It seems they’re slowly adding support to the bioses for that – mine got the option with the update to 1.0.0.6 or 6a. Having said that, a lot of Michael’s segfaults appear to be conftests, and so harmless/desirable.
I noticed in the latest ASrock uefi there is an explicit workaround for a gcc return value. So that’s also a good sign. Is it true Ubuntu exhibits this problem more than most other distros?
Is this the part where we discover the three letter agencies read reflections on trusting trust and there’s stuff lurking around our compilers? Lol
Doubt that’s due to anything more than Ubuntu’s popularity and/or some versions of GCC being more robust than others wrt the generation of these segfaults (I also ran into it less often on a fc23-based VM than on an fc24/25-based one). I’m still surprised that no windows (non-WSL) users have complained about it, though, and/or that it’s run into so little generally – are people who compile/program shit really that scarce, as a percentage of the general (PC enthusiast/PCMR) population?
I’ve been using Gentoo with gcc though I’m using it on a laptop (of course I’m not using Ryzen) honestly from the headaches I’ve had to deal with from Gentoo. I haven’t had an issue since I’ve changed the package accept keyword from ~amd64 to amd64. though i don’t think many issues are going to be fixed on Gentoo. for a distro that is supposed to be rolling release a lot of packages are fairly outdated compared to other RR distros. and I don’t even want to get into it with Funtoo. it’s even worse.
Yeah, from what I’ve seen they seem to be having demographic problems (aka, dying out).
I have been messing around with this today on my 1800x (retail) 1700 (retail) and 1600x (loaner from msi, thanks guys)
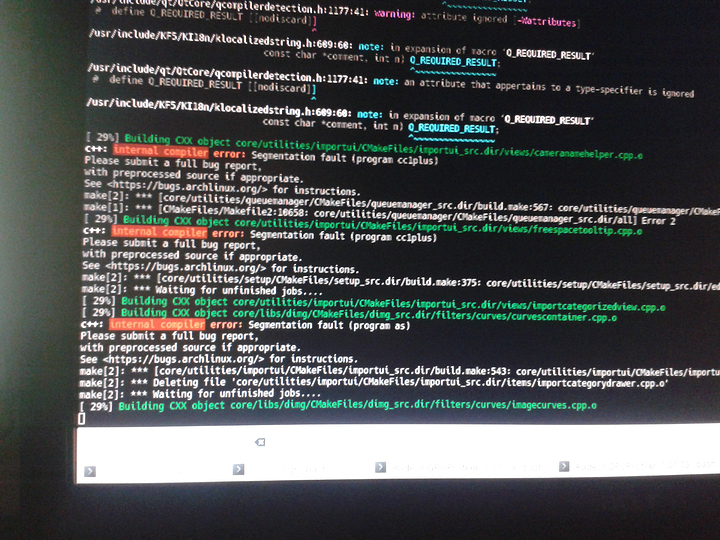
I can cause segfaults all day long with the phoronix test suite but they seem to be in conftest? e.g. not real? with the same image, on x299 I get the same segfaults in conftest.
I have experienced that I’ve had to up my SoC voltage a bit with memory overclocks/xmp but I hvae been testing at purely stock settings today. Testing on ASRock Taichi X370. Testing on Fedora 26 only. I am tempted to live boot ubuntu and see if I can get it to segfault.
I am getting segfaults so I had a bit of a freakout… but then I realized its just conftest? so I think there is something to thise but the signal to noise ratio is too close to 1 for my liking at the moment?
I was running into segfaults on my 1800X + ASUS Prime X370-Pro until I upped the SOC voltage to 1.18v. Now I can go over a day compiling Linux/GCC without segfaults.
Yeah, the conftest stuff is from php – missed that at first as well, sorry about that.
If you want to be sure, I think the best test to run overnight is still this one https://github.com/suaefar/ryzen-test (and if you get segfaults with the ‘kill’ script, try the ‘save’ script next (“I observed that when the processes remain “isolated” in their respective cache domains there seem to be no segfaults.”).
Seems Larabel is in over his head, and also more concerned with generating short-term attention for his products over worries about what drawing so much attention to results that he doesn’t fully understand and that partly constitute false positives will do for his rep in the long term. As #45 would say: #Sad.
I can not for the life of me reproduce these results.
