Just bought and (kinda) set up my new home network with pfSense on a Protectli device with a Unifi Switch 8 PoE & AP-AC-LR and the controller in a docker container on my PC. My intent is to set up VLANs for IOT crap and Guest on wifi, with those restricted from my main LAN. I’ve got things mostly working, but am unable to get anything connecting to the AP to access DNS.
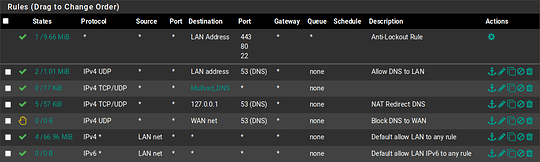
These are my firewall and NAT rules.
TRANSLATION RULES:
no nat proto carp all
nat-anchor "natearly/*" all
nat-anchor "natrules/*" all
nat on em0 inet from 127.0.0.0/8 to any port = isakmp -> x.x.x.x static-port
nat on em0 inet from 127.0.0.0/8 to any -> x.x.x.x port 1024:65535
nat on em0 inet6 from ::1 to any port = isakmp -> (em0) round-robin static-port
nat on em0 inet6 from ::1 to any -> (em0) port 1024:65535 round-robin
nat on ovpnc1 inet from 192.168.5.0/24 to any -> 10.10.0.4 port 1024:65535
nat on ovpnc1 inet from 10.1.10.0/24 to any -> 10.10.0.4 port 1024:65535
nat on ovpnc1 inet from 192.168.20.0/24 to any -> 10.10.0.4 port 1024:65535
no rdr proto carp all
rdr-anchor "relayd/*" all
rdr-anchor "tftp-proxy/*" all
rdr on em1 inet proto tcp from any to ! 192.168.5.1 port = domain -> 127.0.0.1
rdr on em1 inet proto udp from any to ! 192.168.5.1 port = domain -> 127.0.0.1
rdr on em1.10 inet proto tcp from any to ! 10.1.10.1 port = domain -> 127.0.0.1
rdr on em1.10 inet proto udp from any to ! 10.1.10.1 port = domain -> 127.0.0.1
rdr on em1.20 inet proto tcp from any to ! 192.168.20.1 port = domain -> 127.0.0.1
rdr on em1.20 inet proto udp from any to ! 192.168.20.1 port = domain -> 127.0.0.1
rdr-anchor "miniupnpd" all
FILTER RULES:
scrub on em0 all fragment reassemble
scrub on em1 all fragment reassemble
scrub on em1.10 all fragment reassemble
scrub on em1.20 all fragment reassemble
scrub on ovpnc1 all fragment reassemble
anchor "relayd/*" all
anchor "openvpn/*" all
anchor "ipsec/*" all
pass in quick on lo0 inet6 all flags S/SA keep state label "pass IPv6 loopback"
pass out quick on lo0 inet6 all flags S/SA keep state label "pass IPv6 loopback"
block drop in log quick inet6 all label "Block all IPv6"
block drop out log quick inet6 all label "Block all IPv6"
block drop in log quick inet from 169.254.0.0/16 to any label "Block IPv4 link-local"
block drop in log quick inet from any to 169.254.0.0/16 label "Block IPv4 link-local"
block drop in log inet all label "Default deny rule IPv4"
block drop out log inet all label "Default deny rule IPv4"
block drop in log inet6 all label "Default deny rule IPv6"
block drop out log inet6 all label "Default deny rule IPv6"
block drop log quick inet proto tcp from any port = 0 to any label "Block traffic from port 0"
block drop log quick inet proto udp from any port = 0 to any label "Block traffic from port 0"
block drop log quick inet proto tcp from any to any port = 0 label "Block traffic to port 0"
block drop log quick inet proto udp from any to any port = 0 label "Block traffic to port 0"
block drop log quick from <snort2c> to any label "Block snort2c hosts"
block drop log quick from any to <snort2c> label "Block snort2c hosts"
block drop in log quick proto tcp from <sshguard> to (self) port = ssh label "sshguard"
block drop in log quick proto tcp from <sshguard> to (self) port = https label "GUI Lockout"
block drop in log quick from <virusprot> to any label "virusprot overload table"
pass in quick on em0 proto udp from any port = bootps to any port = bootpc keep state label "allow dhcp client out WAN"
pass out quick on em0 proto udp from any port = bootpc to any port = bootps keep state label "allow dhcp client out WAN"
block drop in log quick on em0 from <bogons> to any label "block bogon IPv4 networks from WAN"
block drop in log on ! em0 inet from 24.229.245.0/24 to any
block drop in log inet from x.x.x.x to any
block drop in log on em0 inet6 from fe80::2e0:67ff:fe18:1978 to any
block drop in log quick on em0 inet from 10.0.0.0/8 to any label "Block private networks from WAN block 10/8"
block drop in log quick on em0 inet from 127.0.0.0/8 to any label "Block private networks from WAN block 127/8"
block drop in log quick on em0 inet from 172.16.0.0/12 to any label "Block private networks from WAN block 172.16/12"
block drop in log quick on em0 inet from 192.168.0.0/16 to any label "Block private networks from WAN block 192.168/16"
block drop in log quick on em0 inet6 from fc00::/7 to any label "Block ULA networks from WAN block fc00::/7"
block drop in log on ! em1 inet from 192.168.5.0/24 to any
block drop in log inet from 192.168.5.1 to any
block drop in log on em1 inet6 from fe80::2e0:67ff:fe18:1979 to any
pass in quick on em1 inet proto udp from any port = bootpc to 255.255.255.255 port = bootps keep state label "allow access to DHCP server"
pass in quick on em1 inet proto udp from any port = bootpc to 192.168.5.1 port = bootps keep state label "allow access to DHCP server"
pass out quick on em1 inet proto udp from 192.168.5.1 port = bootps to any port = bootpc keep state label "allow access to DHCP server"
block drop in log on ! em1.10 inet from 10.1.10.0/24 to any
block drop in log inet from 10.1.10.1 to any
block drop in log on em1.10 inet6 from fe80::2e0:67ff:fe18:1979 to any
pass in quick on em1.10 inet proto udp from any port = bootpc to 255.255.255.255 port = bootps keep state label "allow access to DHCP server"
pass in quick on em1.10 inet proto udp from any port = bootpc to 10.1.10.1 port = bootps keep state label "allow access to DHCP server"
pass out quick on em1.10 inet proto udp from 10.1.10.1 port = bootps to any port = bootpc keep state label "allow access to DHCP server"
block drop in log on ! em1.20 inet from 192.168.20.0/24 to any
block drop in log inet from 192.168.20.1 to any
block drop in log on em1.20 inet6 from fe80::2e0:67ff:fe18:1979 to any
pass in quick on em1.20 inet proto udp from any port = bootpc to 255.255.255.255 port = bootps keep state label "allow access to DHCP server"
pass in quick on em1.20 inet proto udp from any port = bootpc to 192.168.20.1 port = bootps keep state label "allow access to DHCP server"
pass out quick on em1.20 inet proto udp from 192.168.20.1 port = bootps to any port = bootpc keep state label "allow access to DHCP server"
block drop in log on ! ovpnc1 inet6 from fdda:d0d0:cafe:1196::/64 to any
block drop in log on ovpnc1 inet6 from fe80::2e0:67ff:fe18:1978 to any
block drop in log inet6 from fdda:d0d0:cafe:1196::1002 to any
block drop in log on ! ovpnc1 inet from 10.10.0.0/16 to any
block drop in log inet from 10.10.0.4 to any
pass in on lo0 inet all flags S/SA keep state label "pass IPv4 loopback"
pass out on lo0 inet all flags S/SA keep state label "pass IPv4 loopback"
pass out inet all flags S/SA keep state allow-opts label "let out anything IPv4 from firewall host itself"
pass out route-to (em0 24.229.245.1) inet from x.x.x.x to ! 24.229.245.0/24 flags S/SA keep state allow-opts label "let out anything from firewall host itself"
pass out route-to (ovpnc1 10.10.0.1) inet from 10.10.0.4 to ! 10.10.0.0/16 flags S/SA keep state allow-opts label "let out anything from firewall host itself"
pass out route-to (ovpnc1 fdda:d0d0:cafe:1196::) inet6 from fdda:d0d0:cafe:1196::1002 to ! fdda:d0d0:cafe:1196::/64 flags S/SA keep state allow-opts label "let out anything from firewall host itself"
pass in quick on em1 proto tcp from any to (em1) port = https flags S/SA keep state label "anti-lockout rule"
pass in quick on em1 proto tcp from any to (em1) port = http flags S/SA keep state label "anti-lockout rule"
pass in quick on em1 proto tcp from any to (em1) port = ssh flags S/SA keep state label "anti-lockout rule"
anchor "userrules/*" all
pass in quick on em0 reply-to (em0 24.229.245.1) inet from ! 24.229.245.0/24 to any flags S/SA keep state label "USER_RULE"
pass in quick on em1 inet proto tcp from any to 127.0.0.1 port = domain flags S/SA keep state label "USER_RULE: NAT Redirect DNS"
pass in quick on em1 inet proto udp from any to 127.0.0.1 port = domain keep state label "USER_RULE: NAT Redirect DNS"
pass in quick on em1 inet proto udp from any to ! 192.168.5.1 port = domain keep state label "USER_RULE: Allow DNS to LAN"
block return in quick on em1 inet proto udp from any to any port = domain label "USER_RULE: Block DNS to WAN"
pass in quick on em1 inet from 192.168.5.0/24 to any flags S/SA keep state label "USER_RULE: Default allow LAN to any rule"
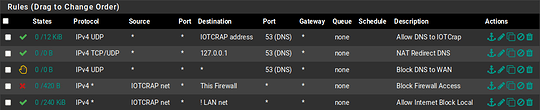
pass in quick on em1.10 inet proto udp from any to 10.1.10.1 port = domain keep state label "USER_RULE: Allow DNS to IOTCrap"
pass in quick on em1.10 inet proto tcp from any to 127.0.0.1 port = domain flags S/SA keep state label "USER_RULE: NAT Redirect DNS"
pass in quick on em1.10 inet proto udp from any to 127.0.0.1 port = domain keep state label "USER_RULE: NAT Redirect DNS"
block return in quick on em1.10 inet proto udp from any to any port = domain label "USER_RULE: Block DNS to WAN"
block drop in quick on em1.10 inet from 10.1.10.0/24 to (self) label "USER_RULE: Block Firewall Access"
pass in quick on em1.10 inet from 10.1.10.0/24 to ! 192.168.5.0/24 flags S/SA keep state label "USER_RULE: Allow Internet Block Local"
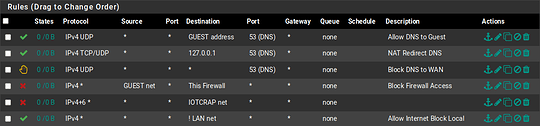
pass in quick on em1.20 inet proto udp from any to 192.168.20.1 port = domain keep state label "USER_RULE: Allow DNS to Guest"
pass in quick on em1.20 inet proto tcp from any to 127.0.0.1 port = domain flags S/SA keep state label "USER_RULE: NAT Redirect DNS"
pass in quick on em1.20 inet proto udp from any to 127.0.0.1 port = domain keep state label "USER_RULE: NAT Redirect DNS"
block return in quick on em1.20 inet proto udp from any to any port = domain label "USER_RULE: Block DNS to WAN"
block drop in quick on em1.20 inet from 10.1.10.0/24 to (self) label "USER_RULE: Block Firewall Access"
pass in quick on em1.20 inet proto tcp from any to ! 192.168.5.0/24 flags S/SA keep state label "USER_RULE: Allow Internet Block Local"
anchor "tftp-proxy/*" all
ALTQ:
queue qACK on em0 priority 6 priq( red ecn )
queue qDefault on em0 priority 3 priq( red ecn default )
queue qLink on em1 priority 2 qlimit 500 priq( red ecn default )
queue qACK on em1 priority 6 priq( red ecn )
STATES:
em0 udp 255.255.255.255:68 <- 10.15.24.1:67 NO_TRAFFIC:SINGLE
em0 icmp x.x.x.x:46144 -> 24.229.245.1:46144 0:0
ovpnc1 icmp 10.10.0.4:46566 -> 10.10.0.1:46566 0:0
em0 udp x.x.x.x:40452 -> 193.148.18.226:1196 MULTIPLE:MULTIPLE
em0 tcp x.x.x.x:888 <- 193.32.163.111:58898 CLOSED:SYN_SENT
em0 tcp x.x.x.x:2801 <- 185.209.0.84:57629 CLOSED:SYN_SENT
em0 tcp x.x.x.x:8759 <- 185.216.140.252:44948 CLOSED:SYN_SENT
