More news on the Power architecture front, an IBM bulletin says that POWER7+ and POWER8 are getting all three CVEs patched in firmware, with OS updates also necessary. POWER9 is supposed to not need KPTI, but I have more about that in the Power Architecture thread:
It’s not weird that AMD is being sued. They pretended they weren’t vulnerable to Spectre 2, then went on the record and admitted that they are vulnerable.
https://finance.yahoo.com/news/amd-ceo-chip-security-flaws-absolutely-211517325.html
They didn’t though. They only said the exploit is extremely hard to pull off on AMD (maybe true, maybe not, I don’t have the knowledge for that) and thus is is unlikely they are really affected.
They never denied they were vulnerable. That was the media.
They pulled the usual corporate BS and now they are getting sued over it. Not the first time and certainly not the last. They lost such a suit not that long ago.
So in the absence of details, any serious discussion about #skyfall or #solace would be as speculative as a x86 processor arriving at a branch instruction.
Also @Pholostan try not to derail the thread too much 
We know where out of order speculation can lead.
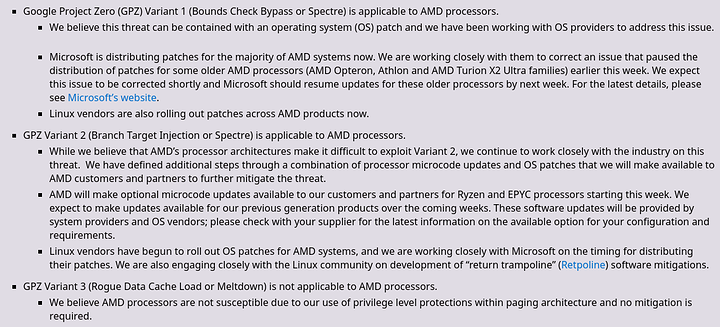
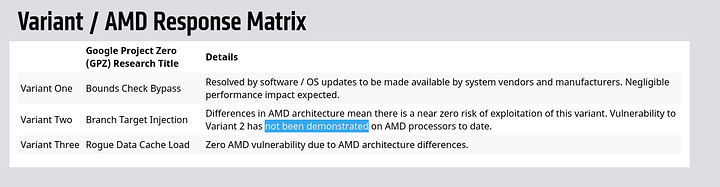
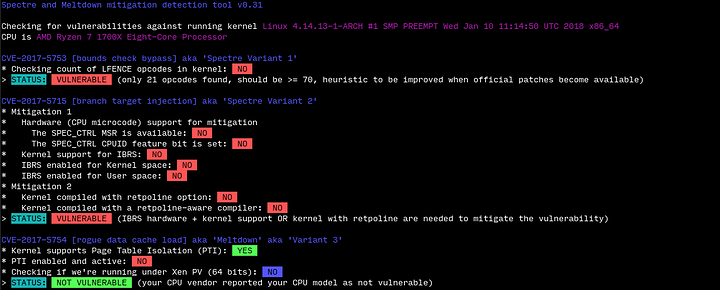
I’m not speculating though. AMD has confessed that they are vulnerable to Variant 2 and are pushing microcode patches. It isn’t something they are doing just for fun. There is no doubt about AMD Ryzen and EPYC being vulnerable to Variant 2, they all are.
Puns! You got’em. 
This I see differently and I am pretty sure this is why the statement was worded the way it was. As I said before, there is a difference between what the actual statement is (legally) and what the wording implies. I don’t see that lawsuit to succeed.
Scroll back up on this thread. I said that from the start even. I personally tried cracking Variant 2 on AMD Hardware and got a partial PoC working. AMD has been careful with the wording since the start.
https://www.amd.com/en/corporate/speculative-execution
From the 11th Jan (5 days before the case filing)
From the 3rd Jan (initial statement)
In the kindest way possible I want to say “you’re beating a dead horse”.
If you know what I mean.
Also I’m not too concerned about the lawsuits. I’m fighting for the users here not any particular company.
Exactly, I wish they would have been more clear and said: “yes we are theoretically vulnerable but we can’t get a Proof of Concept exploit to work” but that’s just wishful thinking.
In their defence, some test results can be ambiguous:
However, they do have the actual schematics and can actually look at the design, so maybe that isn’t much of a defence.
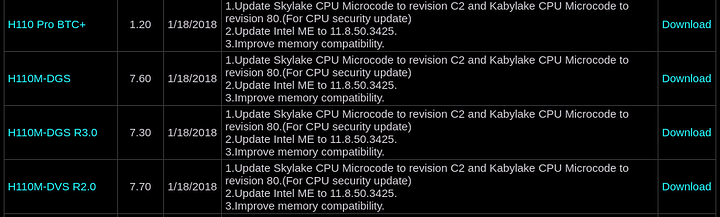
Finally some good news for users of older AMD processors that had their systems broken with the emergency updates.
The revision 80 microcode patches are also starting to roll out on Intel’s side for the large mainboard manufacturers.
http://www.asrock.com/support/index.asp?cat=BIOS
Still waiting on Spectre microcode patches for AMD
Arch also seems to be slower than usual with 4.14.14 release. Should hit mirrors by tomorrow.
I like the “we believe” statement. Just like Intel “believe” that they are selling secure and trustworthy products 
To be frank it’s a legalese term everyone in any industry uses.
It would be amateurish for any company to not use that term in such statements.
All these publications go through the lawyers first before publication, so I fully expect to see such language.
My old AMD laptop will probably not get any patches, it is getting ooold…
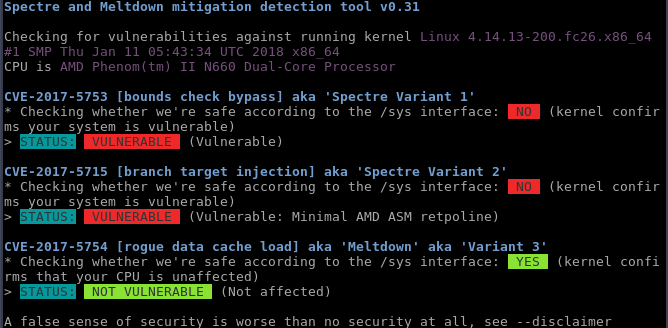
It likely may get a microcode image that’s loadable by the kernel at boot at some later point.
But that’s up to AMD.
Tons of older systems however will be left out in the cold. But if anyone is on Core 2 Quad/Duo you’re screwed anyhow even pre spectre/meltdown since that architecture is absolutely fubar already.

4.14.13-1-ARCH here performance seems erratic at times. Could be placebo tho.
By that logic, just about anything should be answered by a solid “yes” as any number of future factors could make today’s security obsolete, such as the promise of quantum computing on encryption for example. The problem is, theories sometimes are proven true and sometimes they’re proven false. Just because something is theoretical at this time does not make it automatically true.
If AMD stated that they have no doubts they have the most secure products in the world, like someone else we know, they would have some serious egg on their face if they were later proven to have a vulnerability after all. This is why they carefully worded the statement like they did.
If there ever are any microcode released for old ass Phenoms, I might try this guide for patching non-UEFI BIOS:
https://www.win-raid.com/t2811f47-Guide-How-to-update-CPU-microcodes-NCPUCODE-BIN-CPUCODE-BIN-on-a-non-UEFI-Award-Phoenix-BIOS.html
But yeah, it looks like users will be left in the dust. Will be interesting to see if any motherboard vendor will bother to patch any bios for motherboards older than Intel 100-series.
I’ve got an older Dell C2D system I was using for my pfSense router. Dell didn’t bother to patch the IME vulnerability and I have no expectations they will bother with meltdown/Spectre.
I’m currently in the process of building a new router to replace it because at this point I’ve got no excuse. Running older hardware, especially Intel might be nice on the pocket book, but is a bad idea when security is important.
That’s on Intel, not the vendors. They just get the microcode blob supplied from intel to package into the bios.