It is on my planned list of routers to get. Some people collect Base Ball cards others collect stamps. I collect routers and switches, and servers.
I stumbled over this and it looks fairly interesting but at the moment it is too expensive for my taste.
Yeah, I plan to have the odd VLAN, but I have not planned anything concrete yet. (Currently, there are only devices in the network which should be on the same VLAN, but this will change in the future)
In regards to your recommendation, would this PC be good enough?
That is basically my idea. I don’t really know what I want to have or what I want to have running on my firewall because I have not used one yet. If it ends up crippling the performance I will just turn it off again.
True that, it becomes difficult to avoid doing something like that if you are really invested into something. (Which is also exacerbated by the fact that you probably have seen quite a lot and therefore want to be on the safe side.)
Different opinions and suggestions are always welcome ![]()
I know that, on the other hand pfSense or opnSense are more powerful than the Unifi controller. Furthermore, the USG is currently out of stock and it seems like they will also become deprecated and be entirely replaced by Dream Machines.
What is the general opinion of this particular device:
You might want to look up aftermarket support (BIOS etc) and I would think twice about both the CPU and Realtek NICs.
If that doesn’t bother you the UP Squared V2 boards might be of interest.
What the issue with the CPU?
Are Realtek NICs really that bad? I mean maybe a Realtek NIC won’t handle GbE, but it should come very close? I’m asking because most NICs are Realtek as far as I can tell and I think driver support in OPNsense and pfSense probably has improved, hasn’t it?
Realtek NICs are bad in general (but they’re cheap) so your milage may vary, I haven’t touched Realtek NICs in FreeBSD for years and just gone with Intel because it works ™. That’s what also Netgate recommends looking at Hardware | pfSense Documentation . Other brands such as Chelsio are also well regarded by that’s another tier…
Realtek is not great, but common enough to probably work.
ASIX is really bad (and dirt cheap).
Intel, Mellanox, etc. are the good ones.
I find it kinda overkill, but for the price ($134), it’s a steal! I think you can go for it. What I’m afraid though is that it may have Realtek NICs, which is… fine, they work, but I tend to avoid them, because many times, they do not have drivers in BSDs, or they have wanky bugs that make them stop working or have their performance plummet after a certain period or a certain number of packets. All kinds of crazy stuff.
But on my Asrock J3455M, I did use the Realtek in-build NIC as a WAN and it worked fine, while using the PCI-E HP 4x Gigabit Ports Intel chipset card for my LAN. I was running pfSense and got that chip because it had AES-NI, at the time when pfSense was saying that 2.5 will have a hard requirement on it (I started with 2.4). It never actually happened and it took a long time before I realized my OpenVPN was not even using AES-Ni, it was using the CPU and was working flawlessly. Later on, I did enable it in the settings, but I wasn’t aware it was a opt-in toggle. Basically free performance for encryption stuff, you do stuff at the cost of less power.
They might be charging an arm and a leg for the that, just because it’s a rack mounted low power Atom (which the Celeron also technically is, the Gemini Lake is the Atom core lineup - but don’t get me wrong, those things can trade blows with old i3s and keep up with old i5s at only 1/10th of the power consumption).
They should, just that depending on what you get, you may have weird bugs, like mentioned above, or not work at all because of complete lack of drivers.
I’m quite sure that you since several years back don’t need to do anything to OpenVPN for it to utilize AES-NI (or any other CPU related crypto extension that OpenSSL supports). That being said, it doesn’t do that much as data switching between kernel and userland is much more CPU intensive. There is however work done in FreeBSD -CURRENT (HEAD) adding DCO support, src - FreeBSD source tree
In general though you’re likely to see Wireguard to perform better and it’s quicker to setup. OpenVPN does have a few tricks though that Wireguard doesn’t have especially when it comes to routing.
Looking that the comments it appears that you need to use the out of tree driver so you’re at the mercy of how much Realtek cares about their legacy or soon to be controllers.
