Well last year somebody called Bell and managed to get my parents’ business line deactivated even if his fake name was not in the profile. We only noticed the line has been cut because my sister try to call home and didn’t succeed.
Turns out the guy was a bit sloppy at cleaning his trail, he deleted the emails that he received during his “visit” but forgot to remove them from the trash.
Turns out he reset the password on my coinbase account that I have not used in two years, using my number to bypass the 2 factor, and tried to buy some bitcoin but the transaction didn’t go through. I never keep my crypto in an online exchange or on a computer that’s connected to the internet so I suppose my cautious approach paid off in the end.
Very interesting, maybe it was a PI doing research on you/your place of work  if you are married PI’s are usually hired by wives/husbands/parents who suspect cheaters… and when they suspect it the PI’s usually find it’s true.
if you are married PI’s are usually hired by wives/husbands/parents who suspect cheaters… and when they suspect it the PI’s usually find it’s true.
It’s good to know that you recovered, but I have to ask, why does coinbase have a recovery option for phone numbers? Seems like a security risk, nowadays we use emails or backup codes as a recovery option (or done properly, security questions). Kinda out of date don’tcha think?
Having 2FA on your online services is a must […] There’s a simple app called “Google Authenticator”
There’s known malware in the wild that steals Google Authenticator-style OTP credentials.
If you’re implimenting 2FA in 2020, look at FIDO, not OTP-based options like Google Authenticator.
It’s the future, and devices that handle it are cheap.
I am sorry to hear that you have become a victim of these scum.
I wrote about it once that sim methods are becoming more common but hardly anyone listens. 2FA based on sms is not a security!
https://forum.level1techs.com/t/too-smart-to-be-secure/153302/2?u=timholus
I need to come back to this tonight but just a thought. Did they go after anything else or just Coinbase? Because if it was just crypto then it sounds more like a targeted attack.
FIDO U2F is good but you have to spend $ and not always one key is enough.
The problem with OTP is how people use it, not the solution itself. Theft is taking place because people use everything on one device that is online.
Good security is uncomfortable … people don’t care about a higher level of security because they prefer convenience …
If a person uses the same pc / tablet / smartphone to login, store l / p and 2FA then the level of security is immediately lower.
OTP should be a separate security mechanism implemented on a physically separate device that should not be online and only the owner has physical access to it.
For example, I have a dedicated laptop with encrypted ssd using veracrypt and WinAuth for OTP. The laptop is always offline. Only I have physical access. When I have to log in and use 2FA it generates a code and I just look at the screen … Try taking over my 2FA!  But this solution is not very comfortable and it is certainly not a mobile solution, so the average person will never use it.
But this solution is not very comfortable and it is certainly not a mobile solution, so the average person will never use it.
Optimally, everyone will carry around a seperate, non-nfc, non-usb, non-internet connected device for their OTP, and then use their cellphone for the complex passwords. Obviously not realistic for all, but this is a very good way to reduce the possibility of accounts being comprimised. Fuck NFC badges. Fuck SMS MFA. Fuck weak passwords. Offline MFA + password complex password database FTW.
Edit: Forgot to mention; bank cards and credit cards are a form of MFA, for those unaware; the physical card is a (mostly) offline card required for a transaction, with the (not-so-complex) password in your brain.

What happens if that thing just implodes?
In short, all the actor has to do to make use of the 2 factor authentication codes is to steal an RSA SecurID Software Token and to patch 1 instruction, which results in the generation of valid tokens.
OOF
Strange, I got my Gmail account highjacked by someone from Alberta, CA, as well.
It was an old Gmail account I wasn’t using anymore. The password was randomly generated by Keepass. It was not brute forced
First, they accessed my Google account and changed the password. I received a notification and was quick to go and change it to a new password. Note how Google let me do it.
Second attempt was a few days later. They changed the password and all the recovery info this time. Google says “blah blah we can’t allow you to recover from this device”.
Learned two things: Strong passwords mean jack squat these days apparently and Google doesn’t care about you.