ovpnc1 udp 10.10.0.4:59343 -> 95.101.36.192:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:48398 -> 95.101.36.192:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:44579 -> 95.101.36.192:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:48917 -> 95.101.36.192:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:24127 -> 95.101.36.192:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:38986 -> 95.101.36.192:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:11555 -> 95.101.36.192:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:7685 -> 23.211.61.193:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:31433 -> 23.211.61.193:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:65085 -> 95.101.36.192:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:10272 -> 23.211.133.193:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:42825 -> 23.211.133.193:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:36817 -> 23.211.133.193:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:44708 -> 23.211.133.193:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:20390 -> 184.85.248.193:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:9019 -> 84.53.139.193:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:25791 -> 84.53.139.193:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:25181 -> 84.53.139.193:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:22127 -> 84.53.139.193:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:43200 -> 84.53.139.193:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:18621 -> 84.53.139.193:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:61198 -> 95.101.36.192:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:18258 -> 2.22.230.193:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:43684 -> 2.22.230.193:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:56907 -> 2.22.230.193:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:40117 -> 2.22.230.193:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:22438 -> 2.22.230.193:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:56029 -> 2.22.230.193:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:10755 -> 184.26.160.193:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:28654 -> 23.74.25.192:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:41809 -> 184.85.248.193:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:28591 -> 23.211.133.192:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:51123 -> 23.211.133.192:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:14945 -> 23.211.133.192:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:21417 -> 96.7.49.193:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:16928 -> 96.7.49.193:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:48314 -> 96.7.49.193:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:61723 -> 2.22.230.193:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:57238 -> 193.108.88.1:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:50677 -> 23.74.25.192:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:49701 -> 23.55.235.68:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:59403 -> 23.192.125.86:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:22946 -> 23.38.171.183:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:58523 -> 23.55.235.68:53 MULTIPLE:SINGLE
ovpnc1 udp 10.10.0.4:59742 -> 23.55.235.87:53 MULTIPLE:SINGLE
em1 udp 192.168.5.1:53 -> 192.168.5.106:21491 SINGLE:NO_TRAFFIC
em1 udp 192.168.5.1:53 -> 192.168.5.106:65204 SINGLE:NO_TRAFFIC
