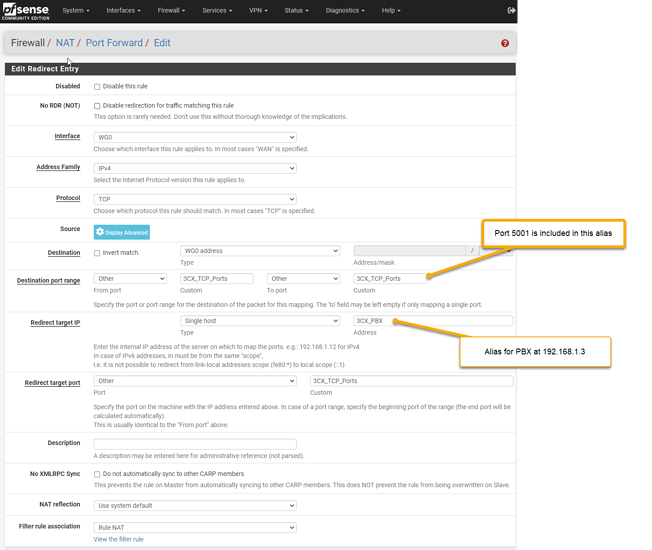
This outgoing NAT over wg0 is good, lots of people do similar hairpin NAT setups, just be warned that it’s a big hammer…
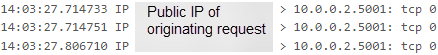
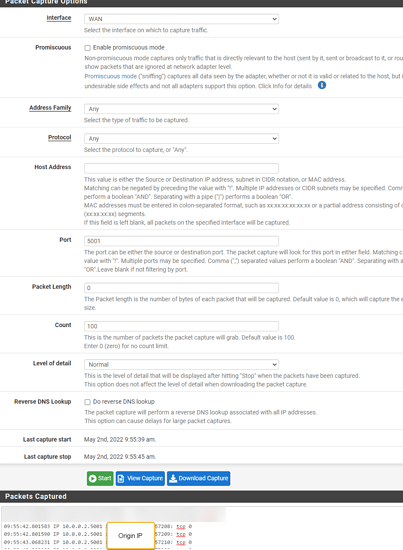
… the issue is that it becomes impossible to differentiate clients based on source IP… to Plex they’ll all look like they’re coming from Linode’s wg0 IP.
Depending on how security concious you happen to be…this might or might not matter to you.
On the other hand, not doing this NAT, …
… while it may not bring you additional security by itself, provides the Plex host with one more piece of information (IP address) that can be used to differentiate clients and maybe do some additional firewalling or filtering in the future, should you choose to do so, in the future.
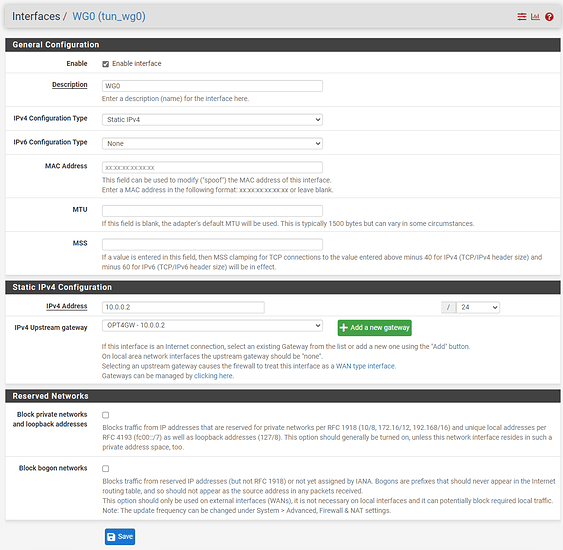
You can set Allowed IPs to 0/0 on both sides, and disabling all NAT-ing on either router on either side of the Wireguard link (with exception of your ISP interface), and just setting a static route on Linode to tell it to talk to your pfSense for your LAN IPs, it might be a bit better than what you have now with the hairpin (-ish) NAT over wg0. Security wise it’s about the same.
To reiterate, nothing wrong with your current setup, just a bit complex, maybe harder to secure.