I really wish everyone had an option to disable recovery procedure and optionally lockout IPs for x hours/days after incorrect attempts. I never make a mistake entering passwords and they’re strong enough.
Recovery is just another attack vector. Plus you need to remember/store all that information.
This is where I advocate storing that in keepass
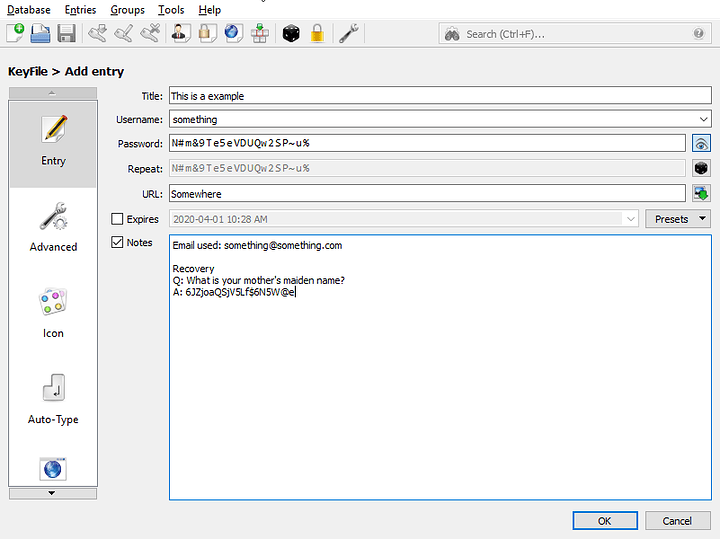
I would have my username and randomly generated password stored in keepass, but for recovery question I would also use randomly generated strings from keepass for my answers.
To store that information, I use the notes section of keepass or store that information on a text file as an attachment to the specific keepass entry.
An example would be like this:
Which is what I do. Answers are random unrelated stuff. But yeah random generated stuff is even better.
My attacker either brute forced them (seems rather unlikely imo) or they have a way of making Google think they’re on a trusted Android device, which is what I believe happened.
i have a weird thing with all my stuff lately. I have an old Yahoo account from 2000 that I have all my password stuff sent to. I rarely use it cept once a month when I change all my passwords. I finally have started using last pass, because I can’t afford anything else, but my main password is a very long sentence. And i change it every 2 weeks. (I have done this since I had an unrelated google account get hacked somehow without my main yahoo account getting compromised. This was 4 weeks ago.)
I also have all of my passwords stored on a USB stick that sits inside the leg of my big vintage school teachers desk from the 80’s. Those passwords are scrambled twice. So even if they get the usb stick, they’re not gonna know what those passwords are.
I thought of all of this like 4 weeks ago Because i decided to go back and reconnect with all the email accounts i’ve had since the early 90’s and either delete them after getting all the info off them, or if I can’t get them deleted, I have deleted everything off them and have the passwords set to some weird gibberish that I don’t even know of anymore.
I will not have anything of mine hacked again. I’m taking all of this way to seriously. But I’m happy with it.
Where do you store the Keepass files, are they all kept on USB sticks or are they also stored in cloud storage?
Banking and yahoo email… should of switch that a long time ago. Something to be said for more modern email accounts. Might use it for a spam dump…about all it is good for these days.
If you have the time, listen to Reply All’s “The Snapchat Thief”; it’s very illuminating. This happens to regular people all the time.
After listening to an episode of Reply All about SIM-swapping, I found a service that allows me to port my phone number away from a SIM card, then I got a new phone number from my original service provider just so I can have mobile data. I don’t use this phone number anywhere (at least not anywhere associated w/ my identity, and I don’t share it with anyone (to prevent them from saving it to their Contacts in the context of my identity)). I’ve been using this service for over a year now, and have been pretty happy with it. Idk if I’m allowed to link to the service w/o solicitation (new to the forum), so feel free to ask me about it. The developer of the service is very responsive and has an XMPP/Jabber chatroom anyone can join.