ovpnc1 udp x.x.x.x:123 -> 208.79.89.249:123 MULTIPLE:SINGLE
ovpnc1 udp x.x.x.x:123 -> 171.66.97.126:123 MULTIPLE:SINGLE
ovpnc1 udp x.x.x.x:123 -> 162.159.200.123:123 MULTIPLE:SINGLE
em1 udp 185.217.69.122:1302 <- 192.168.5.101:56349 MULTIPLE:MULTIPLE
ovpnc1 udp 10.10.0.4:13365 (192.168.5.101:56349) -> 185.217.69.122:1302 MULTIPLE:MULTIPLE
em1 udp 192.168.5.255:32412 <- 192.168.5.101:35891 NO_TRAFFIC:SINGLE
em1 udp 192.168.5.255:32414 <- 192.168.5.101:34288 NO_TRAFFIC:SINGLE
em1 udp 192.168.49.255:137 <- 192.168.5.105:34450 NO_TRAFFIC:SINGLE
ovpnc1 udp 10.10.0.4:19730 (192.168.5.105:34450) -> 192.168.49.255:137 SINGLE:NO_TRAFFIC
em1 udp 192.168.5.255:32412 <- 192.168.5.105:51202 NO_TRAFFIC:SINGLE
em1 udp 192.168.5.255:32414 <- 192.168.5.105:52185 NO_TRAFFIC:SINGLE
em1 tcp 173.194.204.188:5228 <- 192.168.5.105:42230 ESTABLISHED:ESTABLISHED
ovpnc1 tcp 10.10.0.4:52498 (192.168.5.105:42230) -> 173.194.204.188:5228 ESTABLISHED:ESTABLISHED
em1 tcp 45.79.197.58:443 <- 192.168.5.105:58362 ESTABLISHED:ESTABLISHED
ovpnc1 tcp 10.10.0.4:8009 (192.168.5.105:58362) -> 45.79.197.58:443 ESTABLISHED:ESTABLISHED
em1 tcp 45.79.197.58:443 <- 192.168.5.105:58364 ESTABLISHED:ESTABLISHED
ovpnc1 tcp 10.10.0.4:18425 (192.168.5.105:58364) -> 45.79.197.58:443 ESTABLISHED:ESTABLISHED
em1 tcp 192.168.5.1:443 <- 192.168.5.101:45738 ESTABLISHED:ESTABLISHED
em1 tcp 192.168.5.1:853 <- 192.168.5.105:55426 TIME_WAIT:TIME_WAIT
em1 tcp 172.217.12.202:443 <- 192.168.5.105:49218 ESTABLISHED:ESTABLISHED
ovpnc1 tcp 10.10.0.4:56761 (192.168.5.105:49218) -> 172.217.12.202:443 ESTABLISHED:ESTABLISHED
ovpnc1 tcp 10.10.0.4:60845 -> 162.208.119.41:443 TIME_WAIT:TIME_WAIT
ovpnc1 tcp 10.10.0.4:57015 -> 162.208.119.41:443 TIME_WAIT:TIME_WAIT
ovpnc1 tcp 10.10.0.4:57016 -> 162.208.119.41:443 TIME_WAIT:TIME_WAIT
ovpnc1 tcp 10.10.0.4:57017 -> 162.208.119.41:443 TIME_WAIT:TIME_WAIT
em1 udp 172.217.10.131:443 <- 192.168.5.105:38931 MULTIPLE:MULTIPLE
ovpnc1 udp 10.10.0.4:4135 (192.168.5.105:38931) -> 172.217.10.131:443 MULTIPLE:MULTIPLE
em1 udp 255.255.255.255:67 <- 0.0.0.0:68 NO_TRAFFIC:SINGLE
em1 udp 127.0.0.1:53 (193.138.218.74:53) <- 192.168.5.106:21491 NO_TRAFFIC:SINGLE
ovpnc1 udp 10.10.0.4:12720 -> 184.85.248.193:53 MULTIPLE:SINGLE
em1 udp 127.0.0.1:53 (10.8.0.1:53) <- 192.168.5.106:65204 NO_TRAFFIC:SINGLE
INFO:
Status: Enabled for 0 days 06:17:12 Debug: Urgent
Interface Stats for em1 IPv4 IPv6
Bytes In 165467802 0
Bytes Out 2550976393 0
Packets In
Passed 1188929 0
Blocked 111895 0
Packets Out
Passed 2302285 0
Blocked 55 0
State Table Total Rate
current entries 85
searches 11248578 497.0/s
inserts 76375 3.4/s
removals 76290 3.4/s
Counters
match 195930 8.7/s
bad-offset 0 0.0/s
fragment 20 0.0/s
short 28 0.0/s
normalize 0 0.0/s
memory 0 0.0/s
bad-timestamp 0 0.0/s
congestion 0 0.0/s
ip-option 0 0.0/s
proto-cksum 0 0.0/s
state-mismatch 1824 0.1/s
state-insert 15 0.0/s
state-limit 0 0.0/s
src-limit 0 0.0/s
synproxy 0 0.0/s
map-failed 0 0.0/s
LABEL COUNTERS:
pass IPv6 loopback 192407 0 0 0 0 0 0 0
pass IPv6 loopback 87 8 392 4 196 4 196 0
Block all IPv6 192239 0 0 0 0 0 0 0
Block all IPv6 60105 1904 148490 0 0 1904 148490 0
Block IPv4 link-local 190496 0 0 0 0 0 0 0
Block IPv4 link-local 132216 0 0 0 0 0 0 0
Default deny rule IPv4 132216 868 133648 868 133648 0 0 0
Default deny rule IPv4 190498 526 128494 0 0 526 128494 0
Default deny rule IPv6 190486 0 0 0 0 0 0 0
Default deny rule IPv6 58280 0 0 0 0 0 0 0
Block traffic from port 0 190491 0 0 0 0 0 0 0
Block traffic from port 0 190043 0 0 0 0 0 0 0
Block traffic to port 0 190491 0 0 0 0 0 0 0
