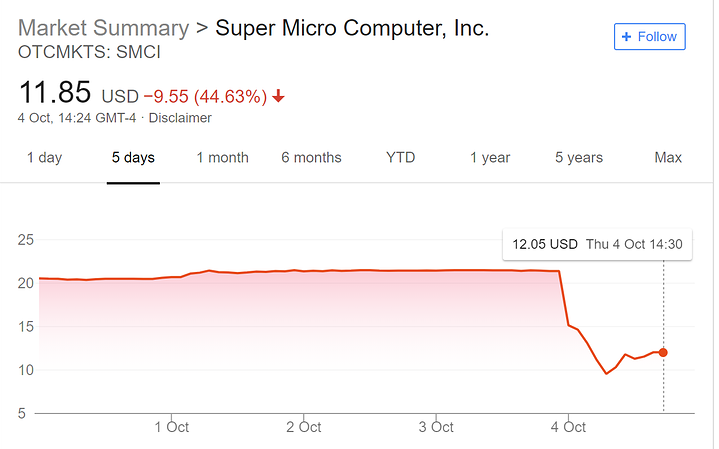
cough Petrobras cough
Thanks to components such as Intel’s AMT/ME, this type of attack is easy for a state actor to pull off. Since we’re not allowed to know what the ME is doing, we have no way to know when it is misbehaving. Thankfully, someone with a sharp eye caught these bugged servers periodically phoning home.
It’s owned by the Brazilian government, not a private enterprise.
I think you’re a bit optimistic with how adherent the NSA is willing to be to that fine line; for context, this was an intercept made on a package from Houston, Texas to Mexico:
Admittedly, this was probably a foreign researcher, but I would be curious where NSA draws the line. Are international packages to USA citizens fair game? Are domestic packages to foreign nationals?
For context, I assume you’re talking about this:
Anyway, we’re getting a bit off-topic here, since neither is even a hardware compromise.
No, put plainly the target of their investigation can’t be a US citizen. The NSA has no mandate inside the US at all. The FBI does, but it needs a warrant due to the 4th amendment. There have been tons of abuses and pushing the line on that stuff, primarily exposed by Edward Snowden, but that all applies to SIGINT, not actively compromising hardware or a supply chain.
At least, as far as we know.
We have been getting a bit off-topic, but it’s important to draw the line. Whataboutism doesn’t apply here. China, the nation-state, is stealing intellectual property. It is performing industrial espionage to help Chinese companies, all of which have ties to the state. They restrict foreign businesses from entering the Chinese market unless they give up control of their technology, services, and financials. They are truly bad actors and really can’t be compared to anyone else.
They need to stop doing that stuff. Maybe the tariffs will do that. I don’t have a lot of faith given the admin that’s applying them, but if they get China to open their market and stop stealing IP that would be a great thing. The trans-pacific partnership would have been just as effective and less risky, but that’s gone now.
TPP had a lot of insane legalese and bizarre corporate immunity IIRC, that’s why most people I talked to opposed it.
Anyway, I don’t really see any safe way to manufacture chips or motherboards in the PRC-controlled mainland, this sort of stuff can and will happen. What I would be interested in, is whether agencies like DARPA would consider board/chip manufacture in ROC-controlled Tawain or Singapore to be safe enough.
Obviously, especially if you are the USA government, manufacture domestically, by domestically-owned companies is probably preferred, but companies like GlobalFoundries might manufacture domestically while being financially owned by an Abu Dhabi sovereign wealth fund. Is that better or worse than a German company manufacturing in Germany?
As an example, with IBM shifting chip manufacturing to Samsung, will future USA supercomputers have their chips manufactured in Korea?
China really isn’t in power in Taiwan and Singapore, unlike Hong Kong. So sure. Note Taiwan was not tariffed, either.
i’m pretty curios whats coming out of this.
If more are dropping Supermicro servers ans such.
Or what those litlle spy chips actually are, how they work etc, and how to identfy them.
