An open question to everyone, I thought it might be interesting.
What would you say is the biggest security related threat to organisations? (Bonus for including why)
An open question to everyone, I thought it might be interesting.
What would you say is the biggest security related threat to organisations? (Bonus for including why)
The people.
Reason: Literally yesterday the IT guy at work had to put in a filter for the word “masturbate” on our email server.
Disgruntled employees.
Hackers. Both lone wolves and gov organizations
Bad programming?
IT security: Users and outdated software. Especially older generation employees still use passwords like “password1”. Outdated software might not be because of bad IT dept, but rather bad organization management who won’t invest enough to keep IT infrastructure updated and secure.
General security: Ignoring guidelines and best practices (assuming these are up to date). Not only in IT, but in general ignoring rules and guidelines usually leads to problems. It might not happen today, or this year, but it will eventually.
I’d have to give a +1 for employees as well.
I can’t count how many times I’ve had teachers come up to me saying their browser keeps taking them to a different site. I got to look at it, and they’ve downloaded some browser extension or even some app from a random website and it’s re-directing everything they do through some search engine that I’ve never heard of. They don’t care to do the research, they just see “free PDF editor” and hop right on it.
Also had a few cases where people said they got an email from the superintendent about something, but it was from a weird email. These employees I trust because they saw that it was suspicious and weren’t scared to bring it up, but how many of them have had the same thing and fell for it?
+1 for disgruntled as well, and I’d like to throw in financial issues too. In the navy we had several briefs from the FBI about different situations where people had willfully given over classified information because they were either super pissed off or in deep financial trouble and were offered money by a foreign entity. Or sometimes they were fine but they just wanted the money.
Listening to a bunch of podcasts and audiobooks on hacking and whatnot, it seems like in many situations there is some employee who failed to recognize a threat, report suspicious behavior, etc. Some cases it might not stop the intruder, but it would have made their job a lot harder. Some cases may have prevented the breach from happening entirely.
You’ll have to add those podcasts and audiobooks to another post so the more curious can delve into them…
Funny you mention this
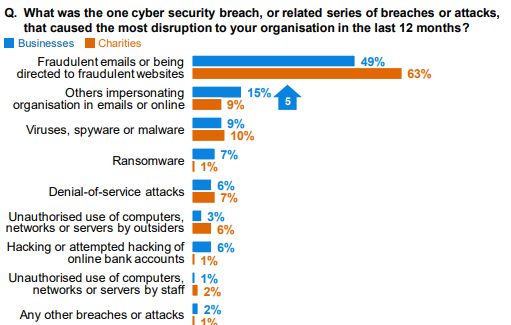

I’m thinking more along the lines of poor education, and failing to persuade employees about healthy digital practices and its importance.
I agree with some of the stats, phishing via email and similar methods seems to be the one of the most successful attack vectors, which almost always un-maliciously succeeds because of the human employee factor.
I don’t think id necessarily put the blame on employees so much as the company and security team for failing to properly education and give employees the right tools.
From personal experience, employee mis-judgement or neglect has been the reason something has gone wrong, in almost every case because of a phishing attempt.
We once had an invoice float around finance while they tried to find out who’s it was and why it was opening weird… while opening it on all their laptops.  They eventually figured it might not be legitimate.
They eventually figured it might not be legitimate.
But the amount of phishing attempts that make it through filters is quite high considering.
I do honestly think though that almost all employees can be given the tools and information not to fall for phishing attempts.
@Ruffalo @aLilBabyOtter disgruntled employees, before or after they are fired?
I like the practice of immediately removing employees from the building when their on notice for their job. Especially employees with any access to sensitive information. But i don’t know how common this really is as a problem?
Typically before, we learned our lesson there. SSO is very important, and not allowing anyone to go outside that using their own ghetto google docs or whatever.
Both are problems. Before may be an even bigger problem because they still have physical access.
And I agree with immediately removing employees. They are already going to have knowledge of some sensitive information, but it’s good to remove their physical access before they can acquire new sensitive information or equipment as soon as possible.
I’ve seen a lot of this not happening, and its a bit bazaar to me.
I’ve not seen a huge amount of issues with disgruntled employees in general though, however i think that can be minimised reasonably well with good access control, only what you need for as long as its required.
I think if i was to pick the top problem areas, disgruntled employees would be reasonably low on the list of risks as its most often than not extremely risky for the employee who could face civil court, fines, or prison time when caught. And more often than not it is when caught, not if, unless your company is completely incompetent.
Even issue of theft that i’ve dealt with before are almost impossible to get away with, once its identified it doesn’t usually take long to find out who did it, and its an immediate loss of your job, potential recovery of what you stole, and maybe the police involved.
So i think its a low risk issue, still and issue, i dont know if you agree with that assessment?
I think this is a problem, but id personally blame the company for this. Except where there is industry regulation requiring you follow ridiculous password rules, technology is sufficiently advanced that there’s almost no need for this kind of stuff. Good implementation of security should lead people to making secure passwords in the first place without rotating numbers or writing them on the screen because they cant remember it all.
The existence of the organization.
One of the biggest issues is the pure volume of attacks, threats and their corresponding alerts. Multiple avenues of attack, huge volumes of attacks, many disparate systems to try secure the different points of ingress and egress, and the pure volume of alerts that may not be accurate or relevant that an organisation has to deal with. Almost always accompanied by insufficient number of security staff to tackle such a volume.
Threats get buried in the noise and detection/remediation takes too long.
Thread closed as it was outside the guidelines for thread revival. Please PM me or another moderator if you feel the thread was closed in error. See the FAQ for more information.
Feel free to create a new thread if you wish to continue this thread’s conversation.