Block traffic to port 0 190045 0 0 0 0 0 0 0
Block snort2c hosts 190488 0 0 0 0 0 0 0
Block snort2c hosts 190497 0 0 0 0 0 0 0
sshguard 190488 3786 220010 3786 220010 0 0 0
GUI Lockout 0 0 0 0 0 0 0 0
virusprot overload table 129379 0 0 0 0 0 0 0
allow dhcp client out WAN 128430 2742 1023204 2742 1023204 0 0 0
allow dhcp client out WAN 58345 0 0 0 0 0 0 0
block bogon IPv4 networks from WAN 6963 0 0 0 0 0 0 0
Block private networks from WAN block 10/8 1594 0 0 0 0 0 0 0
Block private networks from WAN block 127/8 1594 0 0 0 0 0 0 0
Block private networks from WAN block 172.16/12 1594 0 0 0 0 0 0 0
Block private networks from WAN block 192.168/16 1594 0 0 0 0 0 0 0
Block ULA networks from WAN block fc00::/7 1594 0 0 0 0 0 0 0
allow access to DHCP server 125911 65 21942 65 21942 0 0 3
allow access to DHCP server 29 58 19348 29 9780 29 9568 3
allow access to DHCP server 182735 0 0 0 0 0 0 0
allow access to DHCP server 694 6 3456 6 3456 0 0 0
allow access to DHCP server 2 4 1808 2 1152 2 656 0
allow access to DHCP server 58947 0 0 0 0 0 0 0
allow access to DHCP server 0 0 0 0 0 0 0 0
allow access to DHCP server 0 0 0 0 0 0 0 0
allow access to DHCP server 58286 0 0 0 0 0 0 0
pass IPv4 loopback 127551 120 9002 60 3940 60 5062 10
pass IPv4 loopback 55365 0 0 0 0 0 0 0
let out anything IPv4 from firewall host itself 182801 53125 1630961 26375 779598 26750 851363 325
let out anything from firewall host itself 55946 5924 1186597 2416 865308 3508 321289 81
let out anything from firewall host itself 46705 2885239 2251680900 1937923 2133884766 947316 117796134 1334
let out anything from firewall host itself 46726 0 0 0 0 0 0 0
anti-lockout rule 189906 15931 8862322 6368 648660 9563 8213662 2
anti-lockout rule 187207 15456 8636691 6168 626626 9288 8010065 0
anti-lockout rule 187207 15456 8636691 6168 626626 9288 8010065 0
USER_RULE 189915 2181 212101 1628 138265 553 73836 96
USER_RULE: NAT Redirect DNS 5617 0 0 0 0 0 0 0
USER_RULE: NAT Redirect DNS 3795 367 26772 367 26772 0 0 310
USER_RULE: Allow DNS to LAN 10920 98 7102 94 6799 4 303 0
USER_RULE: Block DNS to WAN 111811 111515 7920887 111515 7920887 0 0 0
USER_RULE: Default allow LAN to any rule 2156 2902412 2287723961 947481 121088155 1954931 2166635806 86
USER_RULE: Allow DNS to IOTCrap 56639 0 0 0 0 0 0 0
USER_RULE: NAT Redirect DNS 481 0 0 0 0 0 0 0
USER_RULE: NAT Redirect DNS 481 24 1608 24 1608 0 0 3
USER_RULE: Block DNS to WAN 660 660 43425 660 43425 0 0 0
USER_RULE: Block Firewall Access 24 24 2016 24 2016 0 0 0
USER_RULE: Allow Internet Block Local 0 0 0 0 0 0 0 0
USER_RULE: Allow DNS to Guest 55948 0 0 0 0 0 0 0
USER_RULE: NAT Redirect DNS 478 0 0 0 0 0 0 0
USER_RULE: NAT Redirect DNS 478 0 0 0 0 0 0 0
USER_RULE: Block DNS to WAN 0 0 0 0 0 0 0 0
USER_RULE: Block Firewall Access 0 0 0 0 0 0 0 0
USER_RULE: Allow Internet Block Local 0 0 0 0 0 0 0 0
TIMEOUTS:
tcp.first 120s
tcp.opening 30s
tcp.established 86400s
tcp.closing 900s
tcp.finwait 45s
tcp.closed 90s
tcp.tsdiff 30s
udp.first 60s
udp.single 30s
udp.multiple 60s
icmp.first 20s
icmp.error 10s
other.first 60s
other.single 30s
other.multiple 60s
frag 30s
interval 10s
adaptive.start 237600 states
adaptive.end 475200 states
src.track 0s
LIMITS:
states hard limit 396000
src-nodes hard limit 396000
frags hard limit 5000
table-entries hard limit 400000
TABLES:
bogons
snort2c
sshguard
virusprot
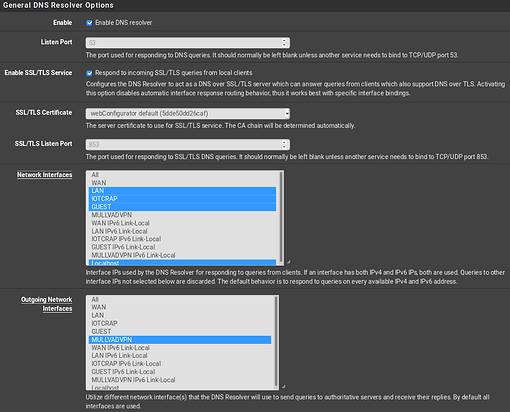
I have the VLANs set up on both pfSense and Unifi, ensuring the VLAN tags match, but I still get ‘DNS Timeout’ issues on all my wireless devices, not on LAN.
Any help?