At least nothing aside from the stoopid conftest like everyone else. Which is a non-issue
One surefire way however that I can reproduce a much worse error is by lowering my DRAM Voltage to 1.2V and setting Load Line level 3 while at stock VCore and clocks on some potato Corsair DIMMS.
This will lead to Hard Machine Check Exceptions and resets while at idle. (It’s got to do with IDLE C-states and is completely random) Disabling C-States and or setting a lower Load Line level (level 4) completely avoids this problem.
That said a new tool I’ve recently started using for testing ryzen stability is sandsifter, the x86 processor fuzzer.
I will have a post coming up about that sometime once I’ve figured it all out.
There’s also this:
Some call it a Ryzen bug, but nobody is actually 100% certain that it is one.
https://svnweb.freebsd.org/base?view=revision&revision=321899
Of note also, I have noted that phoronix is also running those same potato Corsair DIMMS with which I was 100% able to get MCE’s:

So I have just managed to get something while compiling Digikam of all things. I wasn’t even looking for a segfault at the time.
Unfortunately I wasn’t logging any more detailed info on that run and I can’t reproduce it since…
89%] Linking CXX executable usexmpsidecar
In file included from /usr/include/qt/QtCore/qglobal.h:45:0,
from /usr/include/qt/QtGui/qtguiglobal.h:43,
from /usr/include/qt/QtWidgets/qtwidgetsglobal.h:43,
from /usr/include/qt/QtWidgets/qscrollarea.h:43,
from /usr/include/qt/QtWidgets/QScrollArea:1,
from /home/rgr/Projects/Digikam/dk/core/showfoto/setup/showfotosetupmetadata.h:29,
from /home/rgr/Projects/Digikam/dk/core/showfoto/setup/showfotosetupmetadata.cpp:24:
/usr/include/c++/7.1.1/type_traits: In instantiation of ‘struct std::remove_cv<QBrush>’:
/usr/include/c++/7.1.1/type_traits:328:12: required from ‘struct std::is_integral<QBrush>’
/usr/include/qt/QtGui/qbrush.h:137:1: required from here
/usr/include/c++/7.1.1/type_traits:1577:67: internal compiler error: Segmentation fault
remove_const<typename remove_volatile<_Tp>::type>::type type;
^~~~
Please submit a full bug report,
with preprocessed source if appropriate.
See <https://bugs.archlinux.org/> for instructions.
make[2]: *** [core/showfoto/CMakeFiles/showfoto.dir/build.make:111: core/showfoto/CMakeFiles/showfoto.dir/setup/showfotosetupmetadata.cpp.o] Error 1
make[2]: *** Waiting for unfinished jobs....
Ok now I think I’m getting somewhere, going to go over what I can dig out of this.
The segfault is not happening specifically for a single piece of code but rather randomly at about the same point during the compilation.
Update, this turned out to be due to unstable RAM configuration.
NOT a CPU Bug.
Holy Bejuzus! Now I really broke stuff.
Ran another digikam compile with more gcc debug options and it led me to this:
Which resulted in a complete Kernel Panic with this being written to the system log:
