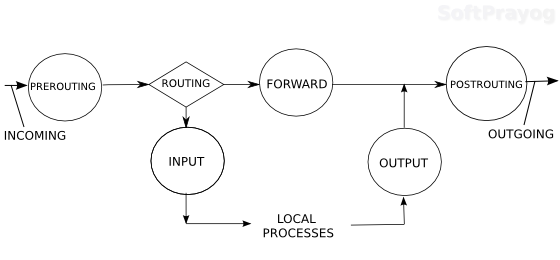
Any thoughts?
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
-A INPUT -p tcp -m tcp --tcp-flags FIN,ACK FIN -j DROP
-A INPUT -p tcp -m tcp --tcp-flags PSH,ACK PSH -j DROP
-A INPUT -p tcp -m tcp --tcp-flags ACK,URG URG -j DROP
-A INPUT -p tcp -m tcp --tcp-flags FIN,RST FIN,RST -j DROP
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN FIN,SYN -j DROP
-A INPUT -p tcp -m tcp --tcp-flags SYN,RST SYN,RST -j DROP
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG FIN,SYN,RST,PSH,ACK,URG -j DROP
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG NONE -j DROP
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG FIN,PSH,URG -j DROP
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG FIN,SYN,PSH,URG -j DROP
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG FIN,SYN,RST,ACK,URG -j DROP
-A INPUT -f -j DROP
-A INPUT -m state --state INVALID -j DROP
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN FIN,SYN -j DROP
-A INPUT -p tcp -m tcp --tcp-flags SYN,RST SYN,RST -j DROP
-A INPUT -p tcp -m tcp ! --tcp-flags FIN,SYN,RST,ACK SYN -m state --state NEW -j DROP
-A INPUT -i lo -j ACCEPT
-A INPUT -s 192.168.1.14/32 -i enx001e0630caa8 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 8080 -j DROP
-A INPUT -p udp -m udp --dport 8080 -j DROP
-A INPUT -p tcp -m tcp --dport 3389 -j DROP
-A INPUT -s 192.168.1.1/32 -i enx001e0630caa8 -j ACCEPT
-A INPUT -d 127.0.0.0/8 -j DROP
-A INPUT -s 127.0.0.0/8 -i lo -j DROP
-A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A INPUT -j DROP
-A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A OUTPUT -o lo -j ACCEPT
-A OUTPUT -d 127.0.0.0/8 -j DROP
-A OUTPUT -d 9.9.9.9/32 -p udp -j ACCEPT
-A OUTPUT -d 9.9.9.9/32 -p tcp -j ACCEPT
-A OUTPUT -p tcp -m tcp --dport 443 -m state --state NEW -m tcp -j ACCEPT
-A OUTPUT -p tcp -m tcp --dport 80 -m state --state NEW -m tcp -j ACCEPT
-A OUTPUT -p tcp -m tcp --dport 21 -m state --state NEW -m tcp -j ACCEPT
-A OUTPUT -d 192.168.1.0/24 -j ACCEPT
-A OUTPUT -p icmp -m icmp --icmp-type 8 -j ACCEPT
-A OUTPUT -p icmp -m icmp --icmp-type any -m limit --limit 1/sec -j ACCEPT
-A OUTPUT -p icmp -m icmp --icmp-type any -j DROP
-A OUTPUT -j DROP