Would like to know if my SM. boards have them and if i can remove them.
From the animation they did, it looked like it was coupled to the spi Rom for the bios and rom. But thats just a nice animation and not real reference.
Oh yes, I expect there will be a lot of information coming out with HOWTO guides to find out if your hardware is compromised. But the article also said that some of the more sophisticated ones were so tiny that they were slipped between layers in the PCB, and you’re realistically never gonna find that.
Hopefully they find some sort of communication commonality which can be picked up by NIDS. That’s probably the best solution.
One of the articles that I read said that some of the spy chips were sandwiched between the layers of the PCB. So, visually spotting those would be nearly impossible.
Theoretically, one could X-ray the board and look for a shadow on the X-ray image, that has no matching surface component. Not sure how well that would work in practice though.
Of course you can find it with sufficient effort, but it’s cheaper and easier to toss the hardware in the garbage.
The real problem is making sure, that whatever you buy to replace the compromised HW, does not get compromised in a similar way. How does one make sure the HW can be trusted?
Build it yourself.
You hire people with the relevant competence and check the hardware. Companies like Amazon, Apple etc has done this for a pretty long time.
Strongly worded denial from Amazon.
Interesting, that is a bit longer than Amazon’s response to Bloomberg, as linked by @mutation666:
Here is an interview with one of the reporters, Jordan Robertson:
An interesting thread on Twitter with Trammell Hudson (developer of Heads), with some speculation as to where the chip could be hiding:
qrs (Trammel Hudson)
Allegedly a supply chain attack on Supermicro’s servers installed small CPUs disguised as passive capacitors on the mainboard that were able to take over the BMC, which could then compromise the main CPU:
(links to Bloomberg article)The BMC is vastly over-privileged and tied into so many parts of the system. Securing it is vital to secure the root of trust, and open source firmware like OpenBMC and u-BMC are good first steps to trusting it.
csirac2
Not capacitors though; article says signal conditioning ICs, of which I’m only vaguely familiar with motor controller variants unlike anything a motherboard would have, but do SPI for legit reasons in that space… could hide on path of SMBus sensor? Cf.
(link about Intel Management engine talking over SMBus while CPU is asleep)
qrs
You’re right that Bloomberg doesn’t identify the component beyond “signal conditioning”. Another place where an attack could reside is in the SPI bus multiplexer since that would allow malicious firmware to be delivered to the x86 from the flash chip.
https://pbs.twimg.com/media/DorHfBaXsAApRWL.jpg:large
Serve The Home has an article up:
I didn’t think of the SATADOM, but as he says in the article, host based encryption would make it unlikely. Everything I’ve seen so far point to a BMC hack. And that is nothing new really.
Bottom line, if this Supermicro attack vector is to the BMC, then the Bloomberg story is no bigger than the Dell EMC PowerEdge iDRACula story or any others. Saying there is a vulnerability in a BMC is like saying the sun is hot.
STH also point out the strange part with the Bloomberg article, why would the FBI etc wait years if they suspected something like this? Why are the US military still using Supermicro hardware? Stuff doesn’t add up.
Everyone involved denying everything, and specifically this part of Apple’s response makes me think that the piece was a hit-piece on Super Micro, more than anything. No clear reason for it, though.
Over the course of the past year, Bloomberg has contacted us multiple times with claims, sometimes vague and sometimes elaborate, of an alleged security incident at Apple. Each time, we have conducted rigorous internal investigations based on their inquiries and each time we have found absolutely no evidence to support any of them.
Ouch.
The Bloomberg article specifically says that the implant is connected to the BMC:
Since the implants were small, the amount of code they contained was small as well. But they were capable of doing two very important things: telling the device to communicate with one of several anonymous computers elsewhere on the internet that were loaded with more complex code; and preparing the device’s operating system to accept this new code. The illicit chips could do all this because they were connected to the baseboard management controller, a kind of superchip that administrators use to remotely log in to problematic servers, giving them access to the most sensitive code even on machines that have crashed or are turned off.