon as I have the time to fish some new cables where they need to be.
You can do it but it won't do anything, you're limited to the speed of your internet connection.
Silly me, I forgot about the switch. With the switch there the local traffic, the only traffic that would have any benefit by using a LAGG configuration would be behind the switch so none of that would be routed by pfSense. What was I thinking? 
Maybe if I plugged the server right into the pfSense box that might be worth it. I guess I wasn't thinking well enough.
Yeah, but in that case you may as well do the LAG between the server and the switch.
Good point.