Their Pro model includes 2x SFP+ but you’d be installing a 24 port switch (USW-Pro-24) at each of your 6 locations. And as you’ve already noticed they don’t make any 8 or 16 port switches with SFP+. This is why I touched on consolidating all your drops to possibly a single location (or to only a few).
https://www.tp-link.com/uk/business-networking/managed-switch/tl-sg3210xhp-m2/v1/
or
They have a 10G uplink + another 10G port for a workstation or a NAS + a bunch of 2.5G
- you’ll need some switch with a couple of 10G SFP+ centrally for your NAS / future internet router. unifi has an 8 port for about 250
Do you have a drawing or an inventory list of what you have in each location?
I think this should be good for approximately the environment you described over the next couple of years, but is probably financially not very optimal today.
Yes, or no, depending on what your real budget is how much you value having a unified managemnt plane vs doing your config on each device.
For something new in 2022 I would not consider 1GB copper for the uplinks and go straight to 10Gb fiber
If you value your time, it is the only option you have, getting up to speed with proper VLAN configs/trunking and such is usually already a challenge on its own. You don’t want to add different UIs, terminology, different implementation of the concepts by going with different brands
Leaf switches:
CSS610-8G-2S+IN
8 x 1 Gig
2 x SFP+
no POE
can be powered via POE using port 1
100USD
CRS112-8P-4S-IN
8x 1Gb POE Out
4x SFP (not SFP+, so limited to 1Gb uplink)
189USD
Top of Rack:
CRS309-1G-8S+IN
1 Gbit
8x SFP+ 10Gbit
269USD
or
CRS317-1G-16S+RM
1 x 1Gbit
16 x SFP+ 10Gbit
399USD
Please note the pricing do not include the cost of the transceivers (around 30USD each for fiber, 70USD for copper)
Not really, it’s more a matter of finding the brand that has the most sensible options for your use case, and then deciding based on price/features how much you want to overspend.
Mikrotik for me is the best bang/fetaure for bucks option at the moment, as their devices are more than reasonably priced and have line rate performance when used as switches (when doing layer3 performance isn’t really there yet unless you go fo the much pricier and server room grade models) and have the most non server room sensible specs I could find. Almost all ‘server grade’ gear assumes they’ll be running in a rack/server room and have fans sized accordingly (i.e. they are loud as fuck in a non server room environment)
I have just deployed 3x CSS610-8G-2S+IN across my house, using fiber runs and fiber transceivers, and hooked up my old Cisco SG200-26 for all the gigabit runs I have in my attic. I have also bought a passive POE injector with 8 ports, that I use for powering the three switches, a pair of ubiquity access points and a pair of wifi WAN routers. As said, layer2 perfromance is line rate (970Mbit/s on the gigabit ports, couldn’t really test the 10Gbit properly as I only have one workstation with a10Gb card, so far)
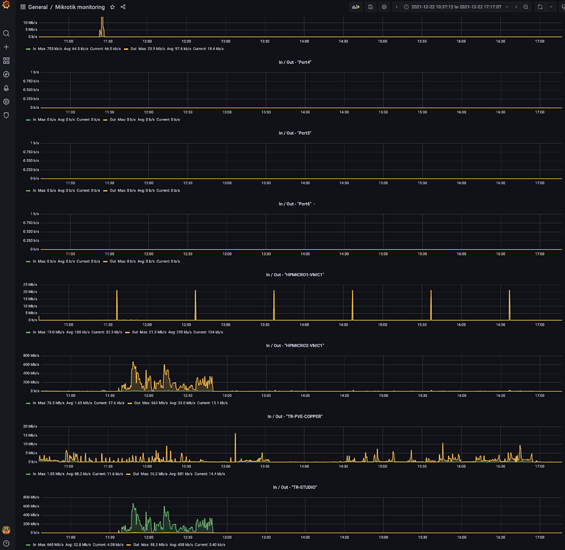
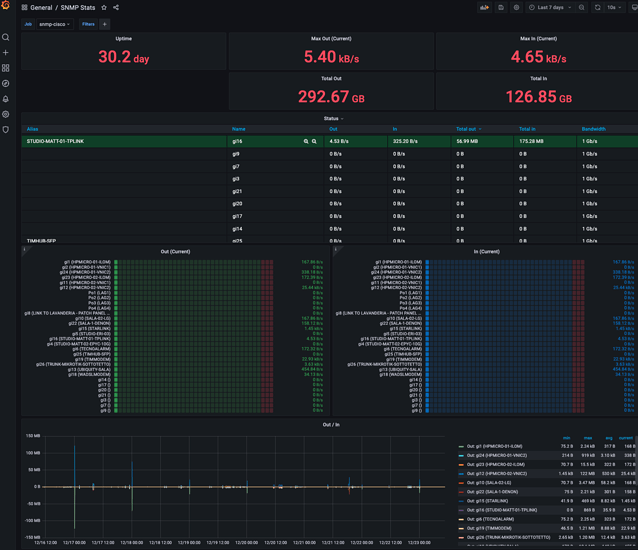
Also, they come with support for prometheus and you can get your compulsive control OCD on with stuff like this:
… to be fair, you can get on with ciscos as well, if control is your poison:
I hear you, but home runs are impractical. I’m in a 70 yr old bank with a sprinkling of 2 prong outlets. Like a simple vertical run…
…becomes a day-long project when you find the top plate of interior walls is a 2’ thick steel and mortar footing (the center of the building is a giant vaulted ceiling).
Exterior walls are a no-go since they’re 18" thick brick and concrete. Hell, I had to rent Thor’s hammer drill to get through half the 10" thick interior walls.
Occasionally I’m lucky and there happens to be a 70 yr old conduit, like with my better than off-site, on-site backup:
I don’t blame you, that looks like a nightmare. Under no circumstance could anyone talk me personally in to doing that wiring. But it wouldn’t hurt to get a quote from structured cabling contractor to do all new Cat6 drops and get a price on 10Gbps fiber at the same time. Might be cheaper to hire someone to rewire the office than buy a bunch of managed switches 
VLANs are strongly recommended and the proper solution for adding all these IP peripherals to my network, correct? My idea was to have a VLAN for:
- admin workstations
- servers (file, SQL, web)
- POS, user workstations
- 1/2/3D printers and scanners, cc-terminals
- IP Cameras
- IoT
Do you need separate wifi AP’s or are there AP’s that can segregate? IoT is all wifi, but I have an admin laptop and a couple of user laptops.
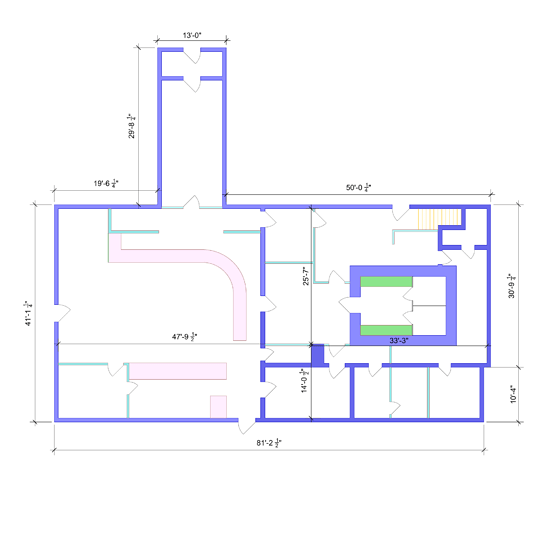
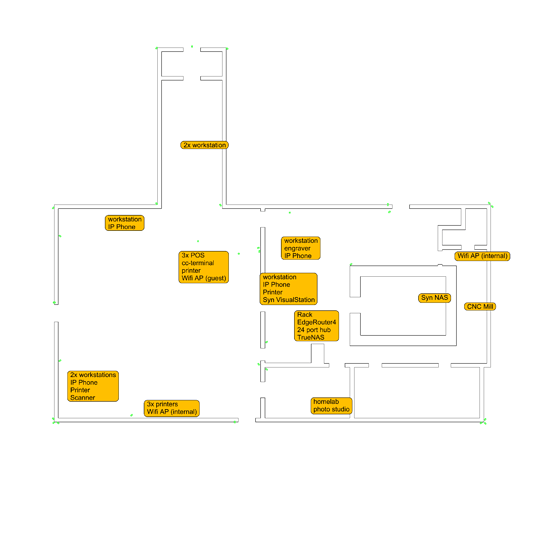
risk, you’ve seen the logical diagram of my current and WIP network. I’ll do a physical layout with inventory in CAD today.
That’s what I was thinking. I wish I had an extra EdgeRouter4 so I learn on a homelab setup with the new switches, VLANs, and firewall config.
MicroTik looks interesting. Do they have any kind of annual licensing for their centralized management?
I didn’t want you to think I was ignoring a valid suggestion for no reason. I’ll prob need to get a quote as I’m leaning towards the SFP+ route. Since I already have at least 1 (if not 4) cat cable home runs at each location, it’ll be easy to use them as leaders to pull one fiber replacement.
… oh sorry, didn’t connect the two threads immediately …
I’m mostly wondering because of the POE stuff and cameras. There’s things where POE is immensely useful, and there’s places e.g. like a home office, where you might need 1-2 POE ports e.g. for a wifi accesspoint maybe and not much else.
@Four0Four suggested going with a single big switch instead of many smaller ones - it’s not unreasonable… depends on - whether or not you already have wiring installed, but it also sidesteps the switch versatility issue. (that way you could probably get away with 2 switches for the whole thing, maybe 3 if you wanted to split off cameras onto a cheap 16 port gigabit unmanaged switch).
–
No, Mikrotik gives you a “Perpetual License” to use their software that’s is included in the device price, and most devices receive updates for a fairly long time.
You use VLAN s for implementing virtual segregation at the layer 2 level when it’s not practical to have physically separated ones. So yes.
You don’t want to overdo it though as all inter VLAN traffic needs to go through a firewall/router and that gets complicated really fast …
You can implement VLAN segregation on most APs nowadays, I am running mikotik switches and ubiquity APs without any issue, with multiple wifi SSID s on segregated networks (home, guests,iot)
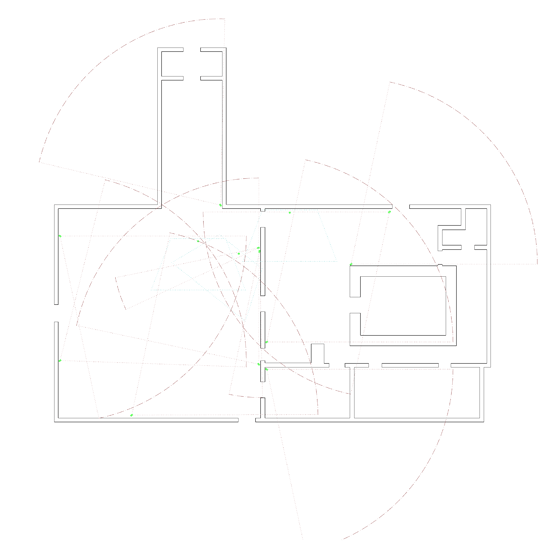
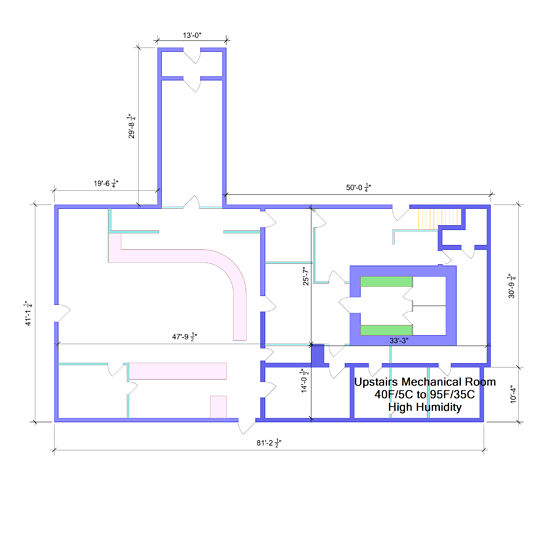
So this is the building layout. Dark blue walls are solid, aqua walls are regular wood-framed, and pink are the showcases.
This is the building inventory with just the solid walls outlined. Green dots are the cameras:
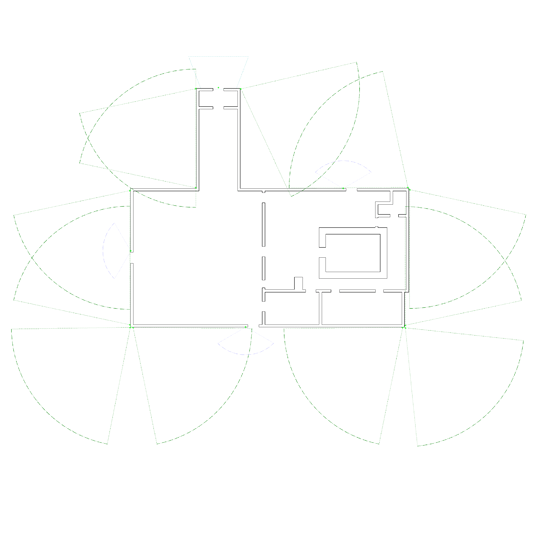
Interior camera FOVs:
Exterior FOVs:
The CAD file is a .3dm (Rhino3D).
Do you happen to have vaulted / panel ceilings or ceiling mounted raceways… that would simplify your cabling setup a lot, to a point where it may be interesting to consider going with 10G/ 25G/40G for workstations today (because fast access to shared storage is cool, no other special reason).
BTW, I don’t think you need a separate guest access point device. Most (probably all) APs support multiple SSIDs ( can put that traffic into a VLAN).
Also, guest network is good for your own phones and other internet only portables.
No, there’s nothing like that. I usually run stuff 25’ up to the attic, then over to the rack outside the vault, and back down 25’. It’s an old suspension ceiling. There are big steel trusses that suspend a steel mesh coated in 1" thick mortar.
You have to hang off the trusses to do anything.
 I didn’t know a copper SFP+ port can go straight to an RJ45, multi-gig card in a PC. So with a switch like this:
I didn’t know a copper SFP+ port can go straight to an RJ45, multi-gig card in a PC. So with a switch like this:
You have 8x 1 gig’s for peripherals, 1x SFP+ for uplink, and 1x SFP+ for a 2.5 gig RJ45 workstation, correct? I thought the extra SFP+ port was for daisy chaining.
I’m also thinking more about a homerun for the cams like @Four0Four was suggesting. All the IP cams are ceiling/roof mounted and could easily run to the mechanical room this picture was taken from:
The room is insulated, but it’s not conditioned space. I’m guessing the average ambient temp in the summer is 80F/25C. Let’s say it’s 95F/35C max. Plus, there’s noticeable humidity (I’m in the south).
The other issue is PoE runs in the 150’ / 50m range. On thin gauge wire, will the cameras work with that much voltage drop? Will the heat from that drop in a 175F/80C attic affect signal quality on 10 Mbps devices like cameras?
The MicroTik 48 port PoE is perfect for the camera home run. It says it’s tested up to 140F/60C, but I’m sure these things are designed for conditioned spaces and not attic mechanical rooms.
You can use the sfp+ port either as trunk (uplink/downlink to another switch or router) or in access mode (connection to a single host on a specific VLAN)
that should be fine.
I am using a combination of these switches for my home. the 4S is used for the IP cameras ans the 2S is used to terminate in each room. The 8S is the central fiber switch.
works well for my use case. especially for vLaning the IoT stuffs and their chattiness.
What is the difference between the CSS and CRS prefix on MicroTik switch model names?
CSS can only run SwOs (Mikrotik Layer 2 switching Os)
CRS models can choose between SwOs and RouterOs, that can do layer3/firewalling/other stuff
All CRS models run SwOs very well , some suck at running RouterOs/doing layer3 because of cpu and power limits, others are way better
SwOs only has a web gui and while straightforward is limited in functionality, Routeros has web gui, cli and a central management plane, and you need it as configuration options are way more and it gets complicated really quickly …
So there isn’t a version of the CSS610-8G-2S+IN with 8x 1 gig with 2x SFP+ that can be managed centrally? I only need level 2 on these switches and was hoping to maintain a single MAC filter list for each VLAN.
The CRS309-1G-8S+IN would be doing the layer3/firewalling between VLANs.
The two big groups I want to segment won’t need any layer 3 stuff. The IPCams (no intra/internet) will be on the same VLAN as one of the synology ports. Guest devices (no intra, yes internet) will connect to the 2nd port on the edgerouter.
The IoT devices will be on a VLAN to lock down their access to the intra/internet. They are chatty but have very little throughput.
Last is the user devices. Not sure if I should segment them. I don’t trust some of the users (there’s no telling a 70 yr old man not to click on things). 100 Mbps is more than enough for these devices (small SMB shares and a SQL db).
If it’s recommended and the CRS309-1G-8S+IN can handle it, I’d do one more VLAN to limit the attack surface of my servers.
If by centrally you mean like the ubiquity controller, then I am afraid none of the Mikrotik devices can be controlled like that with native software (there may e third party solutions, but I have never looked into them) … the winbox app manages one device at a time … nothing like the ubiquity controller where you define your vlans/acls/stuff once and then you apply it to different devices …