I’ve been writing at this for almost 7 hours straight, I need a dang break!
It’s a lot to take on. Take your time.
Need 3 more  on OP to get a badge. Any donators?
on OP to get a badge. Any donators?
Also, added some pics yesterday. Still need to do the IPv6 stuff, which I haven’t yet implemented even on my network.
Fantastic write up. When I have some time I think this is what I need to get started. I will have to learn how to utilize my domain name (I think I can use this for security? Recursive dns with pi-hole?)… I also have to utilize wifi to connect part of my network, so I think I’ll need to use a Cisco managed switch before the AP.
I also started nginx on another pc for testing as I have no idea what to do with it. Think it applies to above for recursive dns, maybe https for home net?.. I’m kind of at a loss. I have wayyyy more reading to do.
Sadly, I have listed all my hardware so there goes that opsec item lol.
This is only a half developed post… I have much more to add once I attempt to figure things out myself first and I have time. Wife took today of work worrying about house sale… But I hope to have some time to mess around today with it.
nginx is a web server that can be used as a reverse proxy. No idea how it related to recursive DNS. Looking through PLL’s guide, it appears nginx is only used for the DNS over TLS HTTPS part, meaning: instead of using unencrypted UDP packets to query a DNS server about a DNS record, you are using TCP packets encrypted with TLS (https) to query a web server about a DNS record. I think this is quite the endeavor, I’ll probably try it in the future, but I don’t have much against forwarder DNS (the default configurations on home routers, where you forward the query to a DNS cacher, like Google, Cloudflare or most commonly ISP DNS).
Telling people the brands and software used isn’t necessarily bad opsec. It becomes bad opsec when you tell every piece of software you are using, so it’s preferable you say none. As for brands, just “Cisco” tells us nothing. Just don’t mention model and especially not firmware. And keep your software up to date.
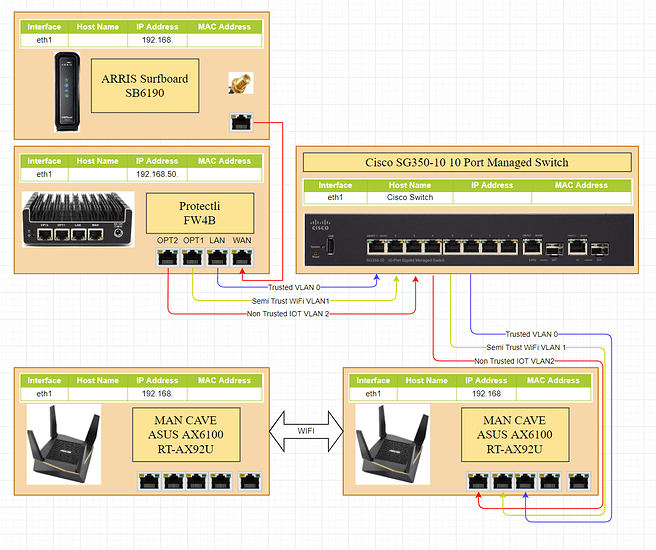
If I understand your guide correctly, This is what my network should look like for a simple version.
I rely on the wifi AP to relay information via its mesh network because I do not have wires in this house, and I think I will have to in the apartment.
Would I just need one wire to the AP? and would the AP relay VLAN tags?
I believe I will also need to design IP’s and Subnets to help keep things organized. I have been reading up on that but the math for whatever reason does not make sense to me. I haven’t had a chance to read the chapter on it front to back, so maybe I am missing something.
Nope, you just bridged the LAN with SEMI-TRUSTED with UNTRUSTED on the WiFi AP. Consumer routers / APs don’t know what vLAN is, so you will need 2 different APs for each vLAN (2 because I prefer LAN not be wireless, so 1 AP for UNTRUSTED and 1 AP for SEMI-TRUSTED). You only connect SEMI-TRUSTED to the WiFi AP. And yeah, they go in a LAN port, after you disable DHCP on the WiFi router (or if they have a dedicated “AP mode”).
Depending on your setup, you may not need the UNTRUSTED network to be wireless. Do you have smart light bulbs and other Internet-of-Junk devices? 
Sadly yes I do. I also have wireless solar cameras. I was hoping to find a way to cut those off from the internet/and keep them on the LAN only unless its passed securely. Then also some alexa devices (I know I know), figured there has to be a way to secure their traffic as well. I also have a subscription to a VPN (PIA) I should be able to utilize as well.
That might be possible because I forgot I had a linksys mesh system as well I can put alexa and cameras on.
Now is it possible to have subnets for each vlan? IE (have a IP range for trusted, Semi, and un trusted?)? Or is that redundant or less secure?
The only way is for each vLAN to have its own subnet. The router’s job is to route traffic between subnets, which are on different vLANs.
e.g. trusted = 192.168.100.0/24
untrusted = 192.168.104.0/24
semi-trusted = 192.168.101.0/24
Very nice, that makes sense. I’ll have to try that.
I forgot to mention that every port needs to be in Mode Access. If you make a server that you want to have access / bridge connections to VMs from both LAN and UNTRUSTED, only set that server’s port (on the switch) in Trunk and allow the 2 vLANs only.
So, for testing… What would be the best way for me to run a setup like this?
Or should I go for a physical connection to the LAN port on the Protectili? I know you said you have used cisco switches, have you ever had a problem with the updates saying the Firmware Image was too large?