Aug 07 17:37:15 jupiter kernel: general protection fault: 0000 [#2] PREEMPT SMP
Aug 07 17:37:15 jupiter kernel: Modules linked in: dm_mod dax xfs nilfs2 jfs btrfs xor raid6_pq overlay xt_CHECKSUM iptable_mangle tun bridge stp llc ebtable_filter ebtables xt_pkttype nct6775 hwmon_vid ip6t_REJECT nf_reject_ipv6 nf_log_ipv6 xt_hl ip6t_rt nf_conntrack_ip
Aug 07 17:37:15 jupiter kernel: media fat cryptd mac_hid pcspkr dca mii xt_multiport snd_pcm snd_timer snd ccp soundcore rng_core xt_limit i2c_piix4 xt_tcpudp shpchp xt_addrtype nf_conntrack_ipv4 nf_defrag_ipv4 xt_conntrack wmi 8250_dw tpm_crb i2c_designware_platform i2
Aug 07 17:37:15 jupiter kernel: syscopyarea sysfillrect sysimgblt fb_sys_fops ttm drm vfio_pci irqbypass vfio_virqfd vfio_iommu_type1 vfio
Aug 07 17:37:15 jupiter kernel: CPU: 1 PID: 23041 Comm: cc1plus Tainted: G D O 4.12.4-1-ARCH #1
Aug 07 17:37:15 jupiter kernel: Hardware name: To Be Filled By O.E.M. To Be Filled By O.E.M./X370 Gaming K4, BIOS P3.00 07/07/2017
Aug 07 17:37:15 jupiter kernel: task: ffff927c1063d580 task.stack: ffffacd650604000
Aug 07 17:37:15 jupiter kernel: RIP: 0010:kmem_cache_alloc+0x72/0x1c0
Aug 07 17:37:15 jupiter kernel: RSP: 0018:ffffacd650607c78 EFLAGS: 00010286
Aug 07 17:37:15 jupiter kernel: RAX: 0000000000000000 RBX: 0000000000000000 RCX: 00000000dbff2c81
Aug 07 17:37:15 jupiter kernel: RDX: 00000000dbff2c01 RSI: 00000000dbff2c01 RDI: 000000000001c080
Aug 07 17:37:15 jupiter kernel: RBP: ffffacd650607ca8 R08: ffffffffb722040c R09: fffffffffffff7f0
Aug 07 17:37:15 jupiter kernel: R10: ffffacd650607ee8 R11: 0000000000000000 R12: 00000000014080c0
Aug 07 17:37:15 jupiter kernel: R13: cfff9278f0996a00 R14: ffff927fbe007180 R15: ffff927fbe007180
Aug 07 17:37:15 jupiter kernel: FS: 00007fc27c89a840(0000) GS:ffff927fbe640000(0000) knlGS:0000000000000000
Aug 07 17:37:15 jupiter kernel: CS: 0010 DS: 0000 ES: 0000 CR0: 0000000080050033
Aug 07 17:37:15 jupiter kernel: CR2: 0000000002ad6cc8 CR3: 00000001b7331000 CR4: 00000000003406e0
Aug 07 17:37:15 jupiter kernel: Call Trace:
Aug 07 17:37:15 jupiter kernel: get_empty_filp+0x5c/0x1b0
Aug 07 17:37:15 jupiter kernel: path_openat+0x3d/0x13a0
Aug 07 17:37:15 jupiter kernel: ? __alloc_pages_nodemask+0xbb/0x230
Aug 07 17:37:15 jupiter kernel: ? mem_cgroup_commit_charge+0x7e/0x4f0
Aug 07 17:37:15 jupiter kernel: do_filp_open+0x9b/0x110
Aug 07 17:37:15 jupiter kernel: ? __check_object_size+0xaf/0x1a7
Aug 07 17:37:15 jupiter kernel: ? __alloc_fd+0xb2/0x160
Aug 07 17:37:15 jupiter kernel: do_sys_open+0x1ba/0x250
Aug 07 17:37:15 jupiter kernel: ? do_sys_open+0x1ba/0x250
Aug 07 17:37:15 jupiter kernel: SyS_open+0x1e/0x20
Aug 07 17:37:15 jupiter kernel: entry_SYSCALL_64_fastpath+0x1a/0xa5
Aug 07 17:37:15 jupiter kernel: RIP: 0033:0x7fc27b5cf940
Aug 07 17:37:15 jupiter kernel: RSP: 002b:00007ffff81a2328 EFLAGS: 00000246 ORIG_RAX: 0000000000000002