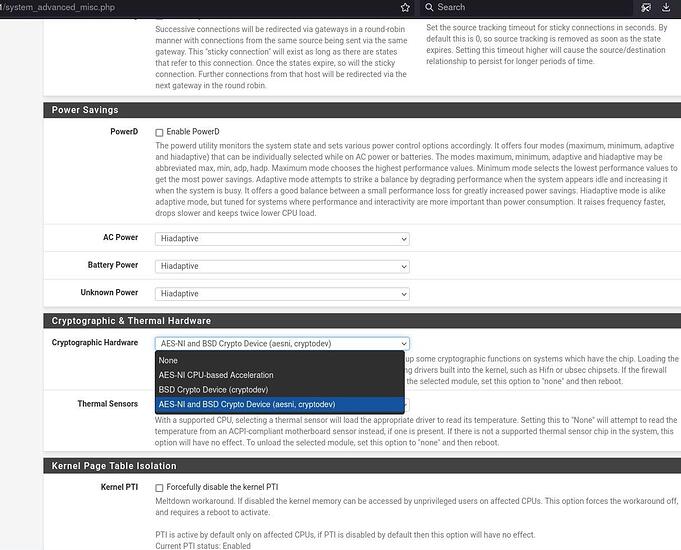
Running pfSense 2.6.0-RELEASE. Under system / advanced / miscellaneous, you can find the option to enable AES-NI. By default, it is set to none.
I just noticed my NAS has a Realtek chip as well ![]()
lspci | egrep -i --color 'network|ethernet|wireless|wi-fi'
04:00.0 Ethernet controller: Realtek Semiconductor Co., Ltd. RTL8111/8168/8411 PCI Express Gigabit Ethernet Controller (rev 06)
Edit: Also interesting, a notebook I have been using as a server has Intel ones:
lspci | egrep -i --color 'network|ethernet|wireless|wi-fi'
00:1f.6 Ethernet controller: Intel Corporation Ethernet Connection (5) I219-V (rev 31)
04:00.0 Network controller: Intel Corporation Wireless 8265 / 8275 (rev 78)
The reason this is interesting is that I could have sworn it was the other way around, because the network controller on the notebook does annoy me from time to time and also has difficulties with anything above 50MB/s on the internal LAN. (It is connected via Ethernet cable, not via WiFi.)
At least some Thinkpads have a rather fragile design regarding the network port so that might be acting up. You might also want to booting up another distro/os to see if it’s a driver / tuning issue.
That’s a toggle for a kernel driver ![]()
https://www.freebsd.org/cgi/man.cgi?query=aesni&sektion=4
I have had hit and miss compatibility with realtek and PFSense. Unfortunately the integrated 2.5Gb Ethernet on my X-570 motherboard isn’t compatible with PFSense. Considering switching over to opnsense as it is supposed to have better comparability.
I slightly doubt it. But do keep in mind that FreeBSD itself should be the one that receives the most recent drivers. The pfSense and OPNsense and TrueNAS folks are enterprise software, so they tend to be conservative with their modifications. Not that FreeBSD is unstable or anything, on the contrary, but when it comes to latest hardware (relatively speaking, BSDs are years behind Linux on drivers), FreeBSD should be the first one where support lands.
That said, I don’t know how close do OPNsense folks keep up with FreeBSD. But I did hear it is closer than pfSense, ever since they moved away from HardenedBSD back to FreeBSD.
It doesn’t, you need to use the realtek vendor driver in ports (how opnsense packages it) or get a nic with better vendor support.
@ThatGuyB
Most common (recent) hardware works fine and I would like to add that “supported” in Linux tends to vary a lot in terms of quality and functionality. I’m not saying that either is better or worse than the other but as far as normal functionality goes it’s quite similar.
The only reason why I haven't moved to Wireguard on my other site is because...
…I am locked out of my ISP’s router, because that piece of junk can’t restore itself to factory defaults, no matter what I try and I don’t have the credentials to access the management on it. I would port forward a lot more stuff if I could (I know, NAT behind a NAT is horrible, but I worked with what I had - setting the ISP router in bridge mode gave me even more headaches with their broken PPPoE server). And the ISP won’t replace it because “it works”.