Or is this not possible because I already have a router “up stream” (not sure if thats the right term) of the firewall?
Would it be easiest to set the “Default Gateway” on the asusrock edge PC to the IP of the LAN on the firewall? or handle it with the switch and connect port 2 to port 3 someway?
Know I’m kinda lost here…
No, but I’ve read that if you have enough storage and RAM available, you should rename the newer image to something that goes alphabetically before the old image (like from “ios-123.bin” to “aios-123.bin”), as Cisco apparently loads things in alphabetical order.
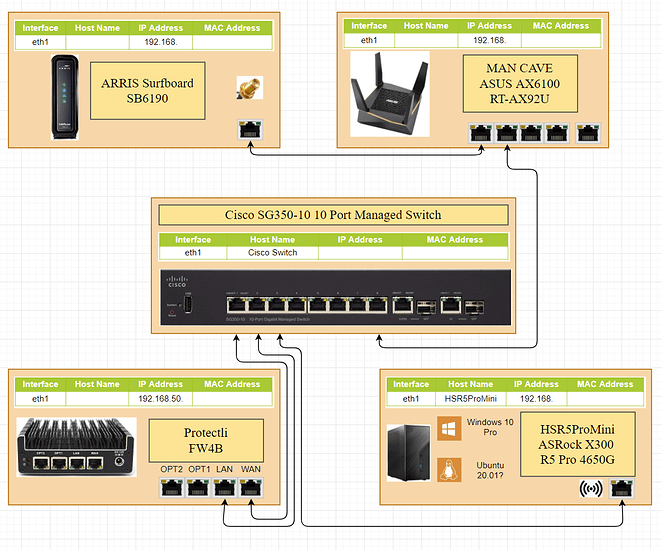
The current map makes the network between the Asus router and the Protectli available on the switch. If don’t you intend to connect other wired devices or VMs to the main Asus network, or more than wired 2 devices, then I suggest you plug the LAN from Asus directly to the WAN from Protectli to save some switch ports. But if you want to make it available to say, Proxmox, then keep this configuration.
You’ll have:
- port 8 mode access in vLAN Asus → Asus LAN port
- port 1 mode access in vLAN Asus → Protectli WAN port
- port 2 mode trunk with vLANs LAN, semi-trusted and untrusted → Protectli LAN port
- port 3 mode trunk with vLANs LAN, semi-trusted, untrusted and Asus (so that you can make the pseudo-DMZ available to Proxmox VMs, it could we worth it for testing some stuff or just pure learning) → Proxmox
I personally used all 4 ports from my firewall to the switch and had the switch ports in mode access, but that’s because I have a 48 port switch (and about 20 of them occupied). But there’s nothing wrong with using vLANs, just that the stuff behind will be limited to 1Gbps total, instead of 1Gbps per subnet. This is ok if you want to save switch ports (to connect other devices).
Also, the attached image doesn’t have labels, but I guess it should be obvious that the Arris port should go to the Asus WAN port.
Really a great write-up on this for someone who really has no experience with networking and firewall rules this helps clarify A LOT.
I do apologize for some of the stupid questions as this really did answer alot once I made it to the section I had a question on (I tended to get ahead of myself/and already have a hard time keeping a train of thought).
To anyone else attempting this I highly recommend reading it through at least once if not twice in it’s entirety (including blurred out points at least on the second read) before you implement or follow the guide. A lot is explained as you go when it’s needed and not before. I assure you the answer to your question is probably there somewhere.
I really should have checked these forums first, as I got super frustrated with setting up my IPv6 stack. I’m not sure if the tutorial would have helped though, since I’m doing everything on a basic Void Linux install. I ended up going with dnsmasq and dhcpcd for getting and assigning IP addresses. I wrote a tutorial myself, in case anyone is trying to do this with a custom Linux router:
Love that you’re using Void. Anyway, I’ll have to check your ipv6 rules, but this project is currently on-hold for now, because I don’t have access to my router at this point in time (and probably won’t for a while). But I will come back to it.
The problem with my tutorial is that it’s split into two parts: the first is the basics, which I should have taken care of, doing the ipv6 rules recommended by the RFCs, and the second part for more advanced users, where I want to block certain traffic (like ICMP v6 echo requests / replies, that are apparently recommended to be allowed). I have waited to write the second part along with the first one, which was a little dumb on my part.
Thank you for your write-up tough, I really appreciate contributions!
I tried to enable DHCPv6 and router advertisement on my internal network, and I set the interfaces to “monitor WAN” in pfSense and somehow I managed to get myself locked out of my network. Somehow, pfSense is so ridiculous that if IPv6 is not working properly, neither is IPv4. How in the world?..
Anyway, the project is still on-hold, I’ll probably have to do a virtual network at some point and continue this project. It’s been a royal PITA, but I don’t like letting things unfinished.
SOOOO… now that I have a better understanding and I’m not completely illiterate to the terminology I was able to follow this guide very easily.
I originally didnt have the WAN rules and was able to set those up no problem.
Thanks again for such an amazing guide for the lay person my friend.
This is still incomplete and I’m ashamed of it, but I don’t have the infrastructure to finish it at this point in time. REEEEEEEE
Dont be ashamed… that was a ton of work you put in!!! Id write more but wife took off work today lol