Aug 07 17:37:15 jupiter kernel: RAX: ffffffffffffffda RBX: 00000000000000c4 RCX: 00007fc27b5cf940
Aug 07 17:37:15 jupiter kernel: RDX: 00000000000001b6 RSI: 0000000000000100 RDI: 00000000026ad840
Aug 07 17:37:15 jupiter kernel: RBP: 000000000000270e R08: 00007fc27a73a010 R09: 0000000000000010
Aug 07 17:37:15 jupiter kernel: R10: 0000000000017a96 R11: 0000000000000246 R12: 00007fc27b890ad8
Aug 07 17:37:15 jupiter kernel: R13: 0000000000000ff0 R14: 0000000002ad5cd0 R15: 00007fc27b890a80
Aug 07 17:37:15 jupiter kernel: Code: 08 48 39 f2 75 e7 48 83 78 10 00 4c 8b 28 0f 84 0f 01 00 00 4d 85 ed 0f 84 06 01 00 00 49 63 46 20 49 8b 3e 48 8d 8a 80 00 00 00 <49> 8b 5c 05 00 4c 89 e8 65 48 0f c7 0f 0f 94 c0 84 c0 74 ab 49
Aug 07 17:37:15 jupiter kernel: RIP: kmem_cache_alloc+0x72/0x1c0 RSP: ffffacd650607c78
Aug 07 17:37:15 jupiter kernel: general protection fault: 0000 [#3] PREEMPT SMP
Aug 07 17:37:15 jupiter kernel: Modules linked in: dm_mod dax xfs nilfs2 jfs btrfs xor raid6_pq overlay xt_CHECKSUM iptable_mangle tun bridge stp llc ebtable_filter ebtables xt_pkttype nct6775 hwmon_vid ip6t_REJECT nf_reject_ipv6 nf_log_ipv6 xt_hl ip6t_rt nf_conntrack_ip
Aug 07 17:37:15 jupiter kernel: media fat cryptd mac_hid pcspkr dca mii xt_multiport snd_pcm snd_timer snd ccp soundcore rng_core xt_limit i2c_piix4 xt_tcpudp shpchp xt_addrtype nf_conntrack_ipv4 nf_defrag_ipv4 xt_conntrack wmi 8250_dw tpm_crb i2c_designware_platform i2
Aug 07 17:37:15 jupiter kernel: syscopyarea sysfillrect sysimgblt fb_sys_fops ttm drm vfio_pci irqbypass vfio_virqfd vfio_iommu_type1 vfio
Aug 07 17:37:15 jupiter kernel: CPU: 1 PID: 28590 Comm: at-spi2-registr Tainted: G D O 4.12.4-1-ARCH #1
Aug 07 17:37:15 jupiter kernel: Hardware name: To Be Filled By O.E.M. To Be Filled By O.E.M./X370 Gaming K4, BIOS P3.00 07/07/2017
Aug 07 17:37:15 jupiter kernel: task: ffff927fb5b45580 task.stack: ffffacd64ce84000
Aug 07 17:37:15 jupiter kernel: RIP: 0010:kmem_cache_alloc_node+0xb4/0x1c0
Aug 07 17:37:15 jupiter kernel: RSP: 0018:ffffacd64ce87ad8 EFLAGS: 00010246
Aug 07 17:37:15 jupiter kernel: RAX: 0000000000000000 RBX: ffff927fb5b45580 RCX: 00000000dbff2c81
Aug 07 17:37:15 jupiter kernel: RDX: 00000000dbff2c01 RSI: 00000000ffffffff RDI: 000000000001c080
Aug 07 17:37:15 jupiter kernel: RBP: ffffacd64ce87b10 R08: ffffffffb7525d0b R09: 0000000000000000
Aug 07 17:37:15 jupiter kernel: R10: ffffffffb788e220 R11: ffff927fb5b45580 R12: 00000000015004c0
Aug 07 17:37:15 jupiter kernel: R13: cfff9278f0996a00 R14: ffff927fbe007180 R15: ffff927fbe007180
Aug 07 17:37:15 jupiter kernel: FS: 00007f0a11df1e80(0000) GS:ffff927fbe640000(0000) knlGS:0000000000000000
Aug 07 17:37:15 jupiter kernel: CS: 0010 DS: 0000 ES: 0000 CR0: 0000000080050033
Aug 07 17:37:15 jupiter kernel: CR2: 0000000002ad6cc8 CR3: 00000007c36e4000 CR4: 00000000003406e0
Aug 07 17:37:15 jupiter kernel: ---[ end trace 3bf91d477d726b26 ]---
Aug 07 17:37:15 jupiter kernel: Call Trace:
Aug 07 17:37:15 jupiter kernel: __alloc_skb+0x5b/0x1e0
Aug 07 17:37:15 jupiter kernel: alloc_skb_with_frags+0x67/0x1c0
Aug 07 17:37:15 jupiter kernel: sock_alloc_send_pskb+0x1ee/0x220
Aug 07 17:37:15 jupiter kernel: ? unix_stream_read_generic+0x26e/0x860
Aug 07 17:37:15 jupiter kernel: unix_stream_sendmsg+0x2a1/0x3b0
Aug 07 17:37:15 jupiter kernel: sock_write_iter+0x95/0x100
Aug 07 17:37:15 jupiter kernel: __do_readv_writev+0x317/0x3f0
Aug 07 17:37:15 jupiter kernel: do_readv_writev+0x8c/0xd0
Aug 07 17:37:15 jupiter kernel: ? __fget+0x6e/0x90
Aug 07 17:37:15 jupiter kernel: vfs_writev+0x30/0x50
Aug 07 17:37:15 jupiter kernel: ? vfs_writev+0x30/0x50
Aug 07 17:37:15 jupiter kernel: do_writev+0x61/0xf0
Aug 07 17:37:15 jupiter kernel: SyS_writev+0x10/0x20
Aug 07 17:37:15 jupiter kernel: entry_SYSCALL_64_fastpath+0x1a/0xa5
Aug 07 17:37:15 jupiter kernel: RIP: 0033:0x7f0a1048a96d
Aug 07 17:37:15 jupiter kernel: RSP: 002b:00007ffe011c1fa0 EFLAGS: 00000293 ORIG_RAX: 0000000000000014
Aug 07 17:37:15 jupiter kernel: RAX: ffffffffffffffda RBX: 00000000010a9aa0 RCX: 00007f0a1048a96d
Aug 07 17:37:15 jupiter kernel: RDX: 0000000000000003 RSI: 00007ffe011c2130 RDI: 0000000000000005
Aug 07 17:37:15 jupiter kernel: RBP: 00007ffe011c24f0 R08: 0000000001077268 R09: 00007ffe011c23ac
Aug 07 17:37:15 jupiter kernel: R10: 0000001000001003 R11: 0000000000000293 R12: 0000000000000000
Aug 07 17:37:15 jupiter kernel: R13: 0000000001093b30 R14: 0000000001089e30 R15: 0000000000000000
Aug 07 17:37:15 jupiter kernel: Code: 80 00 00 49 89 c5 74 4c 48 85 c0 74 47 49 63 56 1c 31 f6 4c 89 ef e8 0c c5 14 00 eb 37 49 63 46 20 49 8b 3e 48 8d 8a 80 00 00 00 <49> 8b 5c 05 00 4c 89 e8 65 48 0f c7 0f 0f 94 c0 84 c0 0f 84 68
Aug 07 17:37:15 jupiter kernel: RIP: kmem_cache_alloc_node+0xb4/0x1c0 RSP: ffffacd64ce87ad8
Aug 07 17:37:15 jupiter kernel: ---[ end trace 3bf91d477d726b27 ]---
Aug 07 17:37:15 jupiter kernel: general protection fault: 0000 [#4] PREEMPT SMP
Aug 07 17:37:15 jupiter kernel: Modules linked in: dm_mod dax xfs nilfs2 jfs btrfs xor raid6_pq overlay xt_CHECKSUM iptable_mangle tun bridge stp llc ebtable_filter ebtables xt_pkttype nct6775 hwmon_vid ip6t_REJECT nf_reject_ipv6 nf_log_ipv6 xt_hl ip6t_rt nf_conntrack_ip
Aug 07 17:37:15 jupiter kernel: media fat cryptd mac_hid pcspkr dca mii xt_multiport snd_pcm snd_timer snd ccp soundcore rng_core xt_limit i2c_piix4 xt_tcpudp shpchp xt_addrtype nf_conntrack_ipv4 nf_defrag_ipv4 xt_conntrack wmi 8250_dw tpm_crb i2c_designware_platform i2
Aug 07 17:37:15 jupiter kernel: syscopyarea sysfillrect sysimgblt fb_sys_fops ttm drm vfio_pci irqbypass vfio_virqfd vfio_iommu_type1 vfio
Aug 07 17:37:15 jupiter kernel: CPU: 1 PID: 23029 Comm: cc1plus Tainted: G D O 4.12.4-1-ARCH #1
Aug 07 17:37:15 jupiter kernel: Hardware name: To Be Filled By O.E.M. To Be Filled By O.E.M./X370 Gaming K4, BIOS P3.00 07/07/2017
Aug 07 17:37:15 jupiter kernel: task: ffff9279d36b8e40 task.stack: ffffacd6505fc000
Aug 07 17:37:15 jupiter kernel: RIP: 0010:kmem_cache_alloc+0x72/0x1c0
Aug 07 17:37:15 jupiter kernel: RSP: 0018:ffffacd6505ffc78 EFLAGS: 00010286
Aug 07 17:37:15 jupiter kernel: RAX: 0000000000000000 RBX: 0000000000000000 RCX: 00000000dbff2d81
Aug 07 17:37:15 jupiter plasmashell[28447]: log_klipper: Checking clip data
Aug 07 17:37:15 jupiter kernel: RDX: 00000000dbff2d01 RSI: 00000000dbff2d01 RDI: 000000000001c080
Aug 07 17:37:15 jupiter kernel: RBP: ffffacd6505ffca8 R08: ffffffffb722040c R09: fffffffffff80000
Aug 07 17:37:15 jupiter kernel: R10: ffffacd6505ffee8 R11: 0000000000000000 R12: 00000000014080c0
Aug 07 17:37:15 jupiter kernel: R13: cfff9278f0996a00 R14: ffff927fbe007180 R15: ffff927fbe007180
Aug 07 17:37:15 jupiter kernel: FS: 00007f79128f0840(0000) GS:ffff927fbe640000(0000) knlGS:0000000000000000
Aug 07 17:37:15 jupiter kernel: CS: 0010 DS: 0000 ES: 0000 CR0: 0000000080050033
Aug 07 17:37:15 jupiter kernel: CR2: 00007f790e982000 CR3: 00000001fc8e3000 CR4: 00000000003406e0
Aug 07 17:37:15 jupiter kernel: Call Trace:
Aug 07 17:37:15 jupiter kernel: get_empty_filp+0x5c/0x1b0
Aug 07 17:37:15 jupiter kernel: path_openat+0x3d/0x13a0
Aug 07 17:37:15 jupiter kernel: ? __alloc_pages_nodemask+0xbb/0x230
Aug 07 17:37:15 jupiter kernel: ? mem_cgroup_commit_charge+0x7e/0x4f0
Aug 07 17:37:15 jupiter kernel: do_filp_open+0x9b/0x110
Aug 07 17:37:15 jupiter kernel: ? lru_cache_add_active_or_unevictable+0x36/0xb0
Aug 07 17:37:15 jupiter kernel: ? __handle_mm_fault+0x88d/0xfb0
Aug 07 17:37:15 jupiter kernel: ? _copy_to_user+0x2a/0x40
Aug 07 17:37:15 jupiter kernel: ? __check_object_size+0xaf/0x1a7
Aug 07 17:37:15 jupiter kernel: ? __alloc_fd+0xb2/0x160
Aug 07 17:37:15 jupiter kernel: do_sys_open+0x1ba/0x250
Aug 07 17:37:15 jupiter kernel: ? do_sys_open+0x1ba/0x250
Aug 07 17:37:15 jupiter kernel: SyS_open+0x1e/0x20
Aug 07 17:37:15 jupiter kernel: entry_SYSCALL_64_fastpath+0x1a/0xa5
Aug 07 17:37:15 jupiter kernel: RIP: 0033:0x7f791162a940
Aug 07 17:37:16 jupiter kernel: RSP: 002b:00007ffd363f0518 EFLAGS: 00000246 ORIG_RAX: 0000000000000002
Aug 07 17:37:16 jupiter kernel: RAX: ffffffffffffffda RBX: 0000000000000070 RCX: 00007f791162a940
Aug 07 17:37:16 jupiter kernel: RDX: 00000000000001b6 RSI: 0000000000000000 RDI: 000000000324f280
Aug 07 17:37:16 jupiter kernel: RBP: 0000000000000000 R08: 0000000000000008 R09: 0000000000000001
Aug 07 17:37:16 jupiter kernel: R10: 00000000018af5cc R11: 0000000000000246 R12: 0000000000000000
Aug 07 17:37:16 jupiter kernel: R13: 0000000000000010 R14: 000000000e6f188d R15: 0000000000000000
Aug 07 17:37:16 jupiter kernel: Code: 08 48 39 f2 75 e7 48 83 78 10 00 4c 8b 28 0f 84 0f 01 00 00 4d 85 ed 0f 84 06 01 00 00 49 63 46 20 49 8b 3e 48 8d 8a 80 00 00 00 <49> 8b 5c 05 00 4c 89 e8 65 48 0f c7 0f 0f 94 c0 84 c0 74 ab 49
