I think for most people its the GUI quality. PIhole is much simpler to interact with.
That’s certainly true, pihole webUI is in a different league then pfsense’s unbound/pfblocker.
Now I am considering switching back to pihole, hmm.
I was already looking at doing a build like this, with Proxmox and PCIe passthrough of a 4 port NIC. Currently I have PFSense running baremetal on a Dell Micro 5060 and its good enough but after working with pfBlocker I decided Pihole probably would be simpler, problem is I dont want yet another baremetal device for it.
So VM’s for these devices makes lots of sense. I may set this all up and then just move it back to the Dell Micro but make it a VM this time so I can run a few different services on that same little very under used PC.
But I want to store ALL THE GAMES LOL. No but really it would be useful with three gaming pcs in the house its easy to hit a data cap.
I built a forbidden router using a Dell R210 is this week. XCP-NG running a pfSense vm and a RHEL vm with podman for container management. I might change back to portainer but I haven’t decided yet
but how is it though?
Adjusting to XCP-NG is a little bit of an endeavor but I am extremely pleased with everything so far.
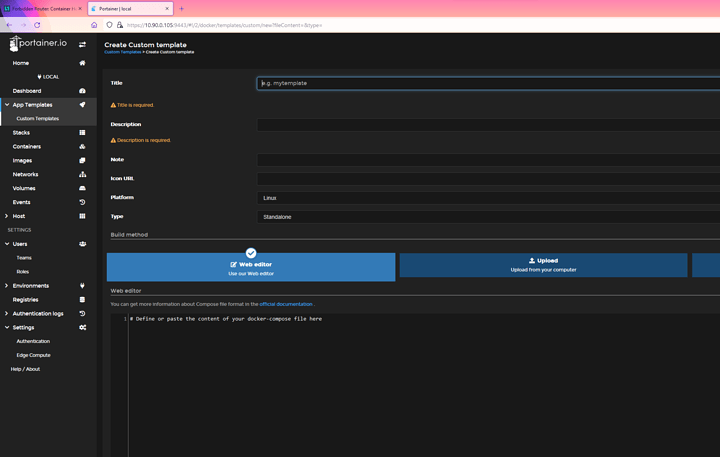
Is this approximately what you are looking for? Portainer allows pasting docker-compose ymls into an app template which seems close enough to me (unless i am missing an advantage of the docker-run approach over docker-compose, which is very possible)
Also about ready to post my double forbidden router - featuring threadripper as a server…
Yes I am happy with portainer, I thought I had broll of this. I meant as a side by side with truenas’ gui for contaieners., Another video I was working on same time as this one
It’s like they are trying to reinvent the wheel with e gui and didn’t even look at portainer
IDK if I am sold on Podman/Cockpit. Honestly Portainer on a Debian 11 vm seems like a smoother experience imo but I am pretty new to containerization.
EDIT: changed podman to portainer.
i think that when I build a forbidden router I want to add a squid proxy server in the mix.
but ive always had a time figuring out how to do it transparently to the users…
Yeah agreed - portainer is pretty awesome and also very easy to get into. Have you ever considered featuring more ebterprise-oriented/difficult to setup platforms like openshift/oks on-prem on the channel?
When I happened onto this project, this is exactly what I want to do to at the network level block Windows 10 and 11 telemetry within a VM virtual interface LAN, so pfsense is the only VM with physical access to the NIC.
Creating JBOD arrays is the thing I currently trust unRAID to do because this is, as you say, a deep rabbit hole.
Sorry Mach3.2 hit reply to you instead first time. No way to unlink a reply after hitting send. So deleted it. Cheers.
It’s impossible to do it transparently to the end user. Wan accelerators can’t cache encrypted traffic. They are proxies and must be their own certificate authority. The proxy’s cert must be loaded to each client machine. You can’t cache something you can’t read. You connect to the proxy using the cert for the proxy verified by the CA on the proxy. The proxy then creates it’s own ssl using the third party ssl of site you’re going to. It gets the unencrtpyed version of what you want then re-encrypts using it’s own certificate. It can only do that if clients below the proxy have accepted the proxy as a CA.
You can still cache unencrypted traffic but most internet traffic is encrypted.
Anyone toss opinions about pfsense vs opnsense. I’m discovering that opnsense has made manually editing unbound.conf directly an amazing pita. And with this setup it’s not like we can’t switch routers on a whim.
Instead of using the dns of lancache, uklans-github has the domains and a script for generating unbound and dnsmasq configs. Thinking I would add that to opnsense as I’m already running unbound with a few modest gui added redirects. No sir. You may not manually edit configs. You must learn how the gui template works instead of just writing the unbound config you already know… my poor free time.
Proof reading this some will argure that a proxy does not need to be it’s own CA another device can be your CA. Opnsense has a surprisingly good gui for that. But still same principle applies, you’re adding a root CA to your clients.
For further reading, check out man-in-the-middle in the enterprise networking world that’s called ‘break and inspect’
Im not worried about caching… i just wanted squid for url/content filtering
Potato potato
Unless you just want to block it at dns
but at dns level
the whole site is blocked… with squid you can do more precise like certain /r on reddit, right?
Yep.
good
i was hoping so. I have kids and my plan is to setup a separate wifi for them that is default block unless on the “okay” list.
That’s a solid idea. I was thinking bout this subject the other day.