Hi, I have problem with my pptp VPN. Bellow there is my config that worked but doesen’t work anymore.
/ip firewall mangle
add action=mark-routing chain=prerouting dst-address-list=Kancl in-interface=bridge1 new-routing-mark=Kancl passthrough=yes src-address-list=XPS
/ip firewall nat
add action=masquerade chain=srcnat dst-address-list=Kancl out-interface=Kancl src-address-list=XPS
add action=masquerade chain=srcnat
/ip route add
disabled=no distance=1 dst-address=0.0.0.0/0 gateway=Kancl pref-src="" routing-table=Kancl scope=30 suppress-hw-offload=no target-scope=10
/routing table
add disabled=no fib name=Kancl
/interface pptp-client
add connect-to=XXX.XXX.XXX.XXX disabled=no name=Kancl user=XXXX
/ip firewall address-list
add address=192.168.88.254 comment=LAN list=XPS
add address=192.168.88.241 comment=WIFI list=XPS
add address=92.62.0.0/16 list=Kancl (public IPs)
add address=100.64.0.0/10 list=Kancl (public IPs)
add address=10.0.0.0/8 list=Kancl (private IPs that is why I am using the VPN)
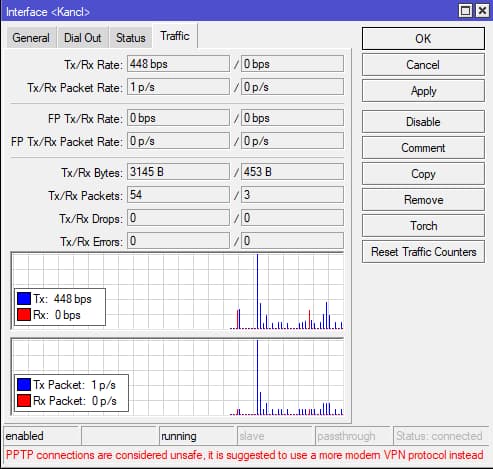
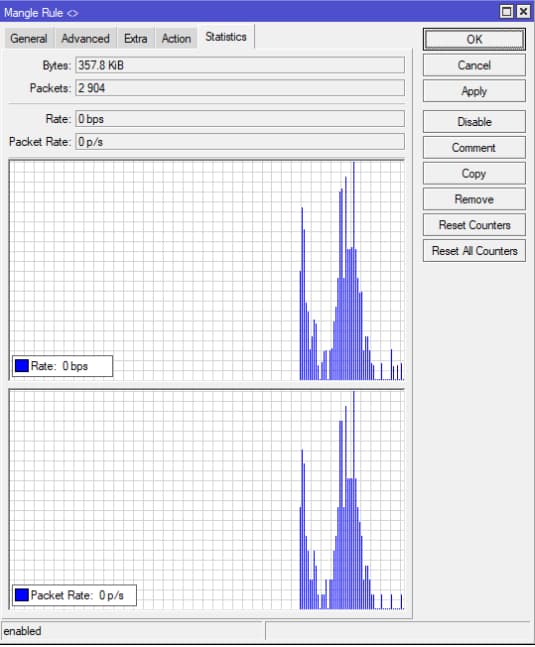
It looks like that the FW rules works based on these graphs. The router is RB5009 on v7.6 (it worked on V7 before) And yes, the VPN is conected
16:39:12 pptp,ppp,info Kancl: authenticated
16:39:12 pptp,ppp,info Kancl: connected
16:39:12 pptp,ppp,info Kancl: using encoding - MPPE128 stateless
It just stopped working without any changes. I even looked in my backup from november and the config is same and it worked before and there shoudnt be problem on the end. I can connect via VPN on my PC to that and it works fine.
The FW should be OK too (this is not my standart firewall, I reduced it to bare minimum):
/ip firewall filter add
action=fasttrack-connection chain=forward comment="Fasttrack UDP" dst-port=53 hw-offload=yes in-interface=ether1 protocol=udp
add action=fasttrack-connection chain=forward comment="Fasttrack TCP" dst-port=53 hw-offload=yes in-interface=ether1 protocol=tcp
add action=accept chain=input comment="accept established,related" connection-state=established,related
add action=accept chain=input comment="allow ICMP" in-interface=ether1 protocol=icmp
add action=accept chain=input comment="allow SSH" in-interface=bridge1 port=22 protocol=tcp
add action=accept chain=input comment="allow Winbox 8291" in-interface=ether1 port=8291 protocol=tcp src-address-list=allowed_to_router
add action=accept chain=input comment="CAPSMANAGER Discovery" in-interface=bridge1 port=5246,5247 protocol=udp
add action=accept chain=input comment=OpnVPN-PASS dst-port=1194 in-interface=ether1 protocol=tcp add action=drop chain=input in-interface=ether1
I think that the rules are working based on those graphs but it doesent want to go through the nat.
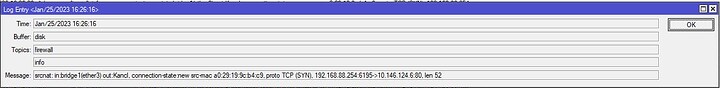
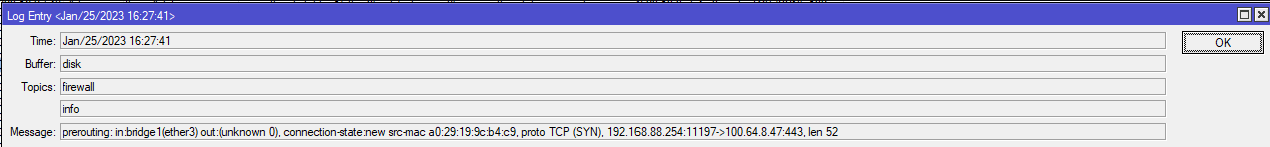
I thought that FastTrack could be the problem but removing it doesn’t help. If I use the pptp client it doesn’t work and I can’t even access these IPs 92.62.0.0/16 (public range) and 100.64.0.0/10 even though they are public IPs (these IPs are blocked for some reason). I even tried to disable the FW and that didn’t work too.