Aug 07 17:37:16 jupiter kernel: RIP: kmem_cache_alloc+0x72/0x1c0 RSP: ffffacd6505ffc78
Aug 07 17:37:16 jupiter kernel: general protection fault: 0000 [#5] PREEMPT SMP
Aug 07 17:37:16 jupiter kernel: Modules linked in: dm_mod dax xfs nilfs2 jfs btrfs xor raid6_pq overlay xt_CHECKSUM iptable_mangle tun bridge stp llc ebtable_filter ebtables xt_pkttype nct6775 hwmon_vid ip6t_REJECT nf_reject_ipv6 nf_log_ipv6 xt_hl ip6t_rt nf_conntrack_ip
Aug 07 17:37:16 jupiter kernel: media fat cryptd mac_hid pcspkr dca mii xt_multiport snd_pcm snd_timer snd ccp soundcore rng_core xt_limit i2c_piix4 xt_tcpudp shpchp xt_addrtype nf_conntrack_ipv4 nf_defrag_ipv4 xt_conntrack wmi 8250_dw tpm_crb i2c_designware_platform i2
Aug 07 17:37:16 jupiter kernel: syscopyarea sysfillrect sysimgblt fb_sys_fops ttm drm vfio_pci irqbypass vfio_virqfd vfio_iommu_type1 vfio
Aug 07 17:37:16 jupiter kernel: CPU: 1 PID: 9816 Comm: teamviewerd Tainted: G D O 4.12.4-1-ARCH #1
Aug 07 17:37:16 jupiter kernel: ---[ end trace 3bf91d477d726b28 ]---
Aug 07 17:37:16 jupiter kernel: Hardware name: To Be Filled By O.E.M. To Be Filled By O.E.M./X370 Gaming K4, BIOS P3.00 07/07/2017
Aug 07 17:37:16 jupiter kernel: task: ffff927fb7f33900 task.stack: ffffacd65254c000
Aug 07 17:37:16 jupiter plasmashell[28447]: log_klipper: Synchronize? false
Aug 07 17:37:16 jupiter kernel: RIP: 0010:kmem_cache_alloc+0x72/0x1c0
Aug 07 17:37:16 jupiter kernel: RSP: 0018:ffffacd65254fc58 EFLAGS: 00210286
Aug 07 17:37:16 jupiter kernel: RAX: 0000000000000000 RBX: 0000000000000000 RCX: 00000000dbff2d81
Aug 07 17:37:16 jupiter kernel: RDX: 00000000dbff2d01 RSI: 00000000dbff2d01 RDI: 000000000001c080
Aug 07 17:37:16 jupiter kernel: RBP: ffffacd65254fc88 R08: ffffffffb722040c R09: ffffffffffff8000
Aug 07 17:37:16 jupiter kernel: R10: ffffacd65254fec8 R11: 0000000000000000 R12: 00000000014080c0
Aug 07 17:37:16 jupiter kernel: R13: cfff9278f0996a00 R14: ffff927fbe007180 R15: ffff927fbe007180
Aug 07 17:37:16 jupiter kernel: FS: 0000000000000000(0000) GS:ffff927fbe640000(0063) knlGS:00000000eafffb40
Aug 07 17:37:16 jupiter kernel: CS: 0010 DS: 002b ES: 002b CR0: 0000000080050033
Aug 07 17:37:16 jupiter kernel: CR2: 00007f790e982000 CR3: 00000007f6053000 CR4: 00000000003406e0
Aug 07 17:37:16 jupiter kernel: Call Trace:
Aug 07 17:37:16 jupiter kernel: ? mntput_no_expire+0x2c/0x1a0
Aug 07 17:37:16 jupiter kernel: get_empty_filp+0x5c/0x1b0
Aug 07 17:37:16 jupiter kernel: path_openat+0x3d/0x13a0
Aug 07 17:37:16 jupiter kernel: ? _copy_to_user+0x2a/0x40
Aug 07 17:37:16 jupiter kernel: ? tty_mode_ioctl+0x1b6/0x4c0
Aug 07 17:37:16 jupiter kernel: ? ___slab_alloc+0xef/0x4e0
Aug 07 17:37:16 jupiter kernel: do_filp_open+0x9b/0x110
Aug 07 17:37:16 jupiter kernel: ? tty_release+0x336/0x600
Aug 07 17:37:16 jupiter kernel: ? __check_object_size+0xaf/0x1a7
Aug 07 17:37:16 jupiter kernel: ? __alloc_fd+0xb2/0x160
Aug 07 17:37:16 jupiter kernel: do_sys_open+0x1ba/0x250
Aug 07 17:37:16 jupiter kernel: ? do_sys_open+0x1ba/0x250
Aug 07 17:37:16 jupiter kernel: ? task_work_run+0x76/0x90
Aug 07 17:37:16 jupiter kernel: compat_SyS_open+0x1b/0x20
Aug 07 17:37:16 jupiter kernel: do_fast_syscall_32+0x96/0x180
Aug 07 17:37:16 jupiter kernel: entry_SYSCALL_compat+0x3b/0x40
Aug 07 17:37:16 jupiter kernel: RIP: 0023:0xf7721db9
Aug 07 17:37:16 jupiter kernel: RSP: 002b:00000000eafff084 EFLAGS: 00200293 ORIG_RAX: 0000000000000005
Aug 07 17:37:16 jupiter kernel: RAX: ffffffffffffffda RBX: 00000000086ef02d RCX: 0000000000000000
Aug 07 17:37:16 jupiter kernel: RDX: 0000000000000000 RSI: 000000000960d180 RDI: 00000000086ef02d
Aug 07 17:37:16 jupiter kernel: RBP: 00000000eafff0c8 R08: 0000000000000000 R09: 0000000000000000
Aug 07 17:37:16 jupiter kernel: R10: 0000000000000000 R11: 0000000000000000 R12: 0000000000000000
Aug 07 17:37:16 jupiter kernel: R13: 0000000000000000 R14: 0000000000000000 R15: 0000000000000000
Aug 07 17:37:16 jupiter kernel: Code: 08 48 39 f2 75 e7 48 83 78 10 00 4c 8b 28 0f 84 0f 01 00 00 4d 85 ed 0f 84 06 01 00 00 49 63 46 20 49 8b 3e 48 8d 8a 80 00 00 00 <49> 8b 5c 05 00 4c 89 e8 65 48 0f c7 0f 0f 94 c0 84 c0 74 ab 49
Aug 07 17:37:16 jupiter kernel: RIP: kmem_cache_alloc+0x72/0x1c0 RSP: ffffacd65254fc58
jesus christ.
The AMD threads are saying they’re getting segfaults once every 400ish runs on gst-plugins-bad-1.10.4 so, you’re probably going to have to run it a fair few times in order to get the exception again.
read the next post… nevermind
With Digikam, I’m now able to get it every single time.
Linux (kernel) version, GCC version, compilation options?
Kernel
Linux jupiter 4.12.4-1-ARCH #1 SMP PREEMPT Fri Jul 28 18:54:18 UTC 2017 x86_64 GNU/Linux
gcc
gcc (GCC) 7.1.1 20170630
Latest digikam git release. (This is not so simple to setup)
Compile options:
It’s very basic 
make -j16
Ok So I reset my UEFI config to some clean settings first of all.
Previously it was rather tightly optimized for performance.
Timings are now loose, CMD Rate is now 2T.
All Voltage’s Clocks and Load Line Calibrations on Auto.
Ram at 2400MHz.
Probably should have done this first.
Going to see if I get something now.
UPDATE:
Well I’ll be Damned. No segfaults so far.
Looks like my RAM timings weren’t stable. Could also be the Load Line Settings, I’ll have to test if 1T cmd rate can trigger it again. If not that then the next thing.
I thought I was onto something here…
I posted this in another thread, relevant in this situation:
If you are using GCC version 5.x or lower you will have problems. (in this situation, I believe GCC 7.x is more appropriate though)
If you are using kernel 4.10 or lower, you will have problems.
If you don’t have the latest BIOS, you will have problems.
If the ram configuration (voltage and timing) is incorrectly set, you will have problems.