thank you thro and novasty.
I do not understand this:
If you can, virtualise two NAS instances on the single NAS, put dedicated NICs in for each virtual machine and split the networks with a firewall appliance.
Sounds too complicated.
I realize that there is no way to be perfectly safe from malware but let me stratify risk into two types:
a) the risk of getting malware when I am not doing anything-for example, some finds a vuln and drops a bad file onto the NAS, someone finds a loophole in a complicated design, or the design is misconfigured
b) the risk of getting malware while I am doing something-I surf to a bad site, download a bad file, connect to a bad machine.
Type b risk control requires virus scanners, playpens, etc.
Type a risk control requires intelligence in not making setup mistakes-leaving ports open, making complicated designs with unintended points of failure. Making VLANS requires rules on the router. A single typo, bit flip, attack, etc renders both groups vulnerable to type b problems.
Having a separate router for PRIVATE keeps that group insulated from failures,compromises,etc on the outer router or clients that it serves.
I suppose NAS could be in a third VLAN but since TEAM will be frequently accessing it and PRIVATE only occasionally accessing it, I put it in the TEAM group. The idea of putting PRIVATE behind a firewall box instead of a router box occurred to me-then everyone would be in the same private address space and going from PRIVATE to any TEAM would be easier.
The design I initially proposed, (with TEAM in the 10.0.0.0 net and PRIVATE in the 192.168.1.0 net) is something I have never done. In fact I am so noob, that I wouldnt know where to start. A simpleton solution would be to make TEAM 192.168.1.0 with subnet mask 255.255.255.0 and to make PRIVATE 192.168.2.0 with subnet mask 255.255.0.0. But maybe that has flaws I cannot see.
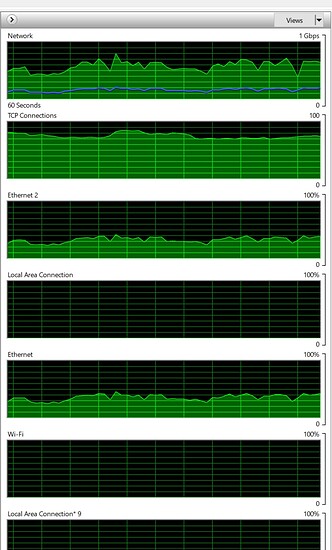
FYI, my current ISP is gigabit and I get 800mbps transfer speeds through the standard verizon box. Model Name:Fios-G1100
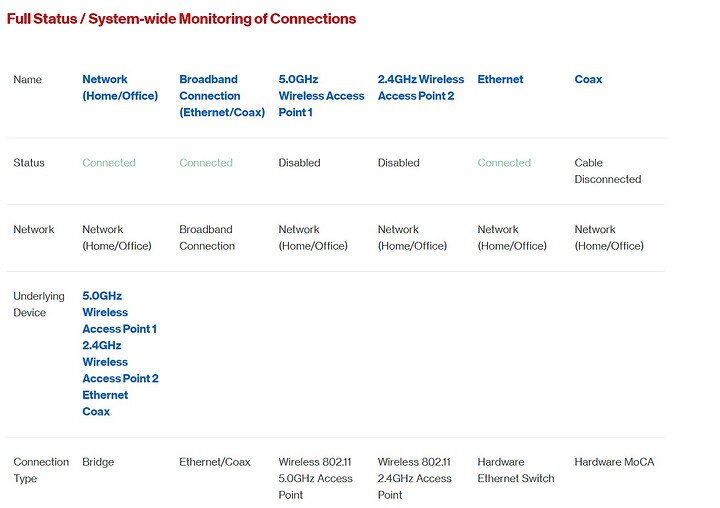
It looks like this:
transfer speeds look like this: