Ok wd
MEssing with linode
Once we get your tunnel working NGINX reverse proxy is simple. We just TCP stream
You will want to enable BBR on the nginx side: (open root terminal)
sysctl -w net.core.default_qdisc=fq
sysctl -w net.ipv4.tcp_congestion_control=bbr
sysctl -w net.ipv4.tcp_notsent_lowat=16384
sysctl -p
Done
Now add a stream block to the main nginx.conf
stream {
include /etc/nginx/tcp.d/*.conf;
}
Thats all we need there. We can make the actual config block in that folder
SO create the file /etc/nginx/tcp.d/00-minecraft.conf
upstream [NAME] {
server [YOUR_MINECRAFT_SERVER IP_INTERNAL/HOME]:[PORT_OF_SERV];
}
server {
listen [PORT_OF_CHOICE];
proxy_pass [NAME];
}
Test
nginx -t
Reload
nginx -s reload
If you already have a domain name via name cheap or someone else. Add a SRV record
Name _minecraft._tcp.[IP].tld
Priority [0-65535]
Weight [0-65535]
Port [PORT]
Value [IP]
Just open the Port you want to use FIRST on both ends! You can also change the defualt port you want to listen on here without changing the port on the server side end
If you want an example of my stream block for DNS (similar): Infrastructure Series -- Recursive DNS and Adblocking DoT w/NGINX
@SgtAwesomesauce correct me if Im wrong but thats all he should need right? Nothing too special. No ssl needed on the stream. Im assuming minecraft handles it
cool we got your tunnel working… excellent. see above
Yeah, looks good to me.
quote of the night
“all the fuckin tutorials online for wireguard are absolute shit” ~ @Argone
LOL
hes not wrong
quick question, proxy_pass name does that need to be something?
Yeah it needs to be the name of your tcp socket.
Aka the same as what you named upstream
So say upstream minecraft {
Then when you write proxy pass
It’s proxy_pass minecraft;
You define the socket port and IP in the upstream block.
Your proxy pass the upstream sockets name
Does that make sense?
ehhh the one on the wireguard site is good if you take a minute to think about it.
The issue is that it’s very simple config that isn’t easy to grok until you’ve done it.
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
Lol
Assuming you’ve allowed it through all sides firewalls. Connecting to your linode on that port should tcp proxy stream to your minecraft server at home. There’s a disadvantage you can’t IP ban so you can only user/account ban. The only IP connecting will show as your linode. Which is fine 
So
Make it so
45.79.183.159:25565 we are in business!
Yes now make an image of that and stops spending so much money on a TCP relay
think about all your lynode is doing is behaving as a relay It’s not doing any chunk loading it’s not doing any of the sort All it does is take the packet request and forwards it then forwards the answer back to your Minecraft clients
one gigabyte there’s no reason to pay 20 dollars instead of 5
Good luck Glad it worked out for you
You also have an added benefit here. If you don’t tie the server to a URL and you just tie it to an IP like you’re doing…
If someone tries to DDOS you just turn down the lanode request a new IP turn the linode back on
Update your friends on the new IP done
Additionally if you do tie it to a URL. You can hand that out to people you trust and then keep the IP public. So when you change the IP you can change a DNS record and assuming your attacker doesn’t know your URL then your friends will automatically receive the updated IP and you don’t need to talk to them about it and you can just change the IP publicly posted 
That’s not 100% foolproof but it’s pretty good
there are other methods such as rate limiting and engine x but you got to keep in mind that that comes with its own fair share of headaches
I hope that this gives you an appreciation for the level of automation that these hosting services do in order to host your Minecraft server not only on a URL but also to provide a rudimentary amounts of DDoS protection
P.S change the ssh port so you stop bots trying to brute force it
P.S disable root login, make a user
P.S disable cockpit web socket if it exists on the linode 
P.S use public key auth for your ssh. Passwords are so 2020
I think we’re adding unnecessary complexity here. Everyone who suggested running a little Wireguard tunnel on a Linode VPS is providing sound technical advice, however I think you should focus on the underlying problem – who are you trying to keep out of your network?
If you still wanted to stand up an NGINX or HAproxy node in front of your server to act as a reverse proxy, that may be fine, but you should invest more time in securing your Minecraft server or whatever is open to the web. Only open the ports you absolutely need (19132?). Try securing your server with a robust firewall and Fail2ban: http://www.fail2ban.org/
Cloudflare offers free tier service that can also assist in protecting and securing your server, but it’s no replacement for investing the time to lock down your environment. YMMV, good luck with your project, sir.
If you want it public facing so any friend can access it you could use Bungeecord, then use Wireguard to tunnel between local and the VPS, or open the port and add a plugin on the mc server to only allow users from the VPS static IP and local network to connect.
What i did was the nginx reverse proxy approach anyone can connect now. The plan is to have it a public server.
solutions finished m8. Should have marked it as resolved I guess lol. We gotta start doing that with threads around here. He ran an NGINX reverse proxy node which is a pretty good way of obscufating his home IP. Which ultimate seemed his goal. It added an advantage. He wont be caught violating terms of service with his HOME internet connection (non business its a violation of TOS on literally all providers).
Cloudflare is a single point of failure tbch and theres a lot of us with anti cloudflare sentiments but I think he did a good job of handling his environment. You lock down the external. Internal locking down can be rather disadvantageous and not really pragmatic. Ive found that out on my own setups.
The thing about cloudflare is. It just shifts the ddos to another centralized service. Someone takes down cloudflare they can take down half the internet. Also funneling all the traffic through one company. God no. The internet practically has gate keepers now and thats very worrisome
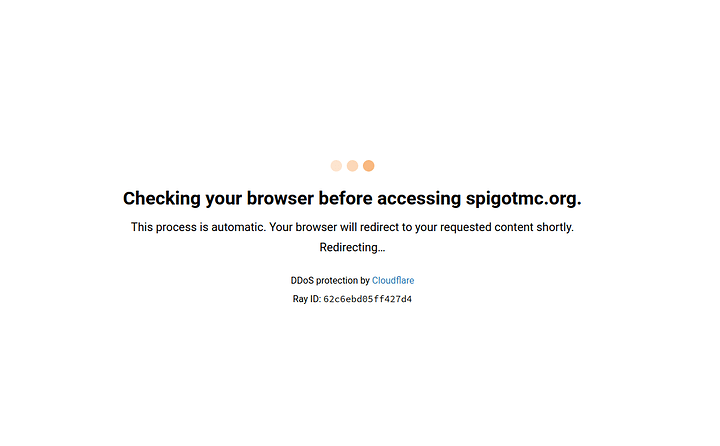
God I hate this fuck off cloudflare
Everytime because I have this
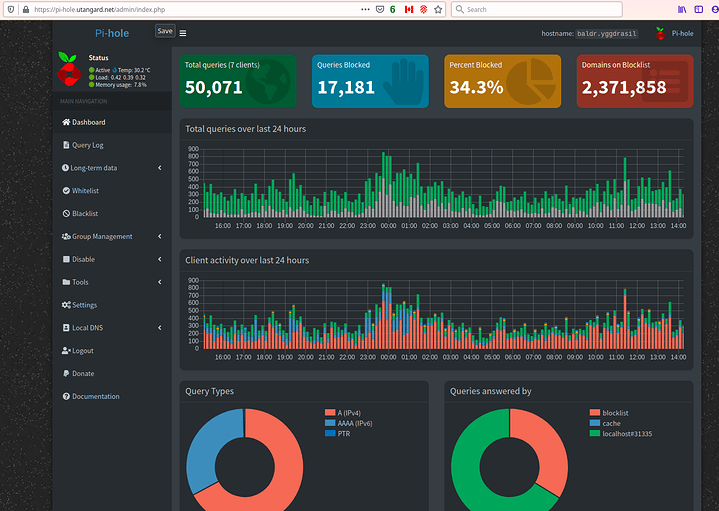
and
(my own recurssive (Top down) DOT+DOH pihole+unbound DNS server)
This is a good reason to detest their protections alone. I should be able to avoid ads and tracking anywhere I want to be and not be forced into a rate limit. To the hell with cloudflare. Happens on this forum too
Sorry to chime in on an old, dead/dying thread. Reddit has really gone down the tubes, this community seems to be thriving and people still discuss a wide array of (on topic) technicals, from hardware to software to theory and beyond. My point being, please forgive me as I get accustomed to these wonderful new surroundings.
I have a few NGINX instances running, but I really should invest the time to stand up a proper reverse proxy. My network management server runs its own little reverse proxy within the Docker stack that it got deployed with, plus I have an actual NGINX Debian VM running my web server (went Apache2 > NGINX somewhat recently) as well as a third instance running in the cloud for my UniFi Controller. Ultimately I believe I will turn the pure Debian web server into a dual role, also assuming reverse proxy duties. Any security related issues with having these on the same virtual machine? NGINX has been super simple to stand up, but a lot of moving pieces trying to get all my internal services working properly with their own security certificates. Not sure how much effort is reasonable for my little “lab” environments.
Talk to me a little more about your Pi-hole setup. I’m also running Pi-hole, Unbound + Wireguard on both my DNS servers (for redundancy, one VM + one RPi - only one survives in the event of a power outage). My router captures and invisible redirects (over 5335) any queries on the network from devices with hard-coded DNS settings, but I’m only utilizing DNSSEC (not DoH or DoT, let alone both) on Unbound, which reaches out to TLD via root.hints
It’s not perfect, but disabling Pi-hole’s DNSSEC has sped things up significantly. I’m happy to trade off the slower uncached queries for nearly instant (<1ms) response times on any cached hits, although I only run about ~half as many domains in my blocklists.
I understand (and agree with most all) the incredibly relevant points you made, especially regarding CF (or any other major technology gatekeeper), but I suspect they (as an organization) are MUCH more robust and capable of fending off a variety of attacks (especially DDoS) than your average user running NGINX in shared compute backed up by 40Gbps pipe, or whatever most VPS commonly offer.
Only semi-related example; I don’t love that Google’s browser dominates the landscape, but I’m not going to gimp my day to day experience running inferior software. Thank the maker projects such as Brave & Vivaldi exist. Edge Chromium is fantastic for the normies, but we demand more. FF is barely competitive these days, capturing what, 6% of the market? That being said, FF Focus goes on every mobile device I use…
but even Richard doesn’t go FULL Stallman all the time. I guess I’m trying to say it’s a fine line between being “too” principled and having a usable workspace at your fingertips, ready to roll or react with a literal press of a button.
Hope it’s alright that I took some liberties rambling, got a bit off topic, but you did say the original issue was now resolved. Now I know who to pester when the time comes to work out syntax errors in my future NGINX block(s). 
Stay safe, sir. Thanks for the detailed response above. So much to learn.
ill reply on my blog