That happened after asking the ISP to put the router to bridge mode, then after the problems with disconnecting and never reconnecting PPPoE on pfSense and 4 other generic routers from Tenda, Asus, and 2 TP-Links running OpenWRT (weirdly enough, it was working fine on Windows for unexplainable reasons), I asked them to switch it back. And since then, it cannot factory reset itself. And the idiots at my ISP’s call center are saying that they can’t reset the password on their side, because there is no user administration in the admin console of the router. BULLSH*T!
I am already running Wireguard at another site and I am having some weird disconnects on it on a Windows laptop, 2 Android phones and 2 iPhones. All of them have keepalive configured, but from time to time, I have to disconnect and reconnect the tunnel. Weird quirk, kinda bothersome, because my phone doesn’t receive any notifications (is offline) until I restart the tunnel. Not that I need my phone that much.
The advantage that OpenVPN has and why I will configure a new one is that it can run on TCP. I want to set a VPN on TCP port 443 to get around restrictions on certain public WiFis. Had some weird experiences where I could not give or receive calls on Telegram and Whatsapp. I stopped using those, but who knows what else could be blocked if I ever hit a public WiFi like that again. Oh, and my normal VPN was blocked, otherwise, this wouldn’t have been a problem, neither OpenVPN at one site, nor Wireguard at the other worked. So I was SOL and the call was kinda urgent and using my normal number was not an option. Managed it through messages, but I don’t want to go through that ever again (although now I have my hotspot).
@Azulath I forgot the ZimaBoard exists, it’s $200 and has 2 ports. Unless you want to go with the RockPro64, probably don’t buy anything else, lol.
This thing even has a 4x PCI-E slot if you want to add Intel NICs, instead of using the built-in Realtek ones.
It would be interesting to resolve your PPPoE issue but I’m by far no expert on the subject. I’m quite sure that pfSense uses the PPP client in base ( ppp ) while mpd 5.x ( http://mpd.sourceforge.net/ , FreshPorts -- net/mpd5: Multi-link PPP daemon based on netgraph(4) ) seems to be the preferred choice for hi-speed links. OpenWrt’s PPP client appears to be pretty solid in general but there also people who have issues with it looking at the forums.
The issue you’re probably seeing on Android and iPhone devices is the power saving mode that agressively puts non essential services into “sleep mode” once you’re not actively using your phone. I would expect it to link after 10-15 secs or so depending on your timeout though once you wake up the phone. You can tunnel WireGuard using WebSocket(s) but that’s likely not an option on mobile devices.
Another alternative if you want x86 might be picking up a Dell Wyse 5070 ( Dell Wyse 5070 Extended 8GB DDR4 64GB SSD Intel J5005 Win10 IoT | eBay ) and a NIC (haven’t tested this setup myself)
It would also be good to point out for the sake of clarity of discussion that solutions like pfsense / opnsense / ipfire are mainly for x86 and there is a problem with them if you choose ARM.
Pfsense was / is for ARM but only for Netgate devices
IPFire has a few specific ARMs only.
Opnsense does have some ARM ports, but they are far from being perfect.
So if someone is thinking about a straightforward solution based on the above, I would rather avoid ARM. ![]()
If this is going to be an internal router/firewall (between VLANs) and you want fast routing between VLANs then I’d suggest going for an intel/amd small form factor PC to get the throughput.
The small Netgate devices (e.g., 1100, 2100) are good for what they are, but they’re more intended as consumer/SOHO network edge devices where they need to route 100 megabit or so - not gigabit lan connections. If 100 megabit or so between VLANs is enough (and it may be) go nuts, but if you’re expecting higher throughput from one VLAN to another you need a beefier box. The little ARM processors in them won’t keep up, especially if you’re looking to do IDS features or high speed crypto.
If this is for home/lab (and you need throughput) consider virtualising it so you can get the high speed routing performance without spending a bunch.
If its an edge firewall go for either a dedicated pfsense box or an appliance though.
Horses for courses - what exactly do you plan to use this for? And what are the throughput demands? So long as you avoid the requirement for high throughput across the firewall you could very well go for an 1100 negate or whatever, just be aware of the limitations and avoid high throughput from one VLAN to another.
And yeah as above, if you’re rolling your own, go x86. Both for performance and availability/support.