You need to hide the hypervisor from windows.
try this in your conf file:
args: -cpu host,kvm=off
vga: none
You need to hide the hypervisor from windows.
try this in your conf file:
args: -cpu host,kvm=off
vga: none
By conf file, you mean /etc/pve/qemu-server/<vm-id>.conf?
Yep
8characters
So if I have this in there:
args: -cpu host,kvm=off
vga: none
Do I need this?
cpu: host
I would assume CPU is redundant?
Edit:
Hmm, the VM started fine, but nothing is being output to my physical displays.
And now I can’t stop the VM due to “unexpected status”.
Time to reboot the host.
It is redundant.
Do you have:
bios: ovmf
in there?
Here is the whole config file for the VM:
bios: ovmf
bootdisk: virtio0
cores: 4
cpu: host
args: kvm=off
efidisk0: local-lvm:vm-100-disk-2,size=128K
hostpci0: 02:00,x-vga=on
machine: q35
memory: 7168
name: Test-Windows
net0: virtio=96:24:CF:B4:AA:A2,bridge=vmbr0
numa: 0
onboot: 1
ostype: win10
scsihw: virtio-scsi-pci
smbios1: uuid=f675c872-c390-4668-9c48-423f5b4ff239
snaptime: 1509639761
sockets: 1
usb0: host=6-1.2
usb1: host=2-4
usb2: host=3-1.2.3.4
usb3: host=1-1.2.3.4
virtio0: local-lvm:vm-100-disk-1,cache=writeback,size=90G
The device on the host machine is 02:00, and is definitely loading the vfio-pci (should this be vfio-vga?)
root@pve-001:~# dmesg | grep -e IOMMU
[ 0.615425] AMD-Vi: IOMMU performance counters supported
[ 0.617069] AMD-Vi: Found IOMMU at 0000:00:00.2 cap 0x40
[ 0.618547] perf/amd_iommu: Detected AMD IOMMU #0 (2 banks, 4 counters/bank).
root@pve-001:~# find /sys/kernel/iommu_groups/ -type l
/sys/kernel/iommu_groups/7/devices/0000:00:13.2
/sys/kernel/iommu_groups/7/devices/0000:00:13.0
/sys/kernel/iommu_groups/5/devices/0000:00:11.0
/sys/kernel/iommu_groups/3/devices/0000:00:09.0
/sys/kernel/iommu_groups/11/devices/0000:00:15.2
/sys/kernel/iommu_groups/11/devices/0000:00:15.0
/sys/kernel/iommu_groups/11/devices/0000:05:00.0
/sys/kernel/iommu_groups/1/devices/0000:00:03.0
/sys/kernel/iommu_groups/1/devices/0000:02:00.1
/sys/kernel/iommu_groups/1/devices/0000:00:03.1
/sys/kernel/iommu_groups/1/devices/0000:02:00.0
/sys/kernel/iommu_groups/8/devices/0000:00:14.2
/sys/kernel/iommu_groups/8/devices/0000:00:14.0
/sys/kernel/iommu_groups/8/devices/0000:00:14.3
/sys/kernel/iommu_groups/6/devices/0000:00:12.2
/sys/kernel/iommu_groups/6/devices/0000:00:12.0
/sys/kernel/iommu_groups/4/devices/0000:00:10.0
/sys/kernel/iommu_groups/12/devices/0000:00:18.4
/sys/kernel/iommu_groups/12/devices/0000:00:18.2
/sys/kernel/iommu_groups/12/devices/0000:00:18.0
/sys/kernel/iommu_groups/12/devices/0000:00:18.5
/sys/kernel/iommu_groups/12/devices/0000:00:18.3
/sys/kernel/iommu_groups/12/devices/0000:00:18.1
/sys/kernel/iommu_groups/2/devices/0000:00:08.0
/sys/kernel/iommu_groups/10/devices/0000:00:14.5
/sys/kernel/iommu_groups/0/devices/0000:00:02.2
/sys/kernel/iommu_groups/0/devices/0000:00:02.0
/sys/kernel/iommu_groups/0/devices/0000:01:00.0
/sys/kernel/iommu_groups/9/devices/0000:00:14.4
root@pve-001:~# lspci -k
02:00.0 VGA compatible controller: NVIDIA Corporation GK208B [GeForce GT 710] (rev a1)
Subsystem: eVga.com. Corp. GK208 [GeForce GT 710B]
Kernel driver in use: vfio-pci
Kernel modules: nvidiafb, nouveau
Your IOMMU groups are problematic.
/sys/kernel/iommu_groups/1/devices/0000:00:03.0
/sys/kernel/iommu_groups/1/devices/0000:02:00.1
/sys/kernel/iommu_groups/1/devices/0000:00:03.1
/sys/kernel/iommu_groups/1/devices/0000:02:00.0
Whatever 00:03.0 and 00:03.1 are, you’re going to need to separate them in order to get the GPU to pass properly.
