So I have a pfSense router set up with PIA for full network VPN. I also have an OpenVPN server setup to access LAN resources from the WAN while also tunneling all traffic over PIA. Now I’m trying to set up a DMZ with a WebServer, with the idea being the DMZ will use the WAN not PIA and be able to access the DMZ from LAN. I can access DMZ from anything not on the LAN. I would like LAN traffic to flow to DMZ not the other direction. I have a DMZ rule set to reject any packets from DMZ to LAN, I have a feeling that’s not what I want to do, but I don’t know how to accomplish what I want. Since I’m doing PIA I have manual Outbound NAT, is there some NAT configuration I need to do? Also, if you need screenshots I can definitely provide them.
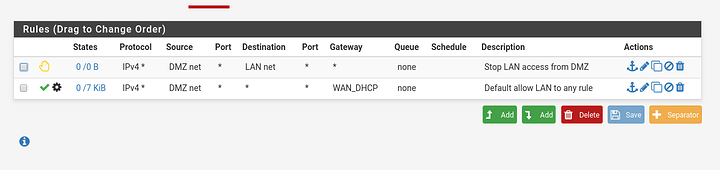
You just need a rule on the lan interface allowing traffic to the DMZ network and a reject rule on the DMZ interface to the lan network. Make sure this rule is above any allow to any rules you may have.
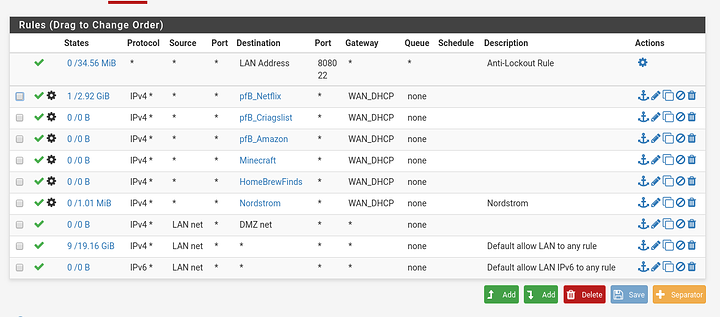
On the DMZ interface you will need a rule for Internet access, you can make an allow to any rule or what I like to do is make an alias with all of your local networks in it and then Create an allow to local rule (or whatever you name the alias) using the invert match check box. On that rule click on advanced and find the gateway option, set that to the wan gateway (or whatever gateway you want to use) and that’s pretty much all you need to do.
I created a OpenVPN server to DMZ rule and that works, if I connect to the OpenVPN server, I can access the DMZ and LAN, but no traffic from LAN to DMZ. Could the rejecting of all traffic from DMZ to LAN be the hindrance?
Put your LAN to DMZ rule above all the any to any rules. The firewall rules are processed top to bottom and first match so that lan to DMZ rule isn’t processed. Any rule for traffic between local networks needs to use the default gateway which is why those any to any rules aren’t allowing it.
Edit: just saw that those aren’t any to any rules but try it anyway.
So I fixed the issue, I think. I removed the LAN to DMZ rule since I have a LAN to any rule over the default gateway. I left the DMZ to LAN Block rule. Left the DMZ to any over WAN Gateway. And finally added outbound NAT to connect DMZ to WAN. Now I can access the DMZ internally and also connect to the Internet from the DMZ. I also allowed bogon networks on DMZ. It’s a little warm in the house so I haven’t fired up the server to see if I can access the website but I’m fairly certain I will be able to.
Those two options, to block private and bogon networks should onoy be enabled on Internet facing interfaces and never internal interfaces as it will cause problems passing traffic between local networks.