Have you tried rebooting pfsense at any point?
A few times but never with the VPN enabled and the single IP rules on. should i try that?
Yeah, sometimes the old states hang around after you update the firewall rules, rebooting will clear all the states. You could also just reset the state table without restarting pfsense, give either a try.
Other than that I'm really not sure, it could be a bug in 2.4 but I can't say.
it doesn't seem to like to bring up the VPN when i reboot. it might now like PureVPN i had a problem putting in the Private key in when i was setting up the Cert. i dont know if that is a problem considering its working. i am just trying VPNs right now to find a good one that doesn't slow down the system to much. if you have any recommendations for good VPN services i would appreciate it
Check the openvpn logs in the system log, that will tell you what the problem establishing the connection is.
I use torguard but purevpn should be good too.
You might want to consider your own Privet Virtual Server and install Open VPN on it. That is what I did and it works out better than messing with VPN providers at least for me.
i originally had OpenVPN setup on the Raspberry Pi itself and that worked just fine. i just wasnt vary fast and i have a VARY overpowered PFsense router so I've been playing with it to see what it can do
Dexter_Kane
do you run Torguard on your router or as a stand alone VPN server?
On the router. But anything which uses openvpn will work as well as anything else.
yeah i might have something wrong with the VPN i set up. i get huge spikes in latency for some reason.
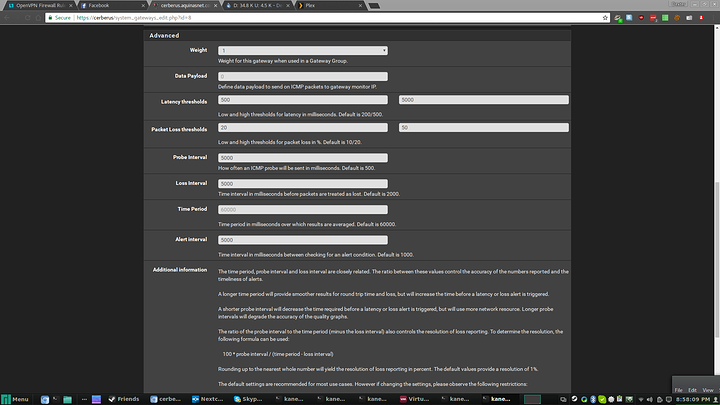
If you're getting high latency it could be causing the VPN to reset, it's part of pfsense's method of doing load balancing but it's not very useful for single connections. To fix it go to system>routing and edit the VPN gateway settings. Go to advanced and put in something like this, you may need to make them higher depending on how bad the latency/packet loss is.
ill defiantly try that! i think i am also going to try a few other VPNs to find what best works for me
Hey Guys I also have openvpn client setup with PIA, Firewall roles to control routes ECT works great, However if I do not pull routes from VPN then I have DNS Leaks! If I do pull routes then all my network Traffic will use VPN DNS but still route as intended however some websites check for this and as a result cause a lot of issues, any ideas thanks?
What do you mean by pull routes from VPN and what are DNS Leaks?
Pulling routes from VPN means getting all your traffic from VPN as in DNS requests and route info...A DNS leak means your IP address will show you in one country but your DNS requests will show your real location! (in my case its the reverse) Also your local DNS server may or may not record all your DNS traffic making the use of VPN mute.
It doesn't appear that you can specify an interface for the DNS server to use, even though the option exists. I started using an external DNS server so I'm not sure but at least at the time it seems there was an update to pfsense that caused all of the traffic from pfsense itself to use the default gateway regardless of what you told it to do.
Anyway, if you don't select the don't pull routes option then the VPN becomes the default gateway so if you don't want traffic to use the VPN you have to specify the WAN gateway in the firewall rule.
Thanks for the replay.
Sure 
Thanks Dexter_Kane that is the way I have it setup different gateway for rules but it still does what it likes lol
If there is a rule above it that matches then it will use that gateway, the traffic is affected by the first matching rule.
Yeah the traffic is fine routes as per rules it's the DNS requests that are the issue.. it appears Pfsense will only use one DNS server for all Gateways.