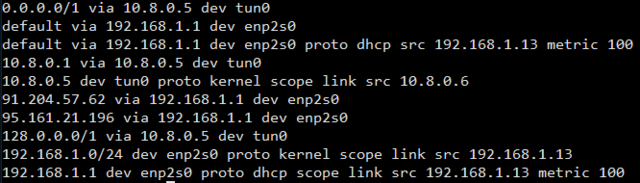
I know it’s a bit of a mess, I can’t seem to find the complete setup script i wrote, just the bits and pieces from before i did the final setup. Think it’s still on my old router, which is in a box somewhere around the house.
However, you’ll at least have a few of the basics to work from, and hopefully it’ll help you get your setup up and running. Everything below is from a router setup, where things were hosted on my lan, so some adaptation will be required.
If you lock yourself out because of iptables, just do a reboot, you have to actively make iptables and route persistent or load it during startup in rc.local or setup a system service to load your settings everytime you reboot.
I’m nipping to Italy on an extended weekend, and won’t be online until start next week, so if something, I won’t be able to answer much till then.
I added these to my VPN client profiles to make sure no route was added, so I could setup my own
route-nopull
dev tun0
You’ll need to enable fwmarks and forwarding, if I recall correctly, a reboot is required after setting the following two. It’s also possible to “echo 1 > /some/long/ass/path/to/nowhere” which doesn’t require a reboot. Someone else here will know if you want to do it that way,
sysctl -w net.ipv4.tcp_fwmark_accept=1
sysctl -w net.ipv4.ip_forward=1
You’d need to have the main table routes in your new “public access” table, used to route back from your server through your wan interface.
wan_gw = the gateway wan interface uses
#ip route flush table 100
ip route show table main | grep -Ev ^default | grep -Ev linkdown | grep -Ev tun | while read r ; do ip route add table 100 $r ; done
ip route add table 100 default via $wan_gw
ip rule add fwmark 100 lookup 100
Saves and restores fwmarks, this one is required for fwmarks to function, makes sure that previously marked packets get remarked if needed, and also makes sure that new ones coming in are marked for their return back out.
iptables -t mangle -A PREROUTING -j CONNMARK --restore-mark
iptables -t mangle -A PREROUTING -m mark ! --mark 0 -j ACCEPT
iptables -t mangle -A POSTROUTING -j CONNMARK --save-mark
An example for how I redirected traffic to my server and back out wan interface. The first three lines are general and not port related If the server that does the routing also hosts the services, I would think you’d have to use INPUT and OUTPUT iptables chain.
(Someone correct me if I’m wrong please).
srv_ip = ip of lan server
wan_ip = public ip adddress
wan_if = wan interface (enp2s0)
lan_if = interface for lan (br0)
iptables -t nat -A PREROUTING -i $wan_if -m mark --mark 100 -j DNAT --to $srv_ip # incoming to server
iptables -t nat -A POSTROUTING -o $wan_if -m mark --mark 100 -j SNAT --to $wan_ip # outgoing from server
iptables -t nat -A POSTROUTING -o $lan_if -j MASQUERADE
These are required for the specific ports/services. Sets a mark on new tcp connections from wan
iptables -A PREROUTING -t mangle -i $wan_if -p tcp -m state --state NEW -j MARK --set-mark 100
iptables -A FORWARD -d $srv_ip -p tcp --dport 80 -m mark --mark 100 -j ACCEPT # inc - HTTP on $srv_ip
iptables -A FORWARD -s $srv_ip -p tcp --sport 80 -m mark --mark 100 -j ACCEPT # out - HTTP on $srv_ip
used this piece to setup routes on specific tables for each vpn connection. It doesn’t have to be a loop if you only have one vpn connection just replace the “for f in…” line with “f=/path/to/your_vpn_file.conf” and remove the “done” in the end
for f in /etc/openvpn/*.conf; do
iface=$(cat $f | grep dev | awk -F' ' '{ print $2 }')
if [ -d /sys/class/net/$iface ]; then
# log "Setting up $iface routes"
tun_srv=$(cat $f | grep remote | grep -v random | awk -F' ' '{print $2}' | nslookup | tail -n 4 | head -n 1 | awk -F' ' '{print $2"/32"}')
tun_net=$(ip a s $iface | grep peer | awk -F' ' '{print $4}' | awk -F'/' '{print $1}')
tun_gw_net=$(echo $tun_net | awk -F'.' '{print $1"."$2"."$3".1/32"}')
tun_gw=$(echo $tun_net | awk -F'.' '{print $1"."$2"."$3".1"}')
tun_ip=$(ip a s $iface | grep peer | awk -F' ' '{print $2}' | head -n 1)
tun_tbl=$(cat /etc/iproute2/rt_tables | grep $iface | awk -F' ' '{print $1}')
ip route add $tun_srv via $wan_gw # table $tun_tbl
ip route add 0.0.0.0/1 via $tun_net # table $tun_tbl
ip route add 128.0.0.0/1 via $tun_net # table $tun_tbl
ip route add $tun_gw_net via $tun_net # table $tun_tbl
#ip route show table main | grep -Ev ^default | grep -Ev linkdown | while read r ; do ip route add table $tun_tbl $r ; done
fi
done
I was really happy to have this one enabled, helps a great deal when you’re debugging.
if [ $ipt_log_enabled -eq 1 ]; then
iptables -N INPUT_LOG
iptables -N OUTPUT_LOG
iptables -N FORWARD_LOG
iptables -A INPUT -j INPUT_LOG
iptables -A OUTPUT -j OUTPUT_LOG
iptables -A FORWARD -j FORWARD_LOG
iptables -A INPUT_LOG -m limit --limit 50/m -j LOG --log-prefix "ipt i_log: " --log-level 7
iptables -A OUTPUT_LOG -m limit --limit 50/m -j LOG --log-prefix "ipt o_log: " --log-level 7
iptables -A FORWARD_LOG -m limit --limit 50/m -j LOG --log-prefix "ipt f_log: " --log-level 7
iptables -A INPUT_LOG -j DROP
iptables -A OUTPUT_LOG -j DROP
iptables -A FORWARD_LOG -j DROP
fi