You will also need to pass 02:00.1 as well. I’m not sure if proxmox automatically detects the .1 and passes it as well, but that could cause a problem.
That is a valid point. I didn’t notice that. I’ll have to see what those are.
I believe that’s safe.
If you have a multi-function device (like a vga card with embedded audio chipset),
you can pass all functions manually with
hostpci0: 01:00.0;01:00.1
orto pass all functions automatically
hostpci0: 01:00
Perfect. I’m not too familiar with proxmox passthrough, just trying my best here. 
I definitely appreciate the help. 
00:03.0 Host bridge: Advanced Micro Devices, Inc. [AMD] Device 157b
00:03.1 PCI bridge: Advanced Micro Devices, Inc. [AMD] Device 157c
There are 10 Host bridges and 2 PCI Bridges.
I assume this PCI Bridge is the same bridge that the GPU is plugged into?
What motherboard are you using? Is this an AM4 board?
It’s at work, so older hardware. FM2 socket. The Athlon X4 in it does support virtualization, and IOMMU (seemingly as I have gotten the GT 710 to appear in the Windows VM).
There are 2 PCI-e slots on the board (x16 and x1), so since 2 are listed when I do lspci I imagine those relate somehow.
Ah, this might be problematic then. The ACS override patch will probably help you here.
This thread can guide you through compiling the ACS override patch into the kernel:
I hesitate to suggest this because it causes bugs sometimes, but since there isn’t a different PCIe slot you can put the GPU in, it’s the only real option.
yeah, this is the PCI bridge. I wonder if passing that through as well would result in instability. If you do pass that stuff through as well, make sure they’re hostpci0 and the gpu is hostpci1
Yeah… that’s kinda what I’m wondering. I would have originally assume this would be beneficial. :S
Give it a go.

kvm: -k en-us: Could not open 'kvm=off': No such file or directory
hostpci0: 02:00,x-vga=on,pcie=1
args: kvm=off
bios: ovmf
Edit:
Oh, I see. That’s supposed to be on the CPU settings with host.
Edit 2:
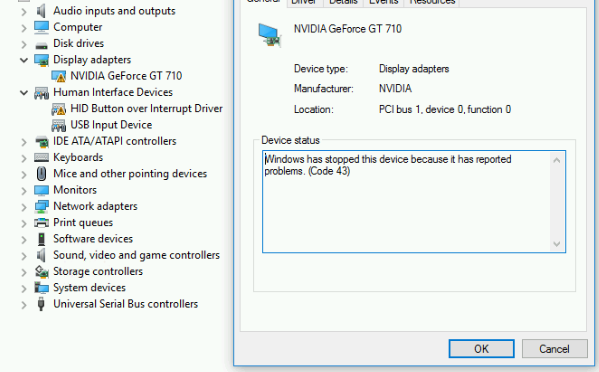
I’m still getting this issue. Research tells me it is the Nvidia drivers not wanting to work in a Hypervisor. I’ve tried the three suggested solutions of having these three CPU options specified: host,kvm=off,hidden=1
Not sure what else to do. I’ve found that more recent drivers use more strict verification, but still. There’s gotta be a way.
Can you post your current conf file?
There is a way, I’ve got it working with the latest drivers on a 660 ti with an arch host. I just don’t know what the exact options for proxmox are…
This proxmox thread may be of assistance.
Sweet. These options are for QEMU KVM so whatever yours is should be the same presuming you’re using that.
hostpci0: 02:00,x-vga=on,pcie=1
bios: ovmf
bootdisk: virtio0
cores: 4 cpu: host,hidden=1,kvm=off
efidisk0: local-lvm:vm-100-disk-2,size=128K
machine: q35
memory: 7168
name: Test-Windows
net0: virtio=96:24:CF:B4:AA:A2,bridge=vmbr0
numa: 0 ostype: win10
scsihw: virtio-scsi-pci
smbios1: uuid=f675c872-c390-4668-9c48-423f5b4ff239
sockets: 1
usb0: host=6-1.2
usb1: host=2-4
usb2: host=3-1.2.3.4
usb3: host=1-1.2.3.4
virtio0: local-lvm:vm-100-disk-1,cache=writeback,size=90G
Have you tried adding cpu: host,kvm=off?
So somehow, that got deleted when I copy/pasted. Using ProxMox’s noVNC doesn’t let clipboards sync, so they have a menu option to be able to copy/paste the contents, but this uses spaces instead of newlines, so to get it to work in a readable format here, I have to manually swap those out. Must’ve deleted that line while doing so.
bootdisk: virtio0
cores: 4
cpu: host,hidden=1,kvm=off
efidisk0: local-lvm:vm-100-disk-2,size=128K
machine: q35
That’s where it is in the conf. Let me try without hidden=1. Maybe combining all 3 is not good?