Hi everyone, I’m new here but have been lurking and watching for quite a long time. A few years ago I built a Pfsense router after watching a bunch of stuff about them and realizing that as time goes by I’m going to need to learn more about this stuff anyways. So I built my device and though it was a bit of a pain to get setup for the first time, it was awesome! I love it and it worked great giving me the tools to learn more over time.
So I had cable and that was great. ISP → Modem → Pfsense. Done. Simple.
Then I moved.
First Problem.
Now I have DSL and its my only option in the new place. I spent some time trying to get the gateway router modem combo thing to bridge and trying to setup my Pfsense box to talk to no avail. I have done a ton searching to see what I am doing wrong but it doesn’t seem to have worked out. I am going to try again soon but its though because I can only have the network down for a few hours in a row or the family starts to get pretty upset. I have a few of what I think are stupid noob questions but thought I would toss them out here and see if there are some ideas from you guys. Just trying to learn more.
1, Pfsense box and ISP supplied router have the same login of 192.168.1.1. If the ISP router is going to be set to bridged mode, should I still change the address of my Pfsense box so they don’t interfere?
2, Is the MTU the same for all ISP’s or do I need to call them and get that information?
3, Is there a simple walkthrough somewhere that I haven’t been able to find that may point out something that I have missed or can check against? My google-fu has failed me on this.
So that’s where I’m at for Stage 1.
Stage 2
Replacing my access point. I have an older Ubiquiti AC lite and it has been good, but I have just received my new Ubiquiti 6 lite and learned what PoE+ is first hand! So because the PoE injector for the AC lite is 24v passive wont work for powering the 6, I was thinking that it is time to get a new switch that has PoE to run it. I was thinking that I should use the old ac lite to have a different wireless network that I can put all of my IoT stuff on. So I have come up with a network diagram for what I think makes sense. Paint for the win! Please tell me if I’m being dumb in the setup of this. I am by no means a network specialist!
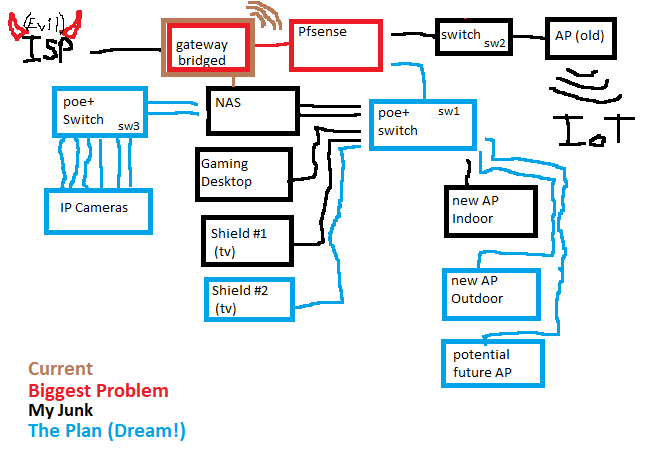
So a few things I need help with in this respect are,
1, Should I get a PoE+ switch instead of an injector? The only switch I have right now is an $8 5 port.
2, Should I get a managed switch? I don’t have a guest WLAN or second network for the IoT things yet but I would like too. I have a 4 port NIC in my Pfsense box, but have used only 2 ports until now.
3, For a bit of extra money, a downgrade in specs, and it is currently out of stock, Should I wait and get a Ubiquiti Switch Lite 8 PoE so that I can manage it with Unifi?
4, If not the 8 lite, What would you recommend? TP-link, Netgear, Cisco scares me because of the $$$, something else?
5, 8 port?
I think these are what I need to really start with and then I can try and get everything setup before I start to worry about future expansions into camera network, or the old server that I got from work that I would like to load TrueNas or Unraid on and try and learn about. ( I chickened out and got my Synology but really would like to learn how to do my own NAS)
I’m sorry if these are dumb, over asked, silly questions. I’m not trying to waste anyone’s time, and I feel dumb for not being able to figure it out but I thought I would ask since you guys sure as hell know what you are doing and I’m trying to learn.
Thanks in advance!

 I believe that you stopped speaking english somewhere in this but I can’t figure out where… lol. Should I ask my ISP what they use?
I believe that you stopped speaking english somewhere in this but I can’t figure out where… lol. Should I ask my ISP what they use?