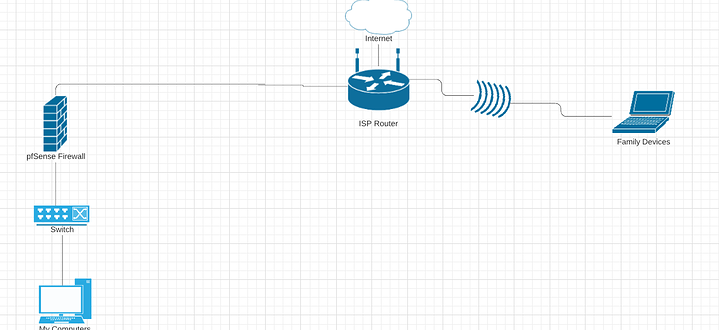
I installed pfsense on a computer that I want to put between my ISP router and a switch. If I want to just use it as a firewall how would I set it up? From my understanding I would need to disable DHCP and setup DHCP relay for the LAN right? Are there any other things I need to do so it works?
We use OPNsense, which is pretty similar (it’s a fork), but here’s a good video on pfSense. It’s long, but I think it’s worthwhile to understand thoroughly.
Why would you not bridge your ISP router?
I want to keep it separate from family devices so I don’t want it to do routing for everybody.
So, are you saying you want family devices on one network and your own stuff on another and for them to be separate and not talk to each other?
If it is, the way we did it is that we have a multi-port intel ethernet card on the firewall/router (OPNsense).
Port 0 goes to the ISP cable modem and is the WAN connection.
Port 1 goes to our local gigabit switch for our LAN; everything is wired. Address space is separate from the WIFI network (example: 192.168.0.1/24)
Port 2 goes to a WAP that our tablets and dad’s phone can connect to to get internet access. Also any visitors can (with a password) connect to it to get internet. This network has a separate address space from the LAN. (example: 192.168.1.1/24)
The firewall rules we set don’t allow communication between the WIFI network and our LAN.
If your family also has wired devices, you can connect a switch to Port 2 and connect the WAP to that switch, then they can have both WIFI and wired.
Our LAN has DNS and DHCP provided by a Synology NAS, but you could use whatever for that. The DNS forwards to the ISP.
The WIFI network has DHCP provided by OPNsense on that port (Port 2). It just provides DNS forwarding to the ISP and doesn’t see our LAN’s DNS.
@PhaseLockedLoop has a pretty interesting and comprehensive post about their network setup, which is a lot more than you’re looking for, but still really educational and I think will give you some context too. 
I keep all the family network traffic off my network and still get internet traffic to my network; all I had to do was connect my Netgate SG-5100 appliance to the family router and turn on the Netgate SG-5100 appliance. What surprised me was the SG-5100 appliance did all the basic configurations automatically. I will be writing a guide on accomplishing the goal @skada wants to fulfill as soon as I figure out the best default firewall rules and get my random thoughts into a concise and coherent format. When It is ready, I will post it at the following post.
This is what I am trying to set up basically. Kind of like a DMZ. PfSense between my computer and the ISP router. I want the ISP router as the DHCP and DNS server. I don’t really have a specific reason as to why I want to do this other than I just want to experiment with the pfSense firewall. Is this possible without having to do double NAT or having two separate networks?
Well, to do it like that you can have your pfSense not do NAT.
The easiest way this was done for me was segregating the ports off into subnets
LAN 1 was my next week 10.31.82.x IP6 7141 prefix
OPT 1 unused
OPT 2 10.31.83.x (government computer). IP6 7142 prefix
WG 10.31.84.x with IP6 LL and routed
Then all you have to do in the rules is make sure they don’t talk to each other (if you wish to isolate) and voila. Done routing for LAN and the other interfaces can all be done different with different router advertisements and not interfere with each other unless you designate specific routes
Thanks buffy for the share 
ISPs do give you subnets for this. You can play around with VLAN tagging there’s a lot of ways to do what you are asking.
Ahh I didn’t see this until I scrolled…
That’s interesting. Honestly I would have bought an AP and put it on the pfsense and bridge moded the modem but you can do it this mode.
Bridge the firewall so it’s firewal only no routing. Everything goes in it like a HOP. the firewall just determines what can get through that hop
I separated my network from the family network with a pi, using dnsmasq and forwarding ports, but it does not use pfsense/BSD, only linux.
The guide I used was below, but iirc, it’s basically just like subnetting, rather than some strong tunnel to an external endpoint
edit: I meant to paste the link to this: