Well, that is what it said. Let me give it another go.
I’d be a little scpetical when it comes to a 186GB version of wireshark.
The download here is probably a bit smaller:
https://www.wireshark.org/#download
OK, I ran it anyways, it’s only 57.2 MB!!! Oh gods help me now! Now I just have to figure out how to read this gibberish. I don’t suppose there is a shortcut key anywhere that just says “NSA Eavesdropping”, or “Illuminatti Confirmed”?
Well, I’m off to watch some interface tutorials.
I really swear it said 186GB, that is so strange.
Learn how to use the SysInternals AutoRuns tool, you can use it to quickly find out if any malware is trying to autostart on boot or login. A great bit of software, I sometimes use it to just debloat older windows installations.
I would not even boot into windows.
Use something like Kaspersky Rescue Disk https://support.kaspersky.com/de/viruses/krd2018 to prevent potential further background shenanigans in Windows.
KRD is more of a virus scanning OS than a virus scanner in the classical sense
OK, I ran wireshark for awhile while I watched some youtube videos on it. It would be than fair to say I have no idea what I am doing, but I did find a video that detailed a quick check to see if data was being sent that wasn’t recognized.
I went to statistics, then protocol hierarchy, and no data file was there.
Is there a better way to check?
I got a data hit under protocol heirarchy. Is there anyone out there who sees anything in this?
43 7.908008 192.168.0.3 18.204.105.183 TCP 55 [TCP Retransmission] 51044 → 443 [ACK] Seq=0 Ack=1 Win=252 Len=1
It looks like it was between my router and motherboard.
I’m a firm believer in Malwarebytes AM. I use it & Defender (I know neither are “proper” antivirus suites) with periodic online scans from a few companies. Eset NOD32 used to be my favorite, then BitDefender and Webroot…My net behavior is much less risky these days. No warez sites and only known good sites now.
Yeah, I was just trying to look up a company. Don’t look it up!
perhaps you might be interested in checking out Firefox with the noscript addon?
It has many false positives, and actively harms your user experience, but I don’t think I would browse on windows without it
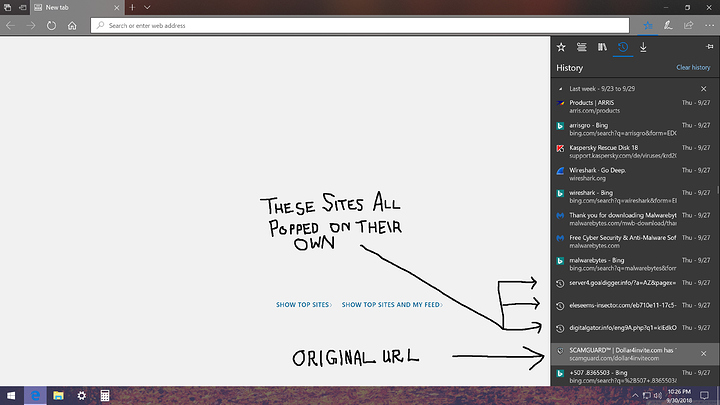
Now we all know to stay away from dollar4invite.
Haaaaaa. Even when I uninstalled it, there was still a file left behind, and it was running in Windows Explorer. I assume it was the explorer compatibility running behind edge. You have to stop it, then it can be deleted:)
If you’d like some help I’m a network security analyst by trade and can take a look at your packet capture. If you give me the urls you visited I can investigate those as well.
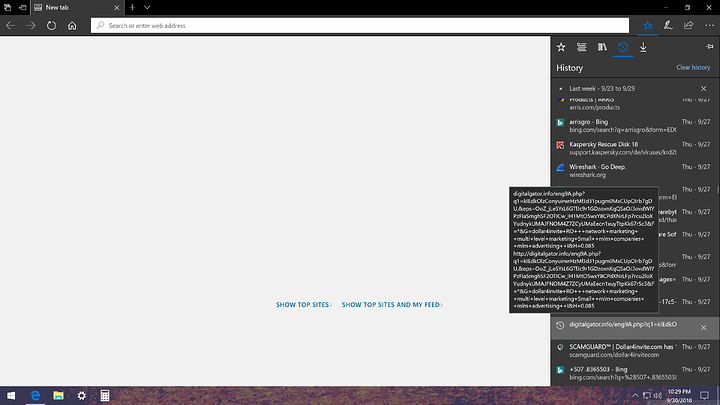
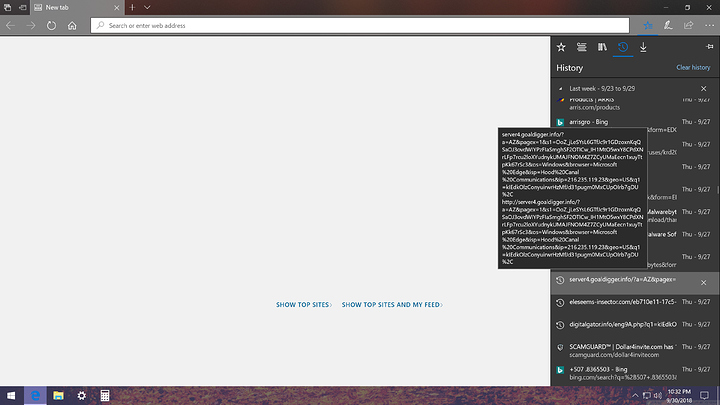
The main website was Dollar4invite with a dot com at the end. The 3 links in the screenshot popped on their own in rapid succession, then the crazy stuff started.
I apologize for my lack of ms paint skills in the first screen capture, the following ones include the expanded url’s.
Is there a specific way you would prefer the packet capture? Do I need to do anything in particular to cause a virus to show itself during the capture?
I appreciate that you were willing to look at this, but honestly, I expect nothing. But if it’s an entertaining exercise, I will cheer you on wholeheartedly:)
I guess I should say I don’t think it was the scamguard website that did it, it was when I typed in the dollar4invite into the search header that I found on the scamguard website.
So here’s the basic rundown from what I’ve seen so far.
The site reaches out to 9 domains and 12 hosts. Several of them do various malicious activities. Mostly installing hooks in running processes. In this case watadminsvc.exe and iexplore.exe (Ex: Spawned process “iexplore.exe” with commandline “SCODEF:1544 CREDAT:275457 /prefetch:2”). It also attempted to open the service control manager (OpenSCManager) requesting admin rights with SC_MANAGER_CONNECT, this is generally seen as a malicious API call. (Example:https://attack.mitre.org/wiki/Technique/T1035).
On top of that it dropped a lot of files for a parked domain, most likely malicious, but it’s hard to tell. some of the http requests had some weird base64 encoding, but I couldn’t decipher what they were attempting, and decoding it just gave me back gibberish, may be nothing.
the major thing would be the hooks it tried to install:
“iexplore.exe” wrote bytes “b06153f3fe070000” to virtual address “0xFE1655C0” (part of module “SHLWAPI.DLL”)
“iexplore.exe” wrote bytes “00ef4ff3fe070000” to virtual address “0xFC2E18D0” (part of module “COMCTL32.DLL”)
“iexplore.exe” wrote bytes “506953f3fe070000” to virtual address “0xF4CB30E0” (part of module “IEFRAME.DLL”)
“iexplore.exe” wrote bytes “401c4ff3fe070000” to virtual address “0xFF4B1318” (part of module “MSCTF.DLL”)
“iexplore.exe” wrote bytes “401c4ff3fe070000” to virtual address “0xFE2505A8” (part of module “OLEAUT32.DLL”)
“iexplore.exe” wrote bytes “b06253f3fe070000” to virtual address “0xFE7F1C30” (part of module “SHELL32.DLL”)
“iexplore.exe” wrote bytes “500751f3fe070000” to virtual address “0xFE7F1ED8” (part of module “SHELL32.DLL”)
“iexplore.exe” wrote bytes “401c4ff3fe070000” to virtual address “0xF4CB1D78” (part of module “IEFRAME.DLL”)
“iexplore.exe” wrote bytes “b06253f3fe070000” to virtual address “0xF4CB2DD0” (part of module “IEFRAME.DLL”)
“iexplore.exe” wrote bytes “90d149f4fe070000f01d5a3f01000000101e5a3f01000000e0365a3f01000000501e5a3f010000000000000000000000” to virtual address “0x3F5A8000”
“iexplore.exe” wrote bytes “406853f3fe070000” to virtual address “0xFF36BEA8” (part of module “OLE32.DLL”)
“iexplore.exe” wrote bytes “406853f3fe070000” to virtual address “0xF4CB2DD8” (part of module “IEFRAME.DLL”)
“iexplore.exe” wrote bytes “00ef4ff3fe070000” to virtual address “0xF4CB2D50” (part of module “IEFRAME.DLL”)
Since you killed it part way it could be unsuccessful.
If you’d like feel free just to send me the pcap file from wireshark, you can save your capture from the menu and just send it as the file it is natively. If you do that, don’t search the web while using it as it will give me all that information as well, which is something you generally don’t want put on a forum for anyone to download, including myself.
Are you in the EU?
As someone that barely has any experience in networking and browser security this thread has been both interesting and scary to read.
Can someone explain to me how clicking on something in a browser can lead to a shell starting to execute stuff?
Obviously this is not supposed to happen with a browser sandbox. I had the impression that with an up to date operating system and browser even clicking on a dubious URL that sends a lot of malicious javascript not a whole lot can happen. It seems my overly cautious approach of opening suspicious links only in a fedora VM and burning it afterwards is not that crazy at all?
Did you visit these files in a VM? Also, do you think running sfc /scannow could revert the changes?
@anotherriddle Basically, when an unknown entity is allowed to run code on your machine, e.g. JavaScript, malicious things can happen sue to various exploits. (Rowhammer for instance)
I know, however Rowhammer is kind of sophisticated and also not very fast. I just did not expect exploits like this to be common.