Don't spread the bullshit. Only interior affairs (that's police) and Megafon (telecom provider, it took out maybe a couple of their callcenters for a short time, no actual production equipment was affected) were reported.
Affected is affected.
I'm just basing this off the number of detections we saw from Russia thanks to people there I work with on this.
Kaspersky?
The amount of detections is high, that's true. But this "industry, infrastructure, power, hospitals"... [citation needed], I would say.
I bet russians not wanting to update their systems due to MS telemetry fears has nothing to do with:
Well...
Because of the scale of this hit, I think it has gone way beyond police kicking in doors. With national security concerns, someone is going to be getting a special visit from the spetznatz very soon, complete with breaching charges, flashbangs, and alot of agression. And they probably won't bother taking handcuffs with them for the raid. Sweet.
FUCK!
MS has issued emergency patches for unsupported versions of Windows.
Get your patch here if you need it.
http://www.catalog.update.microsoft.com/Search.aspx?q=KB4012598
Covers
- Windows Server 2003 -> 2008
- Windows XP -> Windows 8
- Windows POSReady and WES09
Detailed thread here:
https://forum.level1techs.com/t/wanacry-factsheet-continuously-updated-and-patches-for-legacy-windows?source_topic_id=115827I don't know if someone already posted this here, but the spreading of the worm has been (accidentally) stopped now. A security researcher found out that the worm attempts contacting a certain previously unregistered domain. If the domain isn't registered it will attempt spreading to other machines, while it won't do that if it is able to contact the domain. He said this looks like a kill-switch the creator put in place to stop the worm.
Nonetheless, no one stops people from creating a version 2.0 of this worm without the kill-switch that uses the same vulnerability, so patching is a must.
Yip that is correct. The exploit fully multi purpose. Anyone could reuse the same bin with a different payload.
You could even use the exploit to distribute KB4012598 patches. #WanaPatch 
See my above post for the detailed thread, all the info is on a wiki gist updated as more comes in.
I don't get how this virus initially gets into a system. I understand once it's in a system how it can affect and spread to others but how does it get onto say a regular desktop to begin with?
Looks like it was an email attachment first. After it was loose there was no stopping it because I just became a probing worm looking for any box with the same vulnerability it used in the first place.
The NHS were saying it hit their email servers first and spread from there.
It looks like unintentional, though probably welcomed on the hackers part, rapid spreading of the worm once it was loose. Basically, shit is way to networked and it should not be. It started somewhere small enough but exploded and worked every last connection it could to propagate as fast and wide as possible.
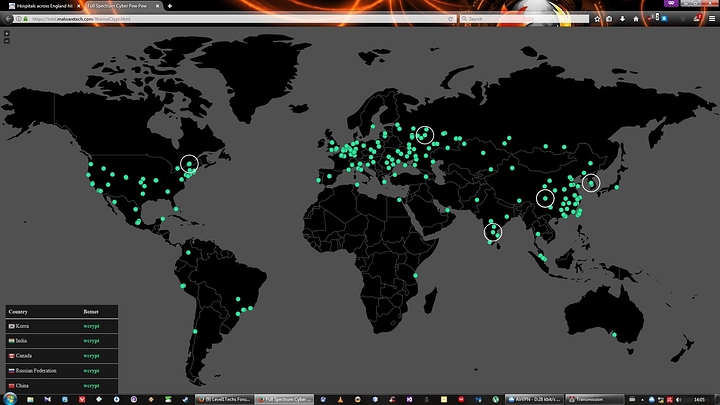
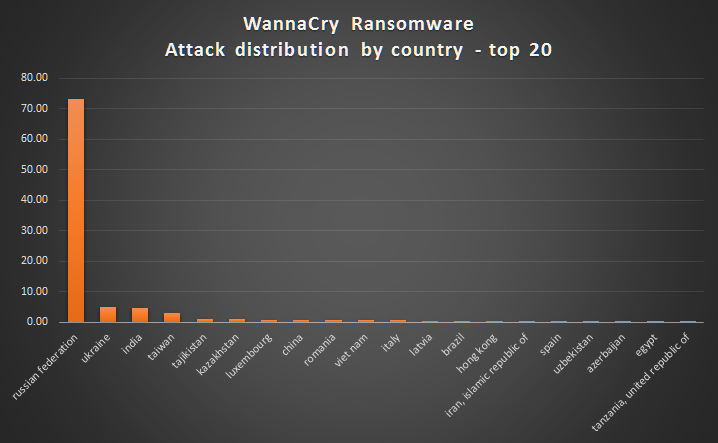
75000 infection across 99 different countries. Wow this is big. Just wait for the shitstorm on Monday morning.
That number is on the low side. Map too.
How, how did Ireland avoid this mess so far. Our IT is universally out of date and shit. all systems are at least as bad as the UK, most times worse.
The mind boggles. I give it till monday. We love to make out everything is fine when it is not.
I think it only shows the new infections from the moment you load the website. Right now there is one infection in Ireland too.
Things that just won't click with me:
MS17-010 wasn't released in the first wave of "we fixed the exploits we didn't knew about" for winXP/Server2003 .After Shit hits the fan hard as fuck, it was released for winXP and Server 2003.
Hospitals and Banks and Train Stations, general infrastructure is STILL running winXP AND HASNT BEEN PATCHED FOR A MONTH!
If you virtualize a winXP system or even use WINE you are still vulnerable.
Madness & insanity. Once a month,
That is better. I wonder who it hit here. No doubt the response will be glacier pace and as effective as a damp flannel on a house fire. On top of that we love inter communication, so who ever has it will not say a word to anyone connected to them and let it spread while fruitlessly trying to stop the infection on their own network first.
For having Intel fabs based here along with many other large tech companies we are woeful bad at IT security or efficiency. PCs to us are still leprechaun magic from the colonies. I hope for the worst. This country deserves nothing less.
You make me laugh. I'm furiously updating all computers at our house while struggling to activate one Windows 7 copy.
Doing the same.